Download the challenge : here
Tools used :
- gdb
- ghidra
Test out the program
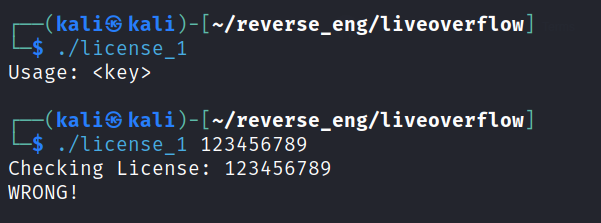
Use gdb to disassemble
Set to intel syntax and disassemble the main function.

Let’s use ghidra to color code and analyze the assembly code.
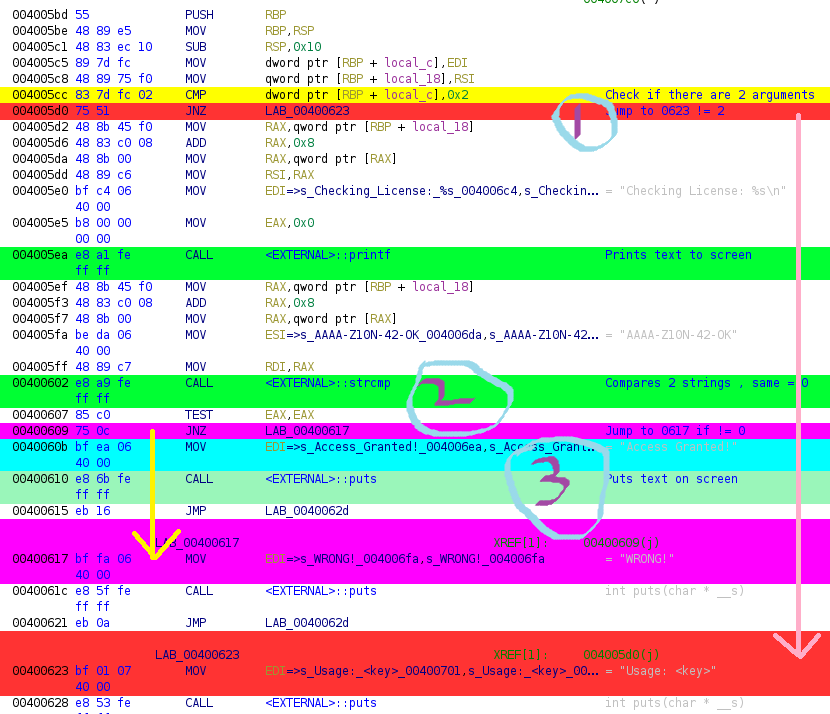
- Checks for two arguments
- Jumps to 0623 is less than 2 arguments
- strcmp user input
- jumps to 0617 if not equal to zero
- prints “Accessed Granted if user input equals to zero
Let’s head back to gdb and crack the program.
Set a breakpoint in the main function.
A breakpoint is a point where execution stops
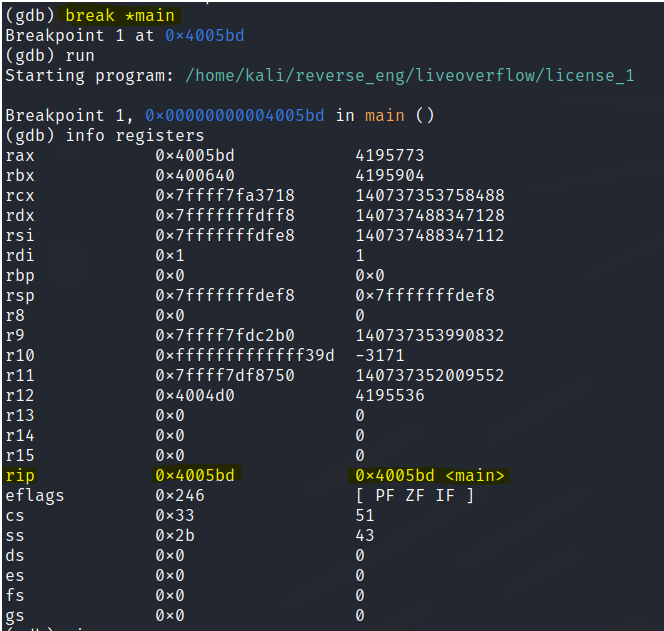
Use ni to move through the program till it ends.
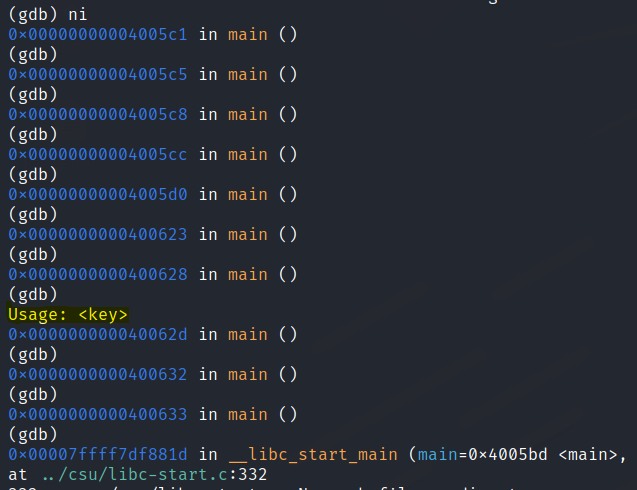
Run the program again with a random license key.
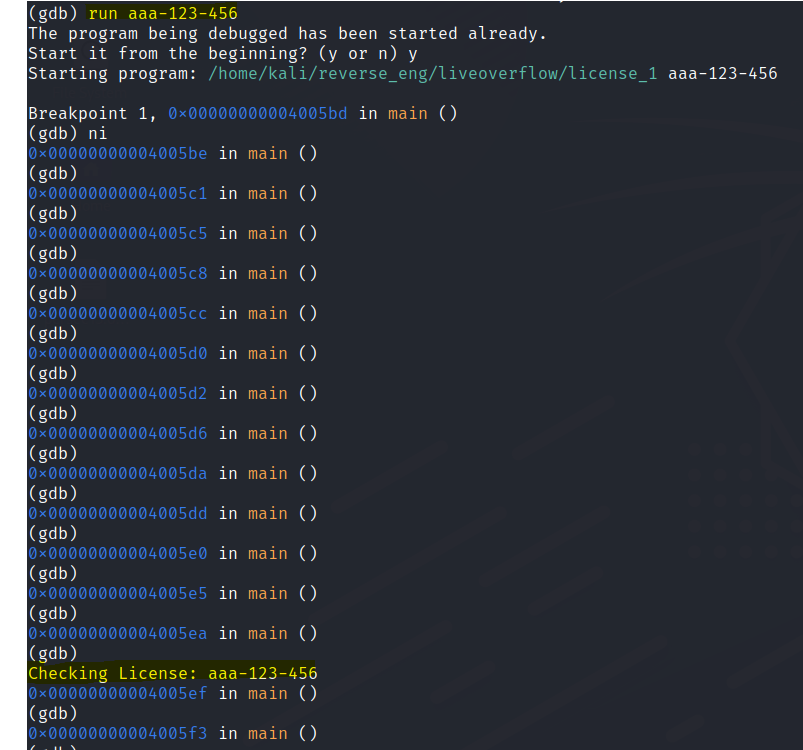
Now it compares with the user input and prints “WRONG!” if its the wrong key.

Set the 2nd breakpoint at the test line

Use info registers to check the value of rax in the test line.

Set rax to 0

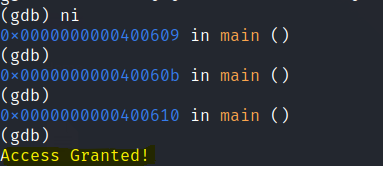
We can also see the decompiled code in ghidra.
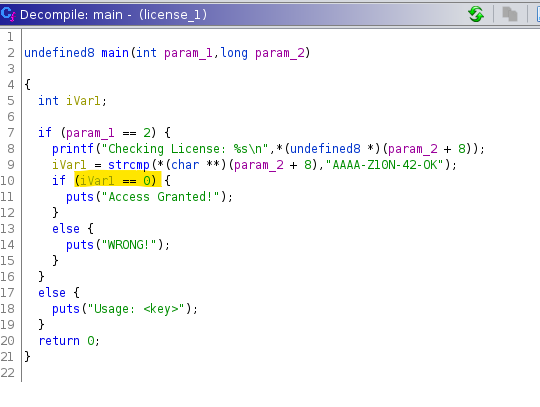
**The hard coded key can be seen in ghidra but buy using the decompiler and going through each line we can learn how a disassembler works.
