https://app.hackthebox.com/machines/Armageddon
Review
- Find service version through enumeration
- Metasploit exploit will give a web shell
- Databases credentials are stored openly
- Use mysqldump to dump password hashes
- Cracked hashes gives password for SSH login
- Able to run snap install without root
- Utilize dirty sock exploit to create an account and switch to root user without password
Enumeration
Run nmap scan to find for open ports.

Port 80 brings us to some type of login page.

Run a gobuster scan to find for hidden directories.

ReadME.txt tells us it runs a Drupal source content management platform

In the profiles folders there are files that contain the Drupal version.
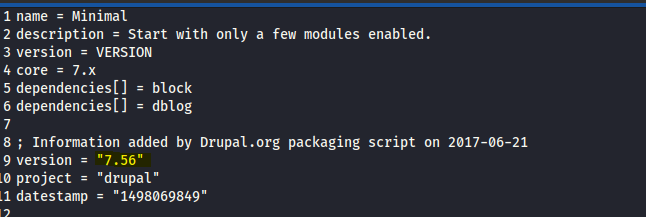
Use searchsploit to find for known exploits.

**There was an issue running the ruby script on my system so I decided to use metasploit instead.


Foothold
Once the shell is gained , a user name is found.

Enumerating the folders , we can find some database credentials in /var/www/html/sites/default/settings.php

Let’s use mysqldump to dump everything.


Let’s crack the hash with John the ripper.

Login to the user via ssh.

First flag is found

We are able to run the snap install with sudo and no password.

Searching GTFOBins we get the following.

We can also use a faster approach with dirtysock here
In the script we can use this payload.

Privilege escalation
Run the following commands in python.


Once dirty sock is installed it creates a user call dirty sock with the same password.
With this installed we are able to switch to the root user.

Root flag is found.
