https://tryhackme.com/room/reverselfiles
Tools used : Ghidra & Radare2
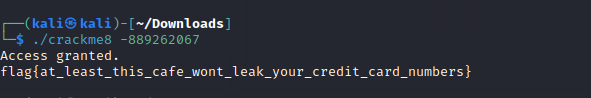
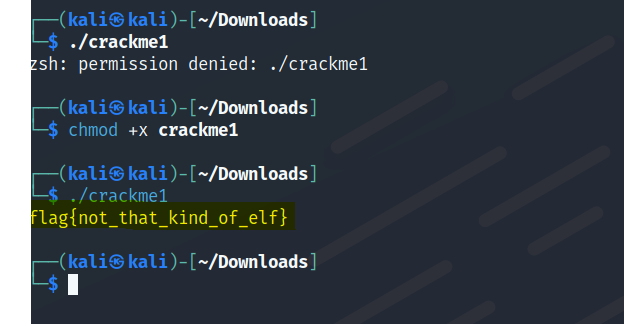
Crackme1
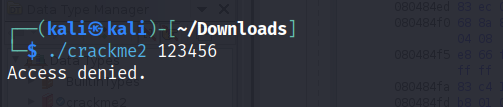
Crackme2
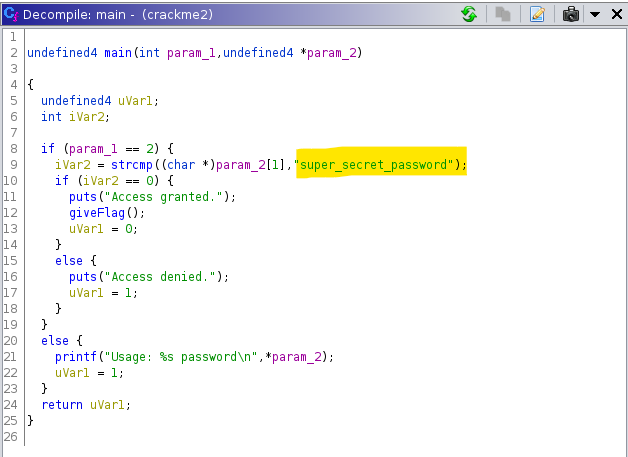
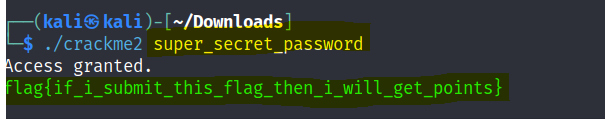
Crackme3
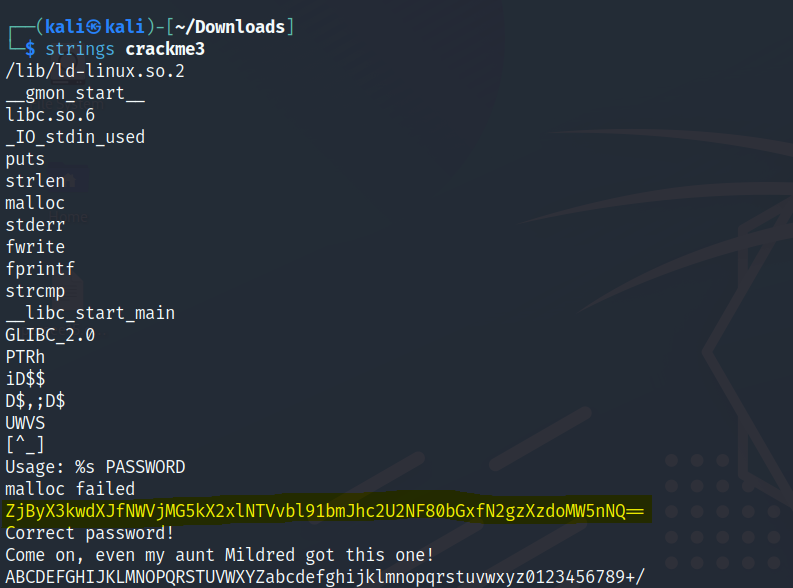
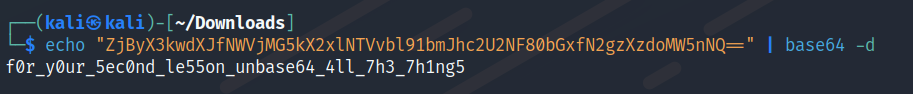
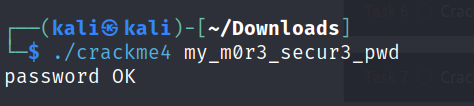
Crackme4
Analyze all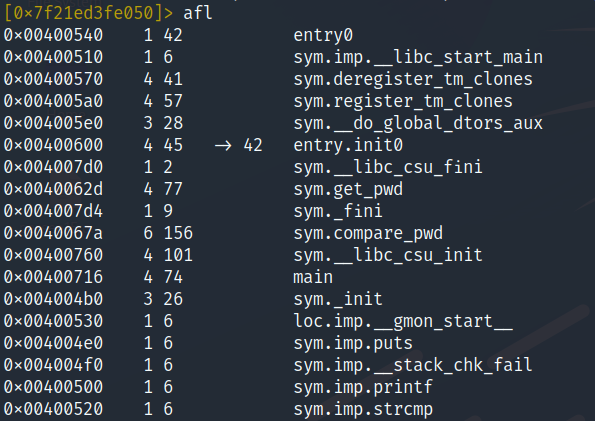
List all functions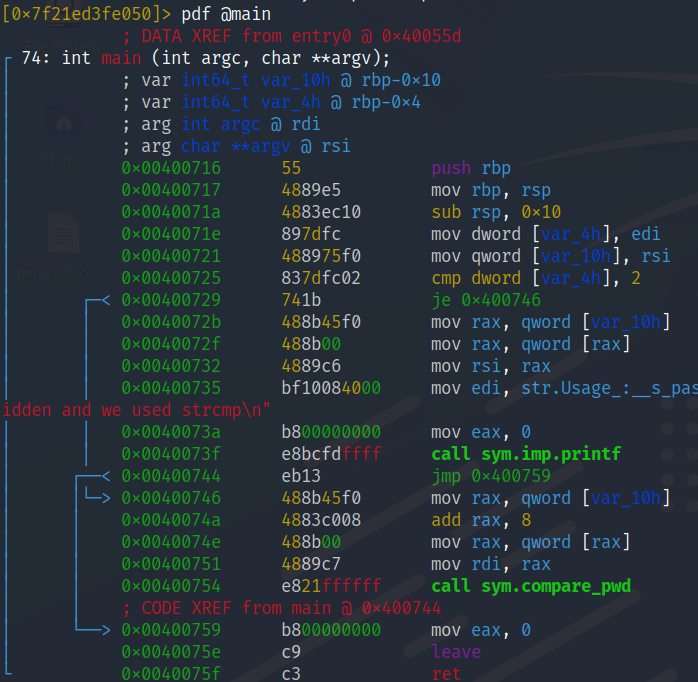
Print disassembled function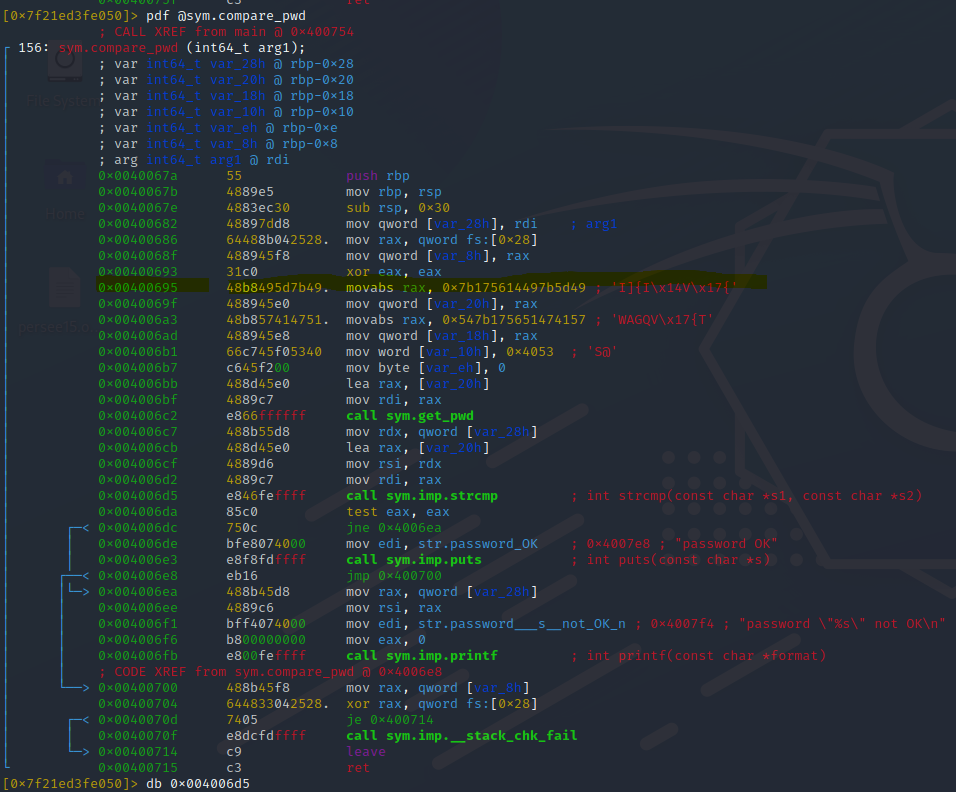
Sets a breakpoint at address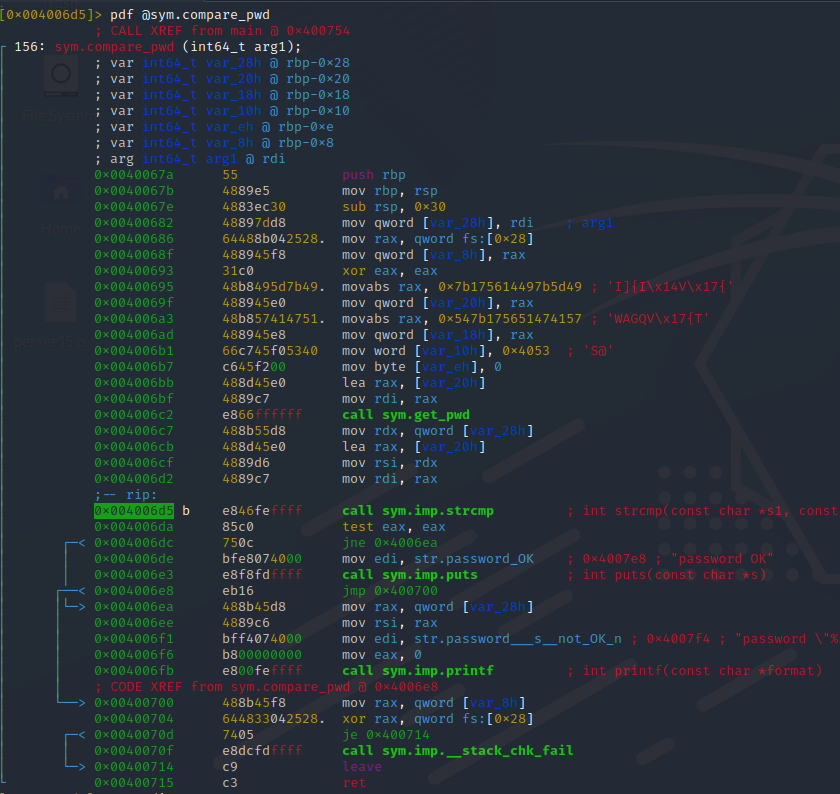
Crackme5
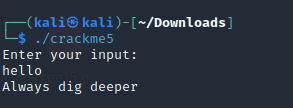
Start up radare to debug the code.
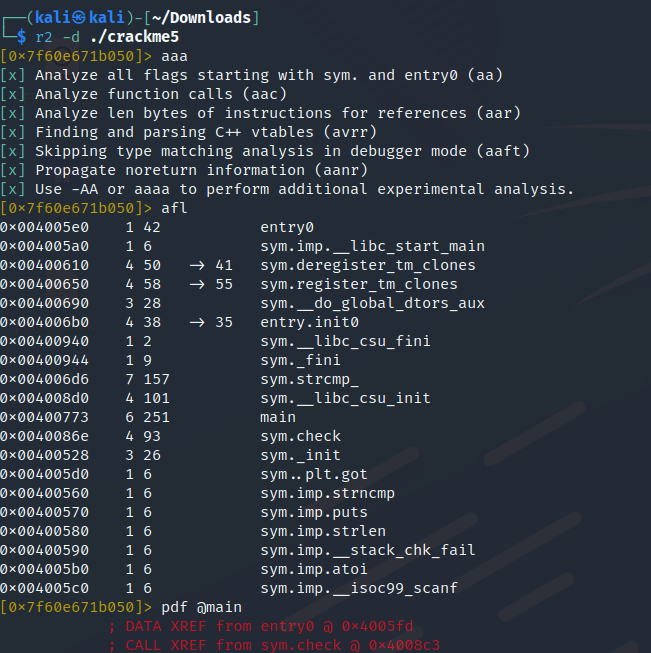
The program compares user input (scanf) and sym.strcmp_
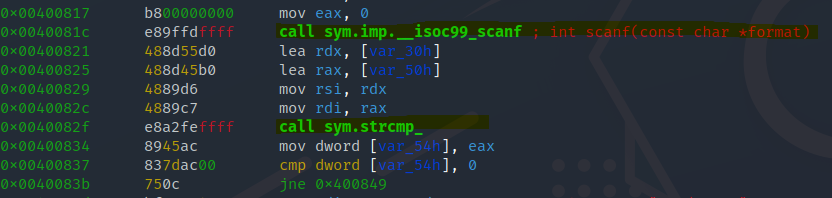
Set up a break point before the comparison at 0x00400829
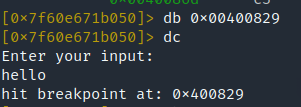
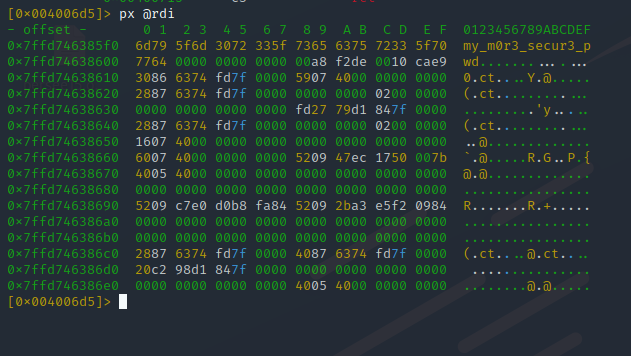
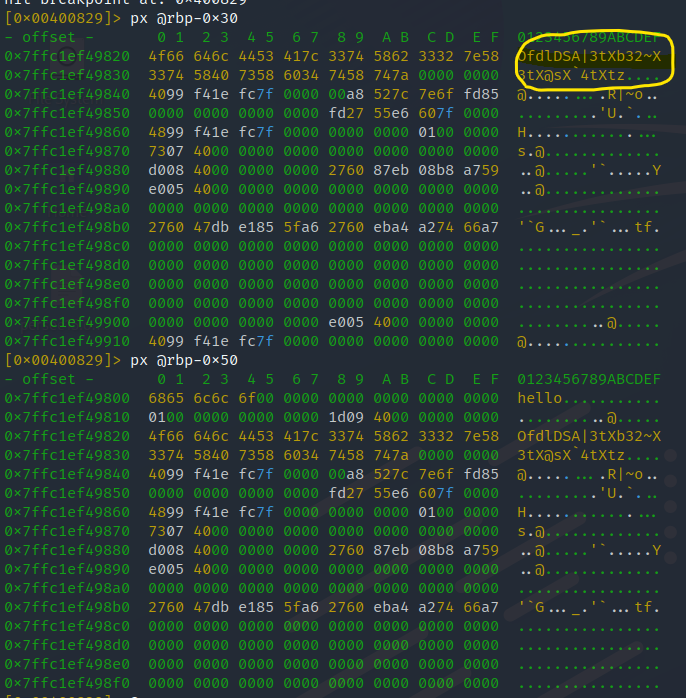
Show the hexdump on both variables one of the variables consists of the password.
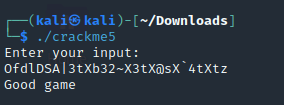
Crackme6
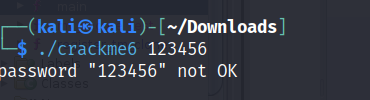
Use Ghidra to view the main function.
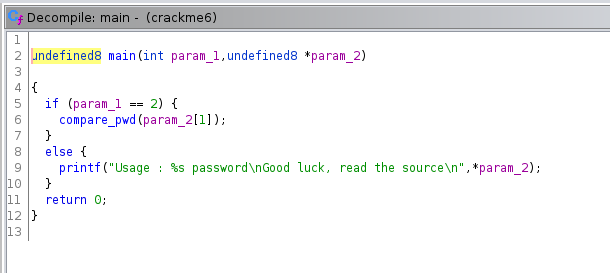
Inside the main function view the compare_pwd function.
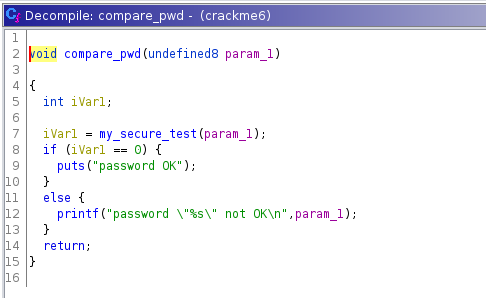
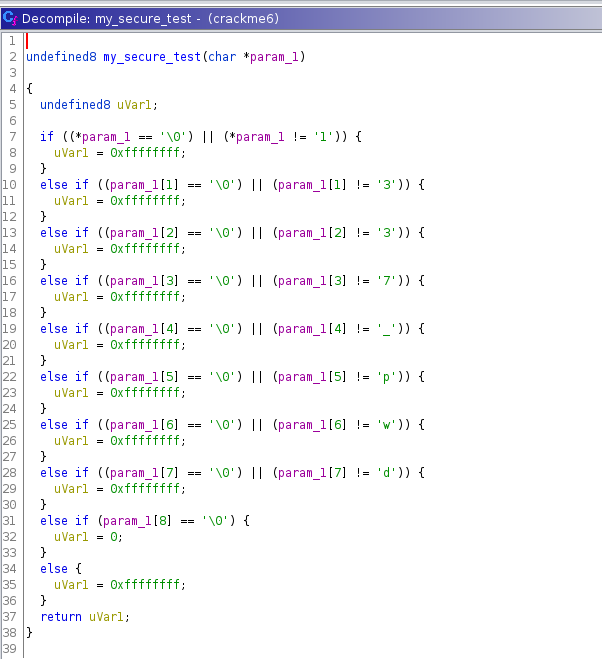
View the my_secure_test function.
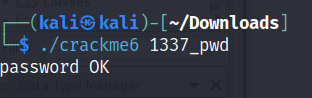
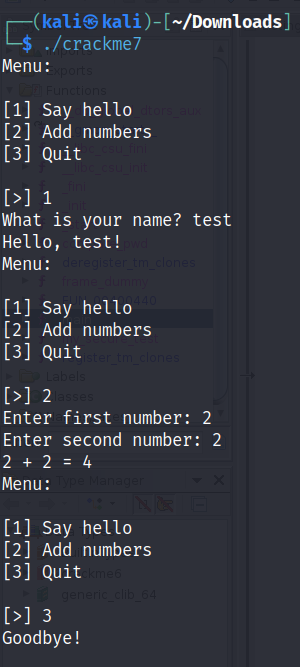
Crackme7
Using the strings command we find a unknown string.
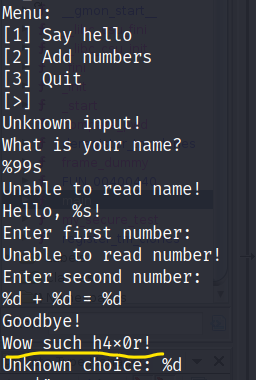
Use Ghidra to dissemble the program.
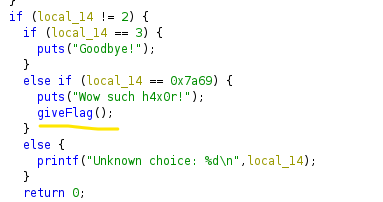
In the main function we can find an option to give the flag. Convert the hex number to decimal.
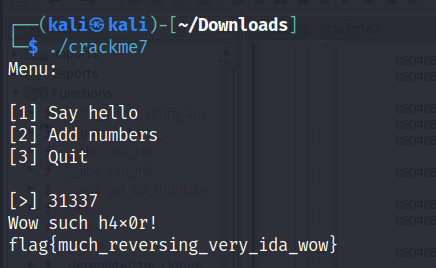
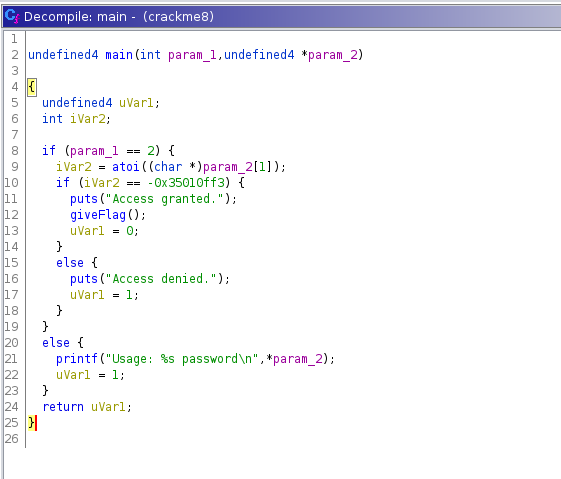
Crackme8
Start up Ghidra to examine the main function of the code.