https://app.letsdefend.io/challenge/remote-working/
Analysis XLS File
File link: https://app.letsdefend.io/download/downloadfile/ORDER_SHEET_SPEC.zip/
Password: infected
NOTE: Do not open on your local environment. It is malicious file.
Tools :
VirusTotal.com
This malware contains a XLS file. We can upload the file into VirusTotal to examine some details.
Question 1
What is the date the file was created?
The History section of the Details tab will indicate the creation time of the malware.

Question 2
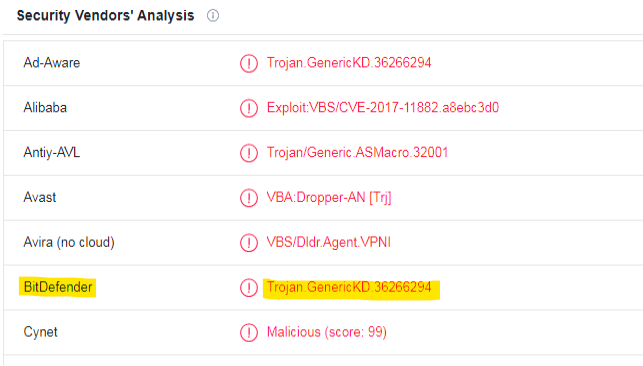
With what name is the file detected by Bitdefender antivirus?
The numerous Security vendor’s analysis can be seen in the the Detection tab.
Question 3
How many files are dropped on the disk?
Dropped files can be seen in the Relations tab.

Question 4
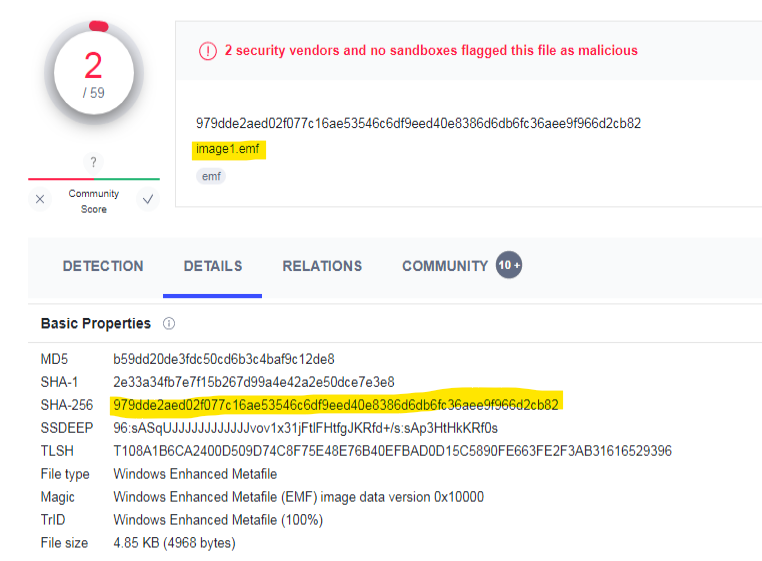
What is the sha-256 hash of the file with emf extension it drops?
Find the file that contains the .emf extension and click on the link.

It contains another analysis and the SHA-256 hash can be seen in the Details tab.
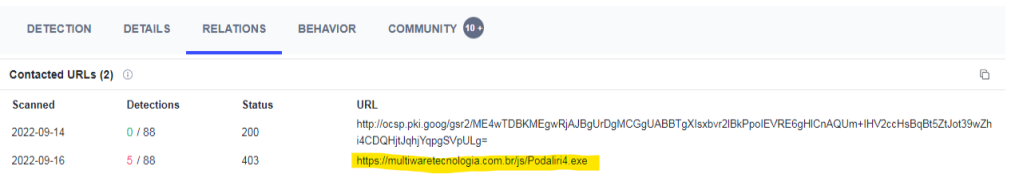
Question 5
What is the exact url to which the relevant file goes to download spyware?
In the Relations tab we can examine the Contacted URLs. From the list we can see the URL the malware goes to download the spyware.