https://app.hackthebox.com/machines/Netmon
Review
- FTP server can be accessed anonymously
- Search for default credentials for interfaces
- Basic passwords are vulnerable
- CVE-2018-9276 : An attacker who has access to the PRTG System Administrator web console with administrative privileges can exploit an OS command injection vulnerability
- PRTG Network Monitor 18.2.38 – (Authenticated) Remote Code Execution scripts creates a new administrator user for us to access
Enumeration
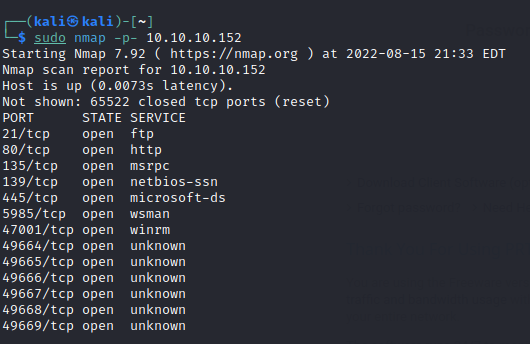
Run nmap scan to find for open ports.

Run a gobuster scan to find for hidden directories.

The webserver shows us a network monitor interface.

Google for default credentials.

Unable to login via default credentials.

Check out ftp anonymous server login.

The public folder has the user.txt file.

First flag is found.

Exploring the Users folders we find the PRTG Network Monitor config files.

Download these files and search for prtgadmin to find for any clues.

Tried it with the password but login failed. Since the password is in the old config file and has the year 2018, let’s increase to 2019.
Access gained.

Foothold
Google exploits for PRTG-Network and we can find a RCE exploit here .
Download the script to the machine.

To use the script cookies of the login page need to be included.

Run the script.

Privilege escalation
With the newly created password and user we can gain access by evil winrm.

The final flag is found.
