- Name: Dina: 1.0.1
- Date release: 17 Oct 2017
- Author: Touhid Shaikh
- Series: Dina
Download the machine:
https://www.vulnhub.com/entry/dina-101,200/
Overview
- Enumeration will lead to robots text and and a directory that was not indicated in robots.txt
- Check the source code of a directory to find creds
- Download a backup folder from one of the directory
- Upload the unzipped audio file in CyberChef to find the text file
- Head to secret directory and gain access from a password list
- Login to the playsms interface
- Use metasploit to gain a shell
Enumeration
Run nmap scan to find for open ports.

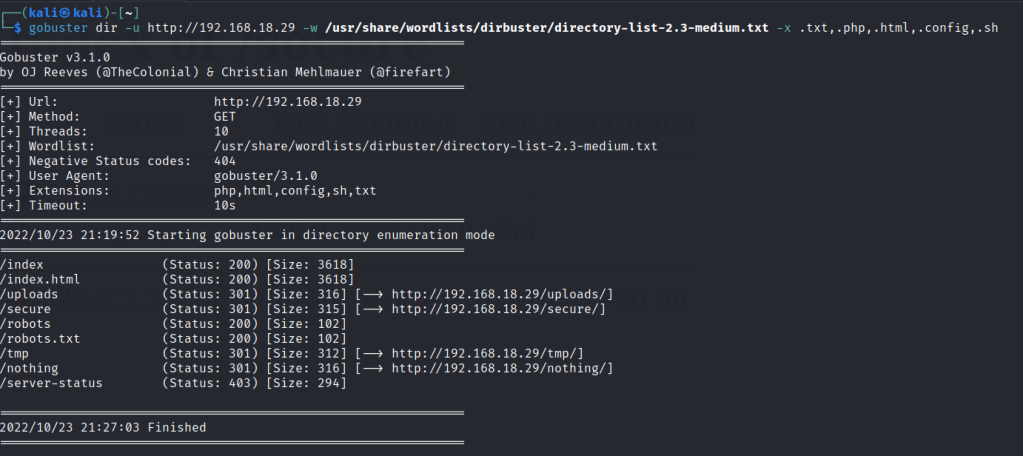
Run a gobuster scan to find for hidden directories.
Port 80

/robots.txt

/nothing source code.

/secure

Unzip the file with the password list and a mp3 file is given.

Use cyberchef to read the file.

Now we found an interface.

We can use the password list again gain access.

Foothold
There are some exploits found on metasploit.

Set up the necessary options.

Run the exploit and a shell will be gained.

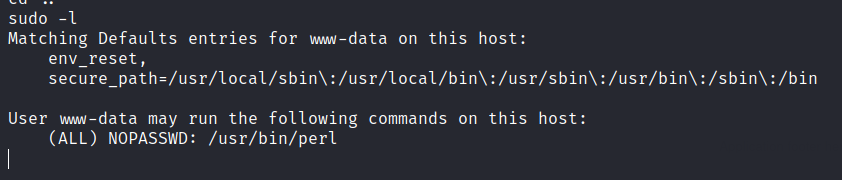
Check for sudo permissions.
Privilege escalation
Use GTFOBins to find for a perl sudo exploit.

Root access is gained and flag is found.
