https://www.vulnhub.com/entry/infosec-prep-oscp,508/
Review
- Find hidden directories on web server
- Decrypt clues with base64
- Edit files to gain information needed
Enumeration
Run nmap scan to find for open ports.



Run a gobuster scan to find for hidden directories.

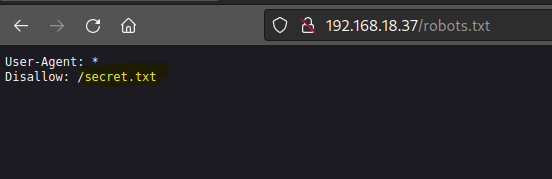
Found a base64 script

Use cyberchef to decode the base64 code and it is a RSA key.

Foothold
SSH into oscp user with the RSA key
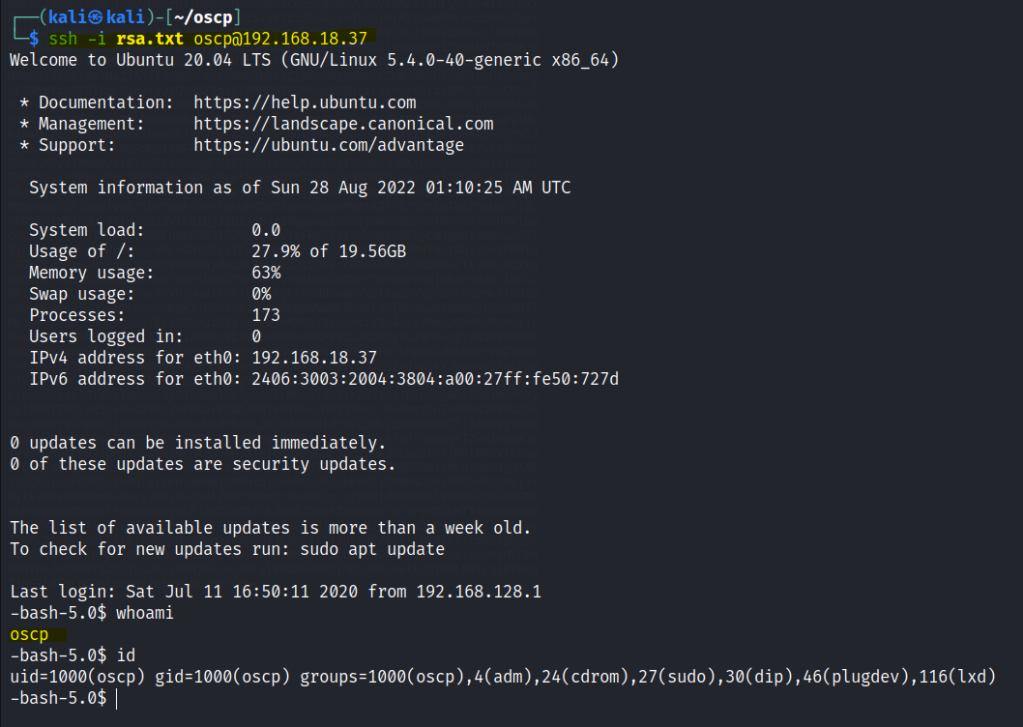


Let’s edit the file and list out the root folder in a ls.txt file. Chmod the file to view it. Restart the machine.

Edit the ip file script again to cat the flag.txt file.

Flag is found

Privilege escalation
Even though the flag is found we can gain root access with the following.

