https://app.hackthebox.com/machines/Blocky
Review
- Directory enumeration leads to a folder that contains valid credentials
- phpadmin page lists users available
- Password is reusable
Enumeration
Run nmap scan to find for open ports.

Unable to login via FTP anonymously.
Run a gobuster scan

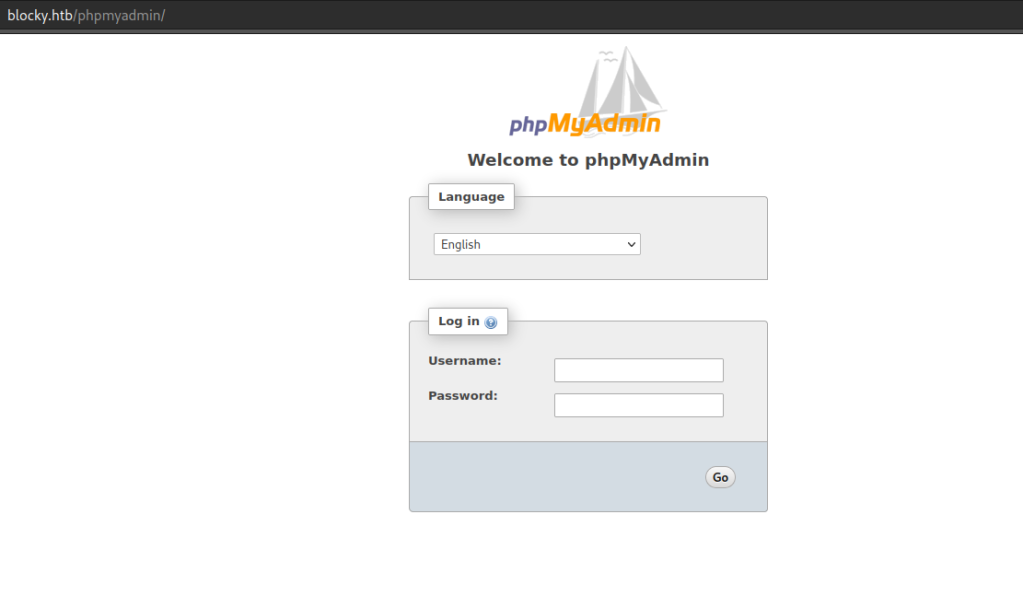
There is a phpadmin page.
Wpscan shows no results.
The plugins directory have 2 files inside.
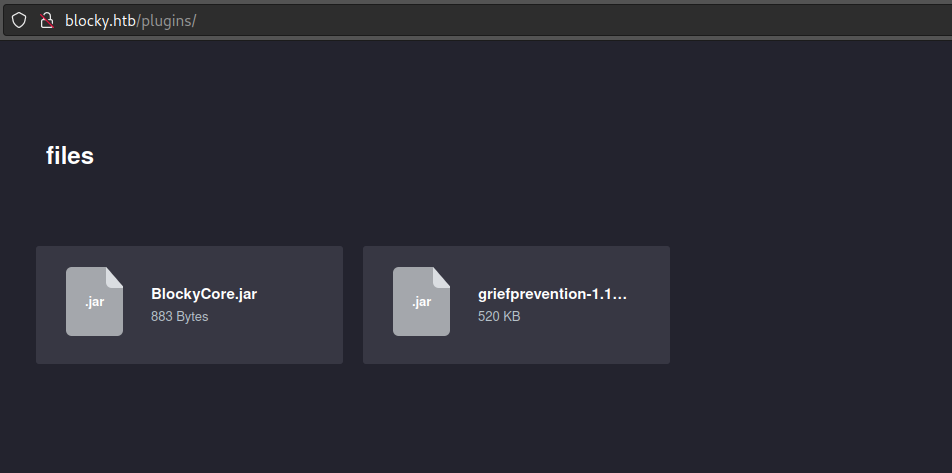
Use a java decompiler like jdi-gui to open up the file.

The 2nd file has a whole bunch of functions, let’s put this aside for now.
Let’s login with the credentials via the phpmyadmin page.

In the wordpress section page there is a credential found.

Foothold
SSH login via the user notch and the password found in the jar file.

First flag is found

Privilege escalation
Check sudo -l
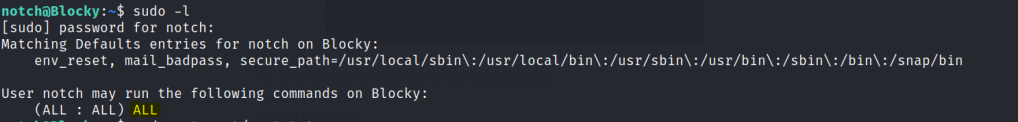
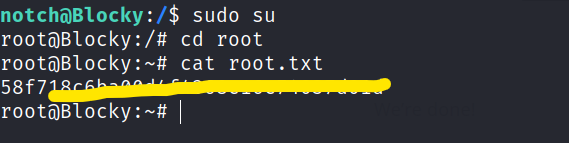
Change to root user and get the final flag.