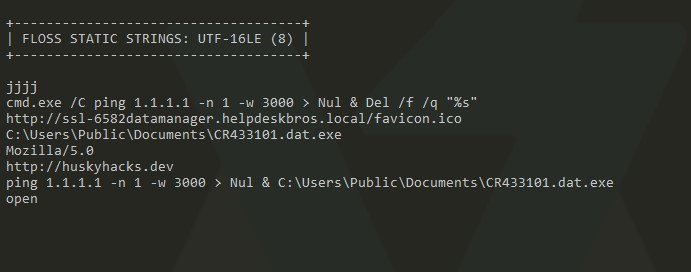
Strings extraction is the process of finding and extracting printable and meaningful sequences of characters from a file. This can be used to identify the functionality of a malicious file, as well as indicators of compromise (IOCs).
The most common tool for extracting strings is Sysinternals’ Strings. FLOSS from FireEye can also be used to automatically detect, extract, and decode obfuscated strings. It can extract all major string types.
FLOSS can be run with the -n argument to specify a minimum string length. This is useful because longer strings can be more informative to analysts than shorter strings. For example, a string of length 4 is unlikely to contain any meaningful information, but a string of length 20 or more may contain a filename, domain name, or other useful information.

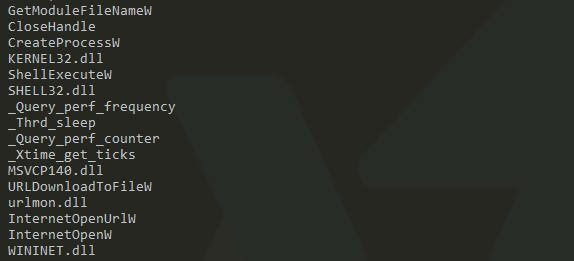
Lookout for functions.
Take note of the decoded strings, it might lead to some clues on how the malware is acting.