Category: Persecure
-

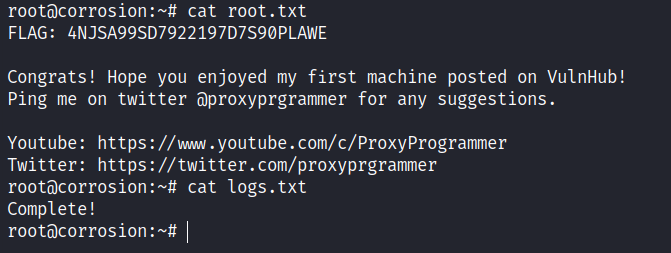
Hacktoria : The Killer Clown
Clues: Head to google map and search for parks near Northwest Berkeley. After some time browsing through the photos looking for rubbish bins I came across the exact bin in Ceda Rose Park Scroll into the location. We need to lookout for a location that is shaded and has a house nearby. The circled area…
-
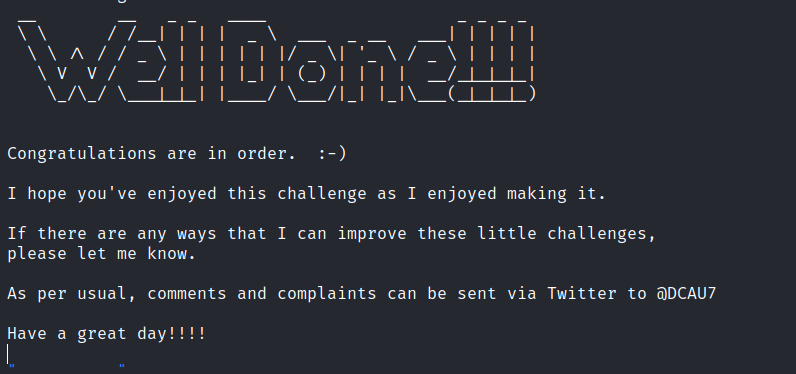
DC: 3.2
DC-3 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. As with the previous DC releases, this one is designed with beginners in mind, although this time around, there is only one flag, one entry point and no clues at all.
-
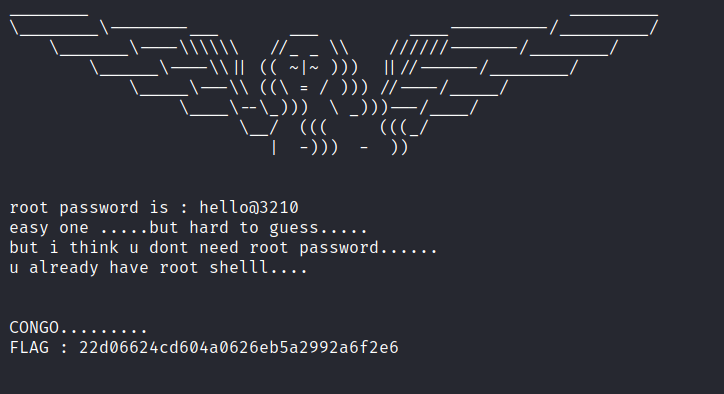
Dina: 1.0.1
Download the machine: https://www.vulnhub.com/entry/dina-101,200/ Overview Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 /robots.txt /nothing source code. /secure Unzip the file with the password list and a mp3 file is given. Use cyberchef to read the file. Now we found an interface. We…
-
Hacktoria : Intergalactic Warfare
Some clues we can get from the information given: The only “usual suspects” that I can think of is AREA 51. Let’s search for area 51 and look around the location. Found some cool planes. And even some choppers. Alright enough with sightseeing , we need to hunt for aliens. Just above AREA 51 we…
-
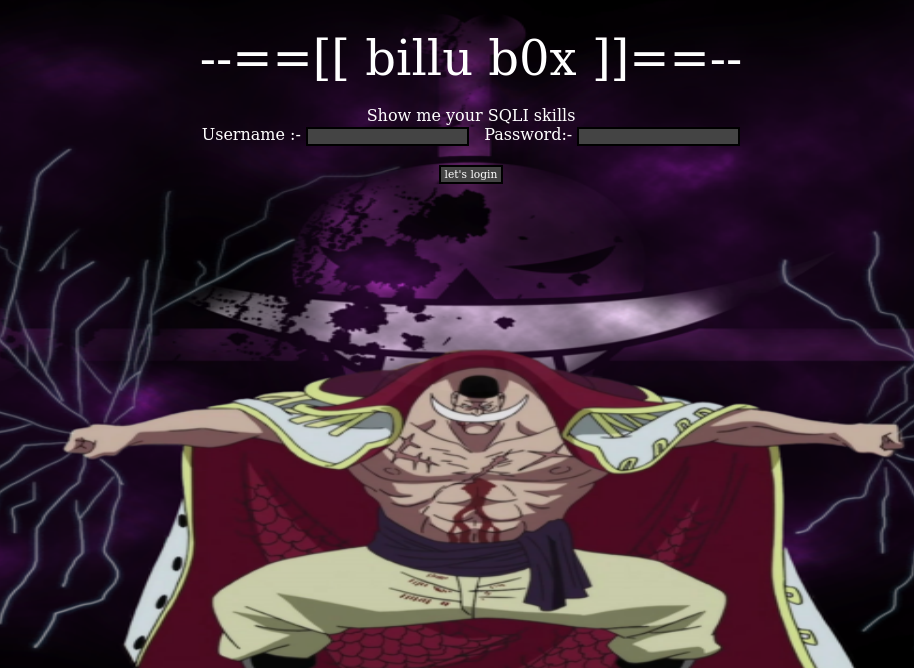
billu: b0x
This Virtual machine is using ubuntu (32 bit) Other packages used: – PHP Apache MySQL This virtual machine is having medium difficulty level with tricks. One need to break into VM using web application and from there escalate privileges to gain root access
-
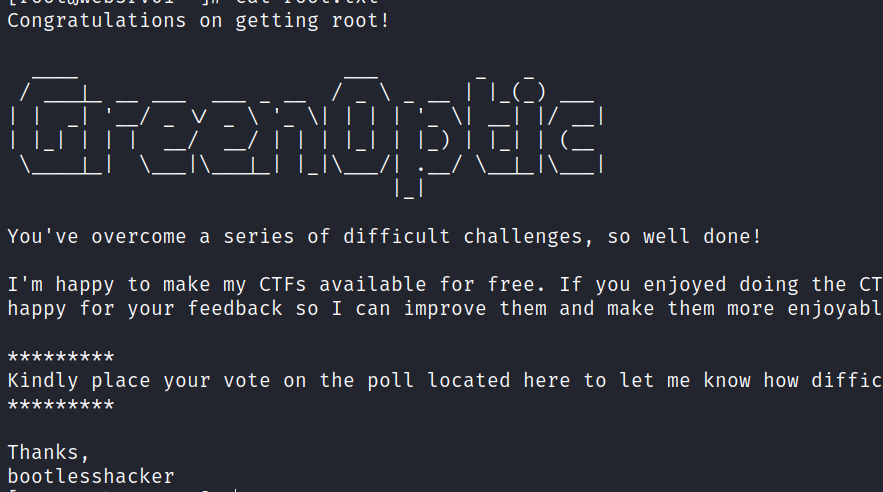
GreenOptic: 1
GreenOptic is my fourth Capture the Flag box. It is rated as ‘Very Hard’. As with all of my CTFs, please run this in ‘Host Only’ mode – it does not need an internet connection. Don’t let the difficulty put you off though – the CTF is designed to be realistic, so you won’t come…
-
doubletrouble: 1
Download the machine: https://www.vulnhub.com/entry/doubletrouble-1,743/ Overview Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 /secret Download the image and check if there are any hidden files inside the file. Let’s search searchsploit for some exploits. since we have some creds let’s use the RCE…
-
Dripping Blues: 1
Download the machine: https://www.vulnhub.com/entry/dripping-blues-1,744/ Overview Enumeration Run nmap scan to find for open ports. Check the FTP server as anonymous. Crack the password on the zip file. Read the text. Run a gobuster scan to find for hidden directories. Port 80 /robots.txt In the robots text file there is a hidden directory that looks like…
-
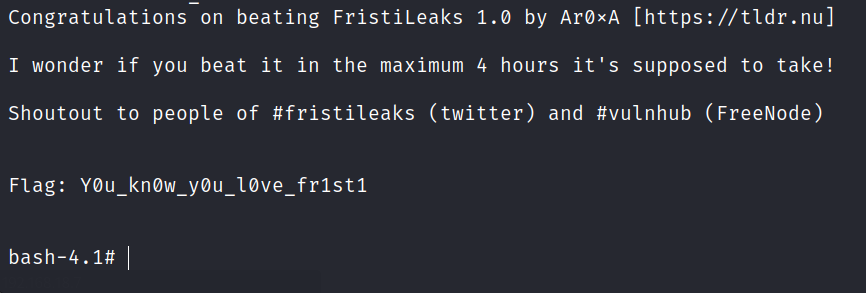
FristiLeaks: 1.3
A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, reverse engineering, etc..
-
W34kn3ss: 1
The matrix is controlling this machine, neo is trying to escape from it and take back the control on it , your goal is to help neo to gain access as a “root” to this machine , through this machine you will need to perform a hard enumration on the target and understand what is…
-
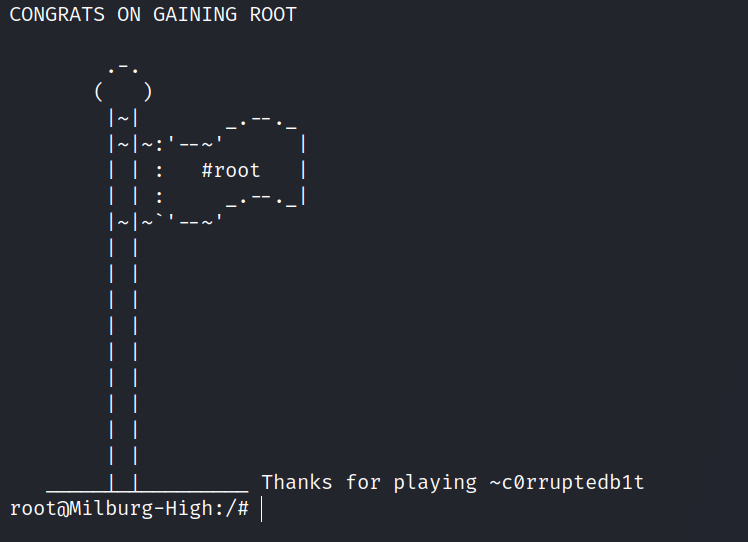
Bob: 1.0.1
The Milburg Highschool Server has just been attacked, the IT staff have taken down their windows server and are now setting up a linux server running Debian. Could there a few weak points in the new unfinished server?
-
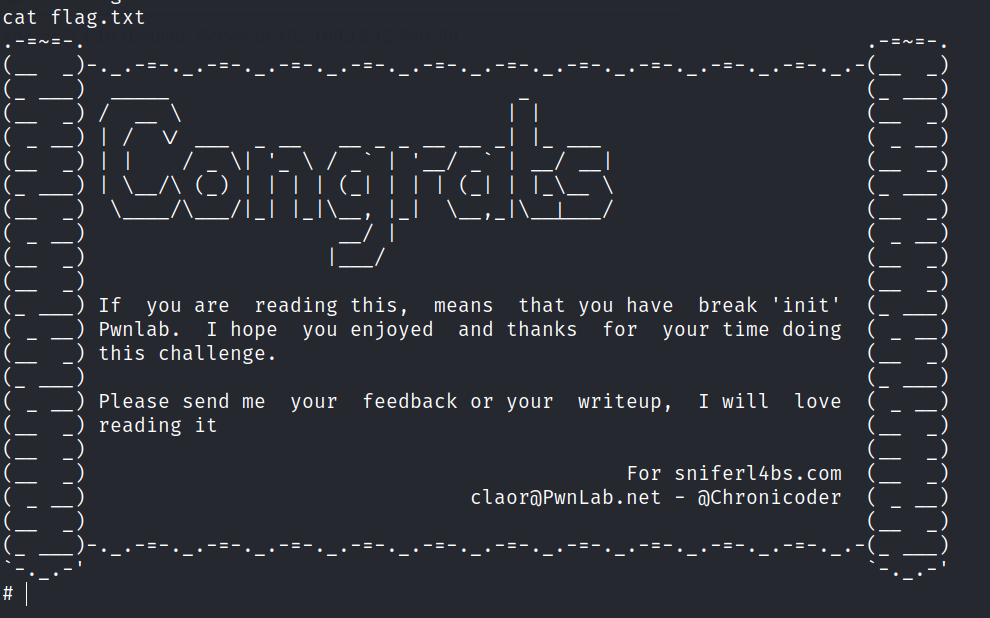
PwnLab: init
https://www.vulnhub.com/entry/pwnlab-init,158/ Review Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 Found a login page. Tried using SQL injection and bruteforcing but to no availability. In the gobuster enumeration found a config.php file , however it doesn’t show any results. After some googling I…
-

Windows Fundamentals 2
In part 2 of the Windows Fundamentals module, discover more about System Configuration, UAC Settings, Resource Monitoring, the Windows Registry and more..
-
HA: Wordy
Wordy is design for beginners to experience real life Penetration testing. This lab is completely dedicated to Web application testing and there are several vulnerabilities that should be exploited in multiple ways. Therefore, it is not only intended as a root challenge boot, the primary agenda is proactive in exploiting tops listed web application vulnerabilities.
-
Trying to learn Assembly for Reverse Engineering
I became interested in cybersecurity because I was curious about how malware creates damage. After some time of research and learning the fundamentals of computers and cybersecurity. I realize malware are like any other programs but with a malicious intent. (Yes, I took weeks to discover this) After getting my hands on Practical Malware Analysis by…
-
Born2Root: 1
https://www.vulnhub.com/entry/born2root-1,197/ Review Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 /robots.txt /wordpress-blog / icons Found a RSA key. Use the private key to SSH into the 3 users found on the homepage. It is a key for martin. Foothold After some enumeration ,…