Link to the ctf : https://tryhackme.com/room/ctf
Using nmap, scan this machine. What ports are open?
Start with a nmap scan to find for open ports.
4 ports are open
Using Google, can you find any public information about them?
Search in google for FowSniff and a Twitter account is found.

Scroll the posts and this is found.
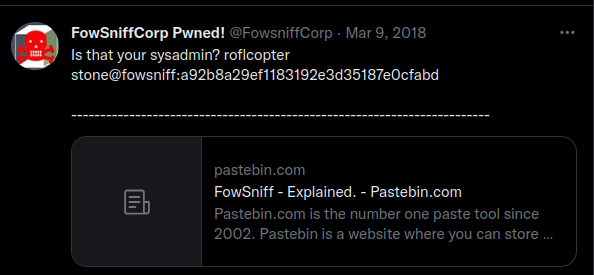
Can you decode these md5 hashes? You can even use sites like hashkiller to decode them.
Head to https://pastebin.com/NrAqVeeX to find users and md5 hashes.

Head to https://hashes.com/en/decrypt/hash to decrypt the md5 hashes.

Save the users in one file.

And the cracked passwords in anther file.

Using the usernames and passwords you captured, can you use metasploit to brute force the pop3 login?
Start up msfconsole and search for pop3 and use the third exploit.
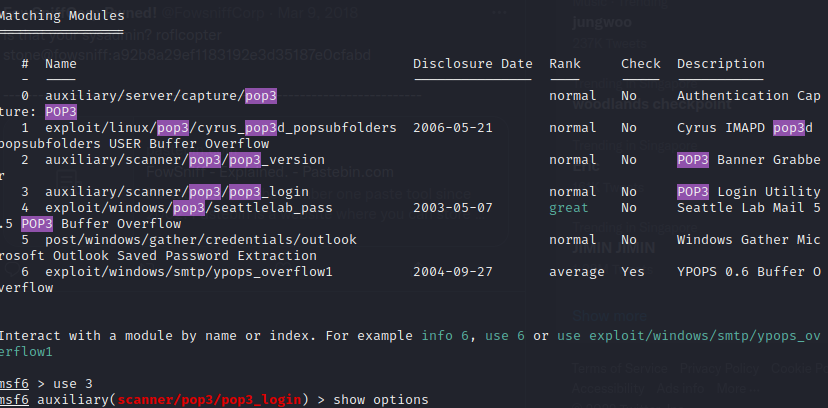
Set the RHOSTS , USERS FILE and PASSWORD FILE and run the exploit.
What was seina’s password to the email service?

Can you connect to the pop3 service with her credentials? What email information can you gather?
start a netcat listener to the box with port 110.

Looking through her emails, what was a temporary password set for her?
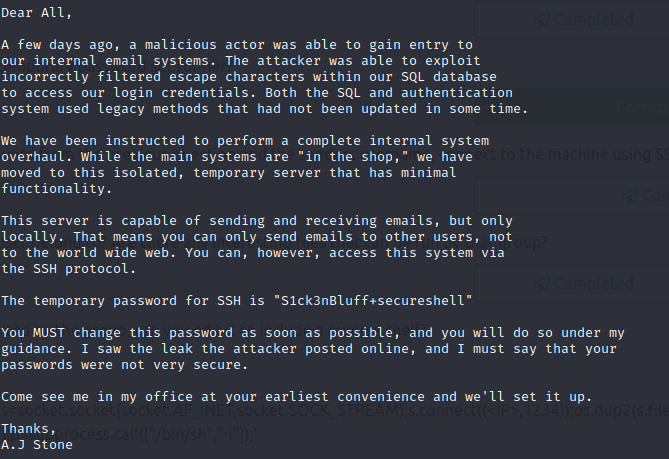
In the email, who send it? Using the password from the previous question and the senders username, connect to the machine using SSH.


Once connected, what groups does this user belong to? Are there any interesting files that can be run by that group?

nano cube.sh and paste the python reverse shell script. Change the IP address to your attacking machine IP

Exit the ssh , start a netcat listener and login to the ssh user again


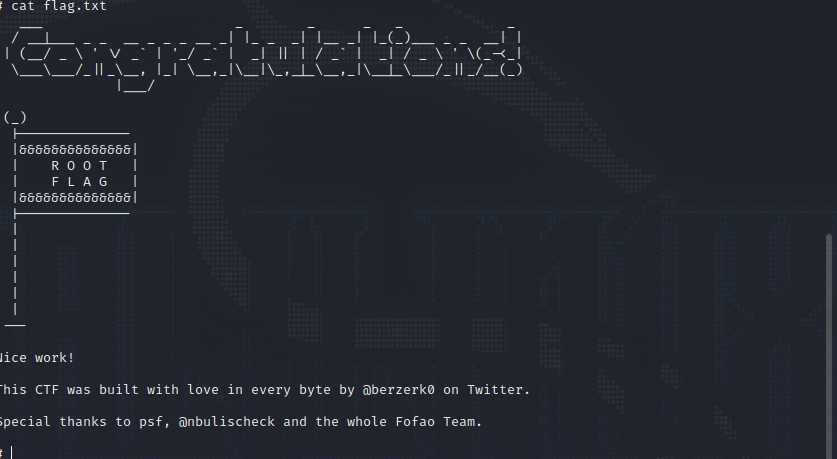
Cat the flag.txt to get the final flag.