| Instructions | Explanation |
| db | Define bytes (expressions) |
| CALL | Call a function |
| ADD | Perform an addition |
| SUB | Perform a subtraction |
| CMP | Compares two numeric data fields |
| JNZ | Jump non zero |
Reverse engineering my own programs
To start learning assembly and reverse engineering I decided to make my own simple C programs and observe the program flow through the disassemblers.
Observing basic functions
#include <stdio.h>
int variableA = 10;
int variableB = 5;
int variableC = 2;
int result;
int result_sub;
int sum()
{
result = variableA + variableB;
printf("The result for sum is %d \n ",result);
return 0;
}
int sub()
{
result_sub = variableA - variableC;
printf("The result for sub is %d ",result_sub);
return result;
}
int main() {
printf("Hello, World! \n");
sum();
sub();
return 0;
}
Dissemble in IDA Pro
main function:
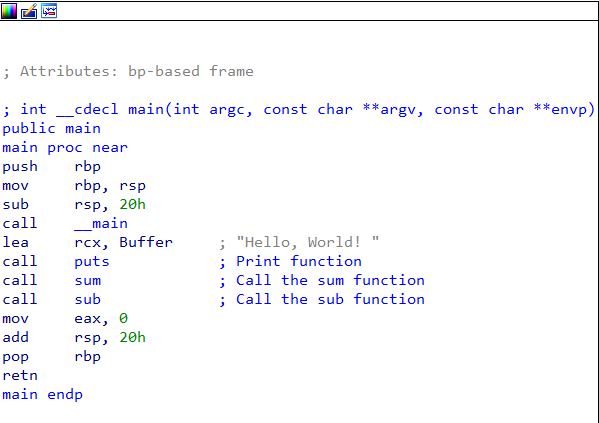
sum function:

sub function:

Password checker
#include <stdio.h>
int main()
{
int input;
int password = 5678;
printf("Please enter the password : ");
scanf("%d",&input);
if(input == password)
printf("Correct password");
else
printf("Incorrect password");
return 0;
}

- 55d = hard coded variable
- 574 = user input
- 586 = comparison with EAX (user input) and local_c (password)
- 589 = Jump non zero , If & else
Hello World
#include <stdio.h>
int main() {
printf("Hello World");
return 0;
}

Addition
#include <stdio.h>
int number1 = 5;
int number2 = 3;
int main() {
int add = number1 + number2;
printf("%d",add);
return 0;
}

User Input
#include <stdio.h>
char string;
int main() {
printf("Please enter a string : ");
scanf("%s",&string);
printf("Your string is %s" ,&string);
return 0;
}
