https://www.vulnhub.com/entry/hackfest2016-quaoar,180/
Goals: This machine is intended to be doable by someone who is interested in learning computer security There are 3 flags on this machine 1. Get a shell 2. Get root access 3. There is a post exploitation flag on the box
Use netdiscover to find the IP address of the machine.

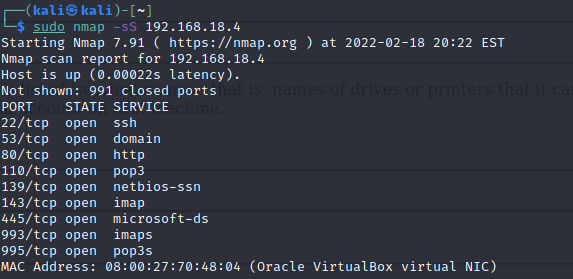
Run nmap to scan for open ports.
Run gobuster to find for directories.

Run wpscan to look for users.


Head to the wordpress site and login via Username: admin Password: admin (default)
You are able to spawn a shell by editing the theme of the site. Use a php reverse shell exploit from https://pentestmonkey.net/tools/web-shells/php-reverse-shell. *Remember to change the listening IP to your attacking machine.

Start a netcat listener and reload a page from the main wordpress site.

Spawn a python shell for a more stable shell using:
python -c 'import pty; pty.spawn("/bin/sh")'

Head to the wp-config.php to find root credentials.

su to root user.

Head to the root folder and find the first flag.

Head to wpadmin folder from the home/user to find the second flag.
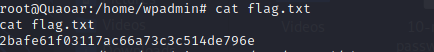
And finally head to the cron folder to find the final flag.
